This guide gives step-by-step guidance on how to collect and parse Imperva Cloud Web Application Firewall (WAF, formerly Incapsula) logs into the Graylog SIEM tool. Read Part I to learn how to set up a Graylog server in AWS and integrate with Imperva Cloud WAF.
This guide assumes:
- You have a clean Graylog server up and running, as described in my earlier blog article
- You are pushing (or pulling) the Cloud WAF SIEM logs into a folder within the Graylog server
- You are not collecting the logs yet
Important! The steps below apply for the following scenario:
- Deployment as a stand-alone EC2 in AWS
- Single-server setup, with the logs located on the same server as Graylog
- The logs are pushed to the server uncompressed and unencrypted
Although this blog was created for a deployment on AWS, most of the steps below apply. Other setups (other clouds, on-premises) will require a few networking changes from the guide below.
This article will detail all the steps to configure the log collector and parser in few major steps:
- Step 1: Install the sidecar collector package for Graylog
- Step 2: Configure a new log collector in Graylog
- Step 3: Creating a log Input & extractor with Incapsula content pack for Graylog (the json with the parsing rules)
Step 1: Install the Sidecar Collector Package
- Install the Graylog sidecar collector
Let’s first download the appropriate package. Identify the right sidecar collector package suited for our deployment in Github: https://github.com/Graylog2/collector-sidecar/releases/
Since we are deploying Graylog 2.5.x, the corresponding sidecar collector version is 0.1.x.
Go ahead and install the relevant package.
We are running a 64bits server and .deb work best with Debian/Ubuntu machines.
Run the following commands:
cd /tmp #or any directory you would like to use
Download the right package:
2. curl -L -O https://github.com/Graylog2/collector-sidecar/releases/download/0.1.7/collector-sidecar_0.1.7-1_amd64.deb
