(Updated April 30, 2019 with new data from an even larger attack. Skip directly to the bottom to learn more.)
DDoS attacks are usually measured by the amount of bandwidth involved, such as the 1.35 Terabits per second (maximum) attack directed at GitHub last year, the largest DDoS attack ever at the time.
However, in DDoS attack mitigation, it’s not the amount of bandwidth that matters – it’s the absolute number of packets directed at a network or web site. Packets per second is the true measure of the attack intensity, and that is what is difficult to block and recover from.
In January 2019, Imperva’s DDoS Protection Service mitigated a DDoS attack against one of our clients which crossed the 500 million packets per second (Mpps) mark. That’s more than four times the volume of packets sent at GitHub last year and we believe at the time was the largest PPS attack publicly disclosed (see bottom of post to learn about a recent even larger attack we recorded).
How DDoS Attacks Work
DDoS attacks aim to deplete compute or network resources. When that happens, the service becomes unavailable and an outage occurs. Network resources can be broken down into two categories: capacity and infrastructure.
Network Capacity
Depleting network capacity is fairly easy to achieve. A DDoS attack can be launched within a matter of minutes (just google for stressers or booters) and overwhelm the vast majority of websites or enterprise networks.
Avoiding network pipe congestion requires significant network capacity, which is not a cost-effective strategy for the average business. That’s where DDoS mitigation services come into play.
DDoS mitigation/protection service providers tend to provision network bandwidth far greater than the largest observed DDoS attack, making the sheer volume of the attack a non-issue. Since the DDoS capacity is shared between numerous customers, economy of scale becomes the basis for their operational and financial model.
Network Infrastructure
Once we have passed the network capacity barrier, there is still a ton of traffic to be processed. In the case of DDoS mitigation services, these would be the switches, routers, and mitigation appliances. Network appliances mostly evaluate the headers of the packets (every packet!) and rarely inspect the full payload. Their limiting factor is the packet rate, not the packet size.
For mitigation appliances, the PPS challenge is even greater because mitigation is performed using a wide variety of techniques. This requires far more compute processing power than what traditional network appliances require to route or switch a packet.
For a DDoS protection or mitigation service, mitigating a high PPS attack can be its Achilles heel, while a bandwidth-intensive attack can be much easier to handle, even with hundreds of gigabits per second, if it is composed of a smaller number of large-sized packets.
Using PPS Data to Analyze the Github Attack
At 1.35 Terabits per second, the widely-publicized attack on GitHub in 2018 was considered the largest DDoS attack ever at the time. However, how complex was it to mitigate?
The attack was a memcached amplification attack. Amplification attacks use a compromised server to bounce traffic to the attacked server. In other words, a packet of N bytes will be bounced to the attacked server as a packet of size N times the “amplification factor.”
Popular vectors such as NTP and DNS have an amplification factor of up to 556.9 and 54, respectively. Memcached has a whopping amplification factor of up to 51,000, which means:
- The generated attack mainly consists of large packets and a relatively low PPS rate. The GItHub report indeed confirms a peak of 129.6 million packets per second.
- The source port of each of the packets was identical (port 11211), as they all came from the same service (on different servers).
Put these two together, and the attack no longer looks so challenging: since the PPS volume is relatively low, a mitigation appliance could be used. Alternatively, it could be a perfect candidate for traffic filtering (i.e. Access Control List), which blocks any packet whose source port is set to 11211. ACLs are available on any switching appliance, which makes it a less sophisticated, but effective option.
