Web application firewalls (WAFs) are hardware and software solutions that protect websites from application security threats. They examine incoming traffic to block attack attempts, thereby compensating for any code sanitization deficiencies.
By securing your data from theft and manipulation, WAF deployment meets a key criterion for PCI DSS certification. Requirement 6.6 states that all credit and debit cardholder data held in a database must be protected. (Read more on Incapsula PCI DSS compliance here.)
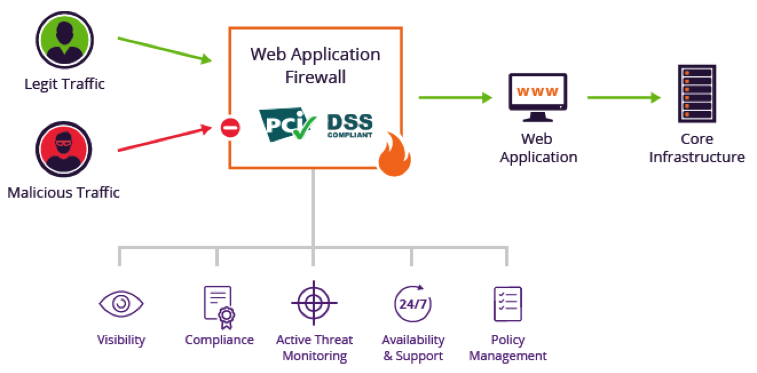
Deploying a WAF generally doesn’t require making any changes to an application, for it’s placed at the edge of a network. From there it functions as a gateway for all incoming traffic, blocking malicious traffic requests before they’re able to interact with your application(s).
WAFs use several different heuristics to determine which traffic is given application access and which need to be blocked. A continually-updated signature pool can enable a WAF to instantly ID bad actors and known attack vectors.
Almost all WAFs can be custom-configured for specific use cases and security policies, as well as to combat emerging (a.k.a., zero-day) threats. Most modern solutions leverage reputational and behavioral data to gain additional insights into incoming traffic.
WAFs are typically integrated with other security solutions to form a security perimeter. These may include distributed denial of service (DDoS) protection services that provide additional scalability required to block high-volume attacks.
The following are six important terms you should know as you prepare to deploy a WAF.
ACL
An access control list (ACL) is a table that identifies to your network control system those IP addresses which should always have authorized access as well as those that should forever be blocked. For example, Imperva Incapsula published a list of “good” bots that ensure that that your site gets the Internet traffic it deserves; these should all be whitelisted in your ACL.
The Incapsula WAF blocks bots it has determined to be suspicious. But you may be keeping your own list of additional IPs, such as those belonging to a competitor, you don’t want to ever have access to your website. The ACL is accessed through the Incapsula Dashboard where you are able to purposely blacklist these addresses.
For examples of how to do this, read Banishing Bad Bots with Incapsula.
DDoS
Every day, distributed denial of service (DDoS) attacks actively cripple organizations by damaging their operations, bottom lines and reputations. Launched from numerous compromised devices—often globally distributed in what is referred to as a botnet—a DDoS attack is a malicious attempt to make an online service unavailable to users, usually by temporarily interrupting or suspending the services of its hosting server.
DDoS protection service is built on top of the Incapsula enterprise-grade, PCI-certified web application firewall—the only leader cited for the third year in a row in Gartner’s 2016 Magic Quadrant for Web Application Firewalls. It provides automatic detection and mitigation of all types of DDoS attacks launched at websites and web applications—targeting the OSI application, protocol and network layers. It blocks attacks seeking to target DNS servers while providing blanket infrastructure protection for all types of services (UDP/TCP, SMTP, FTP, SSH, VoIP and others.)
Incapsula DDoS protection is conceptually based on a set of concentric rings around an application, each of which filters a different traffic portion. By themselves each ring can be bypassed, but by working in unison they stop almost all malicious traffic. Some DDoS attempts are blocked at the outer rings, while persistent multi-vector assaults require the use of all (or most) of them.
Visit our DDoS Knowledge Center to learn more about the various types of DDoS attacks.
Client Classification
Inspecting HTTP headers is a very effective way to gain valuable insight into site visitors. It offers various clues to as whether each is human or automated (i.e., a scripted bot), and whether or not the latter is suspicious. Because IP headers can be faked, they should never be the sole criterion for making a blocking decision. Instead this data should be combined with additional criteria to make a more informed determination.
For Incapsula, IP and ASN verification comes next. We evaluate several items, including whether the identity of the IP and ASN owners match with the site visitor. This can be used to identify illicit/malicious bots posing as legitimate ones. For example, if a visitor claims to a benevolent Googlebot, but neither the IPs nor the ASN match those used by Google, it’s a telltale sign that it’s likely a dangerous impostor.

The WAF next uses modeling to analyze visitor behavior and requests made. It’s another opportunity to flag or block suspicious bots. If behavior is indicative of automation, Incapsula also tracks items such as the order or rate of requests, irregular browsing patterns, and abnormal interaction between clients and servers. All of this data is then fed into our classification engine.
But advanced client classification doesn’t stop there. The WAF also uses IP reputation and fingerprinting to quickly filter out bad bots. A form of crowd sourcing enables disparate websites across the entire Incapsula community to actively participate in their own security, thereby benefitting the whole. You can read more about our global client classification process here.
XSS
Cross-site scripting (XSS) is a common web attack vector that injects malicious code into a vulnerable web application. It differs from other vectors (e.g., SQL injections) as it doesn’t directly target the application itself. Instead, users of the web application are those at risk.
A successful XSS attempt can have devastating consequences for an online business’s reputation and its client relationship.
Depending on the severity of an attack, user accounts may be compromised, Trojan horse programs activated and page content modified—misleading users into willingly offering their private data. Session cookies could also be revealed, enabling a perpetrator to impersonate valid users and abuse their private accounts.
Cross-site scripting attacks can be broken down into two types: stored and reflected. You can read more about the differences within the Threat Glossary included in our Knowledge Center.
In addition to XSS, Incapsula WAF protects against the most critical application security risks, such as SQL injection, illegal resource access, remote file inclusion and other OWASP Top 10 threats.
Security logs vs. Access Logs
Security logs give you visibility into suspicious activity and access logs (weblogs) a full view of traffic from users to your servers. Your WAF vendor may present security and access logs in a different manner. Incapsula offers security logs for Enterprise customers and access logs via SIEM integration.
Incapsula security logs provide a detailed alert for each suspicious event on your network that’s detected by the Incapsula proxy throughout its globally distributed network. All logs include the account ID and site ID references which let you drill down into each individual customer/site.
Incapsula access logs specify every request and response sent between your customers and the Incapsula proxy. This represents all the traffic that would have been sent between end users and your origin server, including traffic that Incapsula serves from its cache.
Conclusion
A strong WAF will protect your websites and your digital assets. With the right configuration that meets your organization’s needs, it can be both hardened without compromising user experience. Are there any other terms you’d like to know more about? Drop us a comment. We’d love to hear from you.
Try Imperva for Free
Protect your business for 30 days on Imperva.