Fast Forward to 2019
At Imperva, we are currently seeing DDoS attacks over 500 Gbps on a weekly basis:
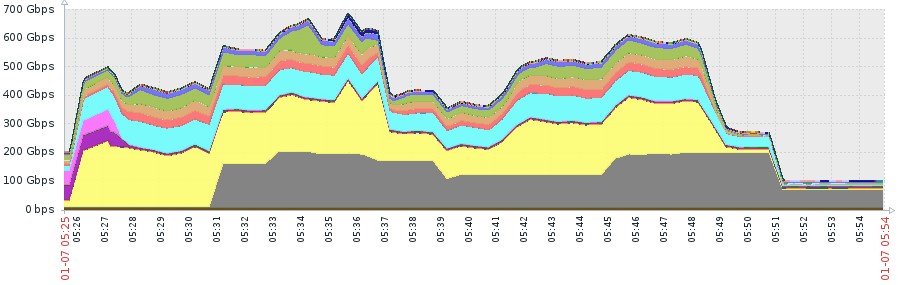
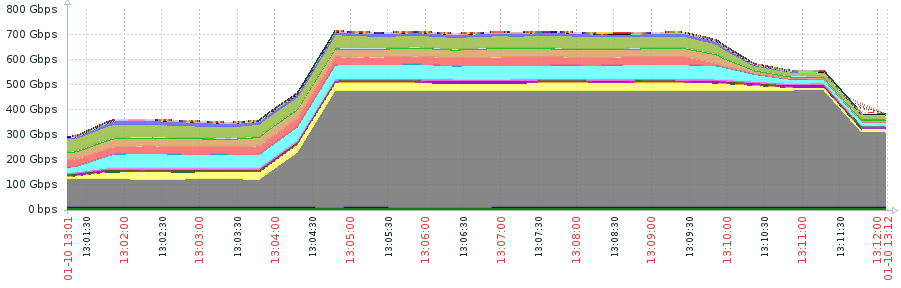
While these huge attacks are the largest by bandwidth mitigated by Imperva to date, that wasn’t what made it a potential challenge. Rather, it was the 500 million packets-per-second torrent directed at our customer – the highest volume ever recorded – that made it so intense, and the real challenge to overcome.
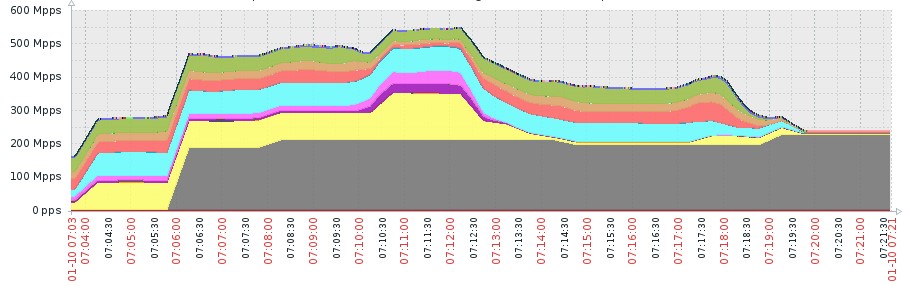
The Jan. 10 attack was a syn flood augmented by a large syn flood (packets of 800-900 bytes). The source ports and addresses of the traffic sent to our customer’s server were highly randomized and probably spoofed. Fortunately for us and the client, the attack was mitigated automatically, with no humans involved.
When we investigated, we realized the attack wasn’t generated using new tools, but two common older ones: one for the syn attack and the other for the large syn attack. Although both tools try to mimic legitimate operating systems, there are some odd, suspicion-raising differences. One tool randomizes various parameters but accidentally malforms the packet. The other tool uses a legitimate, almost identical packet, for the entire attack. One possible hypothesis is that these tools, although used in the same attack, were written by two different individuals and then combined to form an arsenal and launch the most intensive DDoS attack against Network infrastructure in the history of the Internet.
On April 30th, 2019, we recorded an even larger-by-PPS-volume attack against one of our clients. This attack peaked at 580 million packets per second. Using our new common mitigation state (CMS) feature, our DDoS Protection service was able to escalate and mitigate this attack even faster.
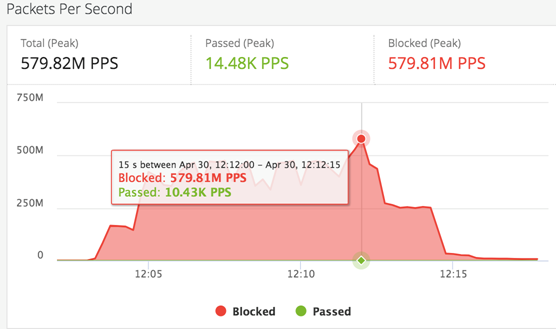 When it comes to DDoS protection, bandwidth is not everything. The most demanding attacks are high-volume PPS attacks, because with more packets to process, you need more network hardware and other resources to mitigate them.
When it comes to DDoS protection, bandwidth is not everything. The most demanding attacks are high-volume PPS attacks, because with more packets to process, you need more network hardware and other resources to mitigate them.
Check out the behemoth 2 blog for a deeper dive of how our technology protects against high-volume PPS attacks, or visit our website’s resource section to learn more about Imperva DDoS Protection.
Try Imperva for Free
Protect your business for 30 days on Imperva.