- Install the package:
sudo dpkg -i collector-sidecar_0.1.7-1_amd64.deb
2. Configure sidecar collector
cd /etc/graylog/collector-sidecar
sudo nano collector_sidecar.yml
Now let’s change the server URL to the local server IP (local IP, not AWS public IP). And let’s add incapsula-logs to the tags:
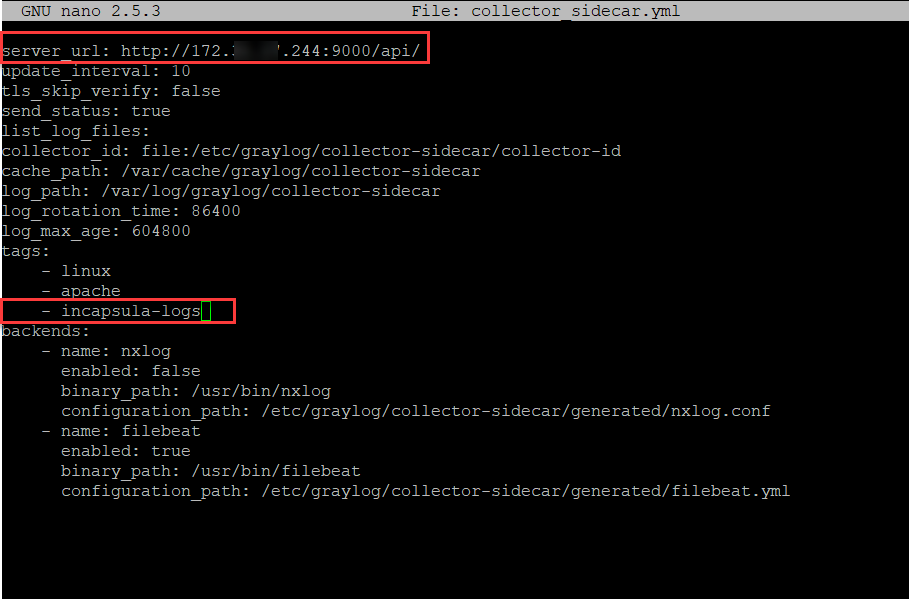 And let’s install and start graylog-collector-sidecar service with the following commands:
And let’s install and start graylog-collector-sidecar service with the following commands:
sudo graylog-collector-sidecar -service installsudo systemctl start collector-sidecar
Step 2: Configure a New Log Collector in Graylog
3. Add a collector in Graylog
Follow the steps below to add a collector:
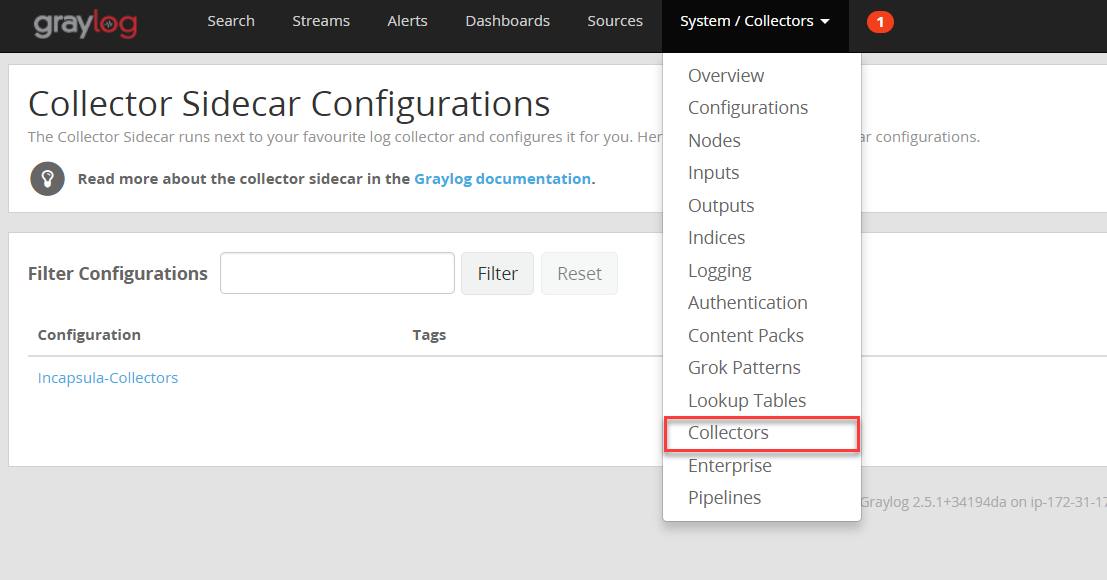
- System > Collectors
- Click Manage Configurations
- Then click Create configuration
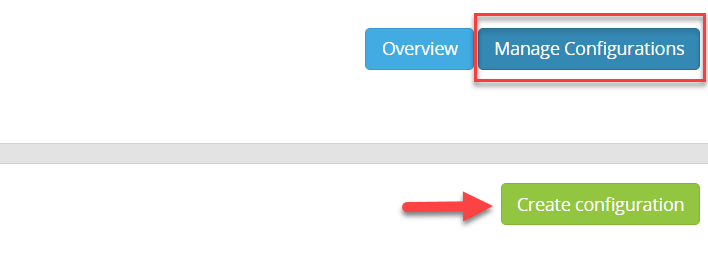 Let’s name it and then click on the newly-created collector:
Let’s name it and then click on the newly-created collector:
4. Add Incapsula-logs as a tag
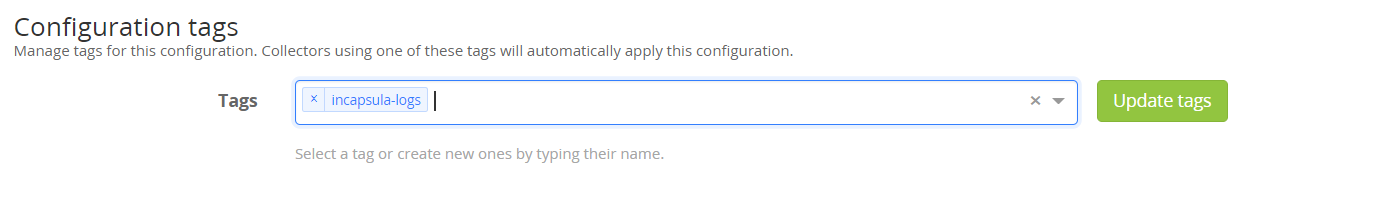 5. Configure the Output and then the Input of the collectors
5. Configure the Output and then the Input of the collectors
Click on Create Output and configure the collector as below:
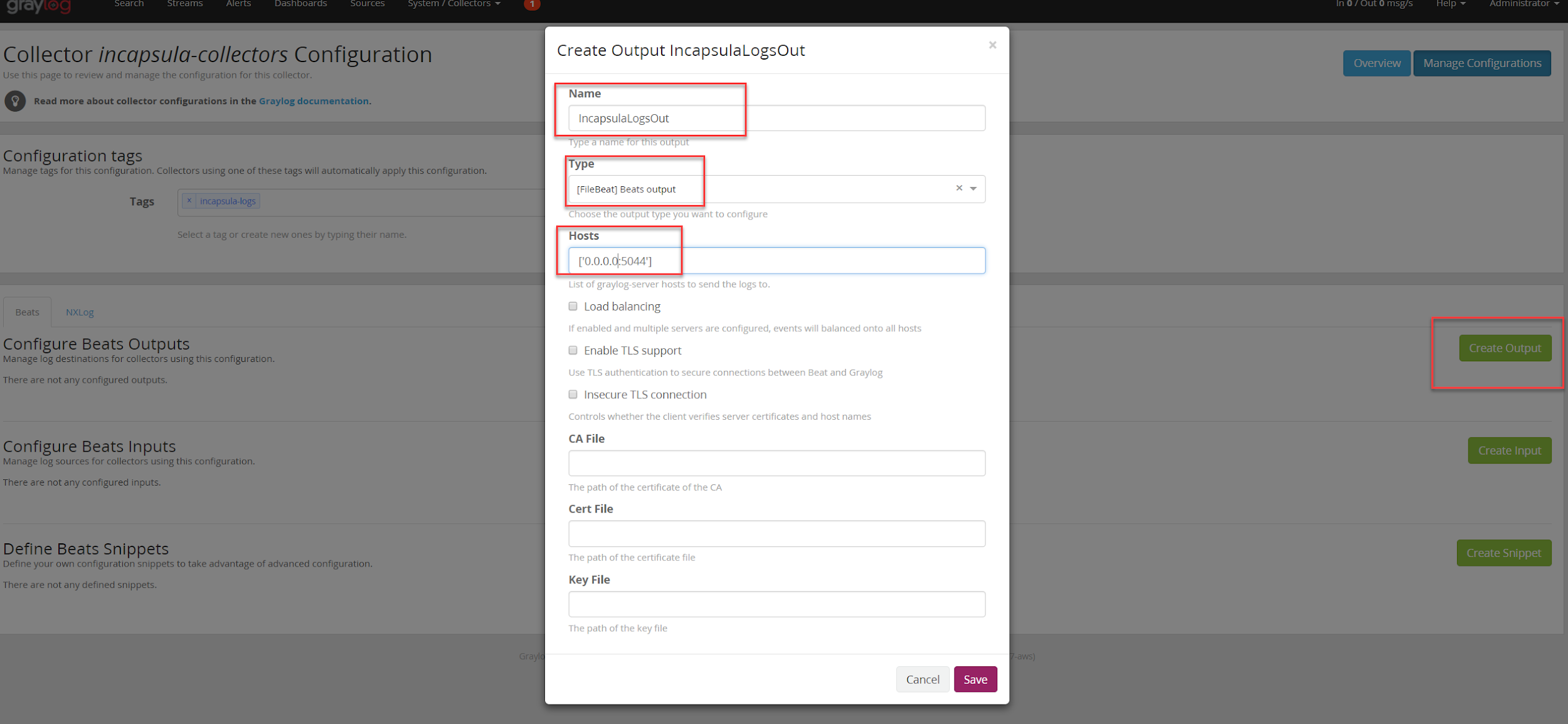 Now click on Create Input and configure the collector as below:
Now click on Create Input and configure the collector as below:
![graylog 2 7]() Step 3: Creating Log Inputs and Extractors with Incapsula (now named Imperva Cloud Web Application Firewall) Content Pack for Graylog
Step 3: Creating Log Inputs and Extractors with Incapsula (now named Imperva Cloud Web Application Firewall) Content Pack for Graylog
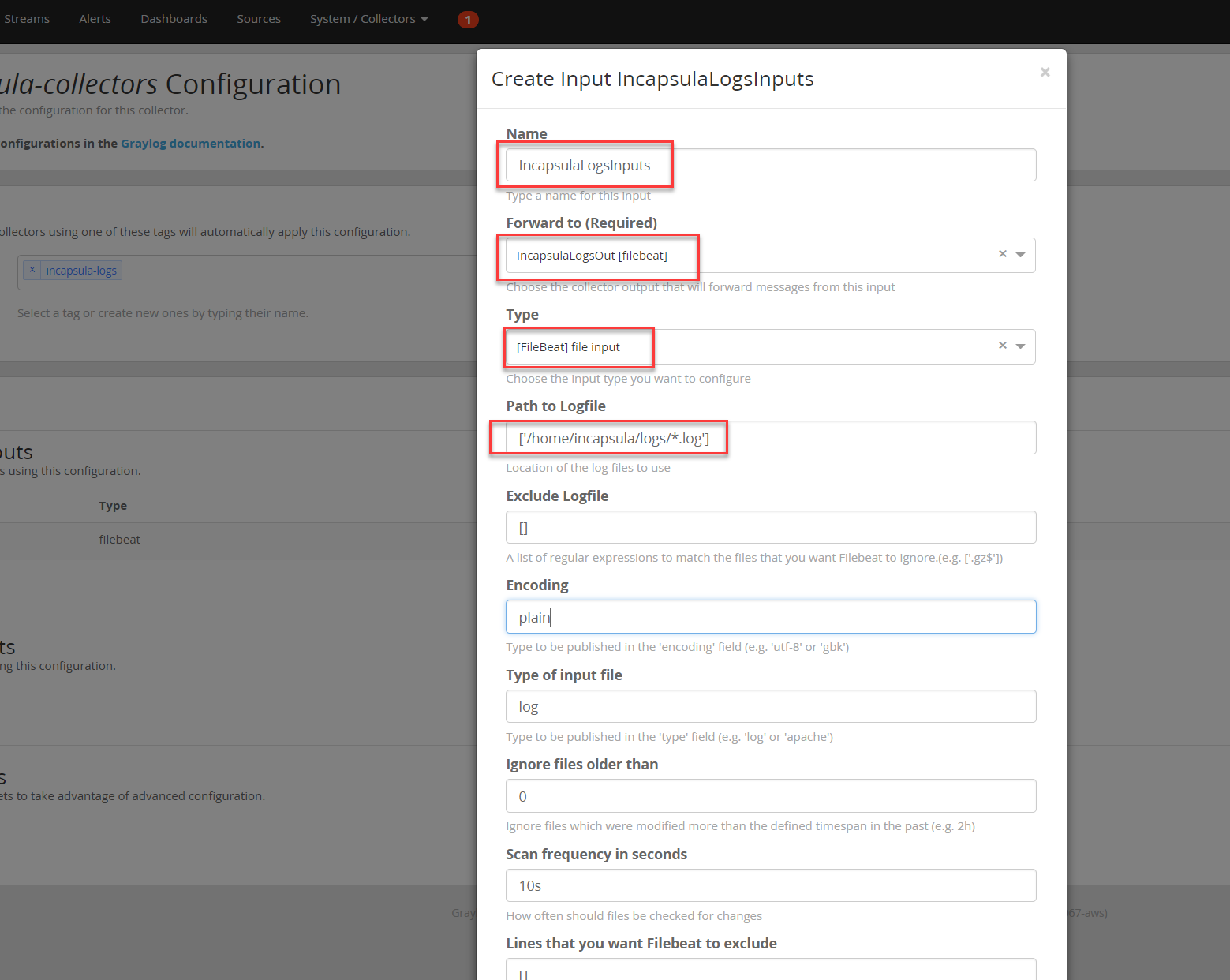
6. Let’s now launch a new Input as below:
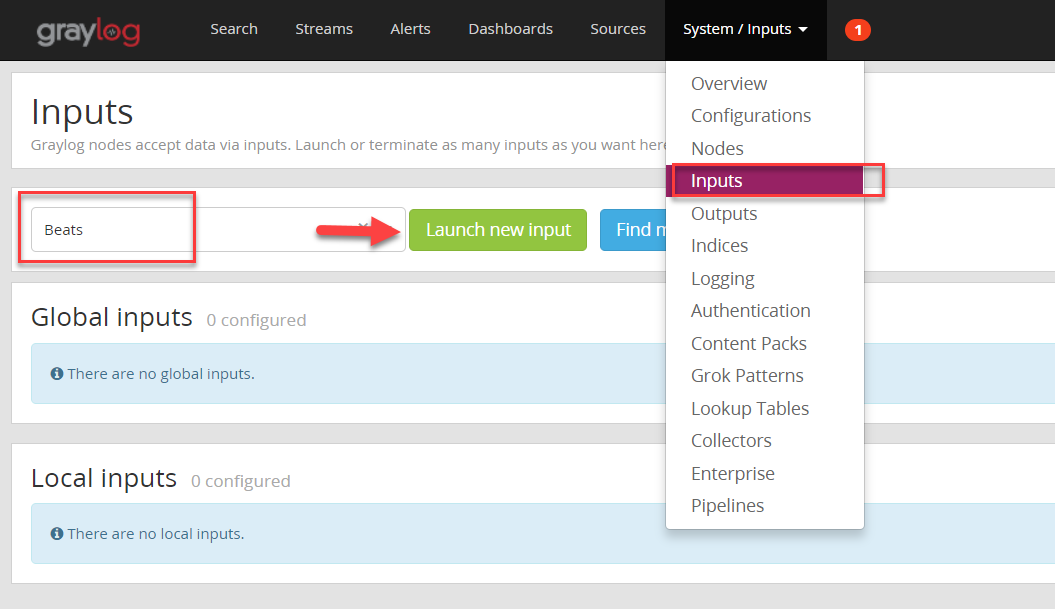 And configure the Beats collector inputs as required:
And configure the Beats collector inputs as required:
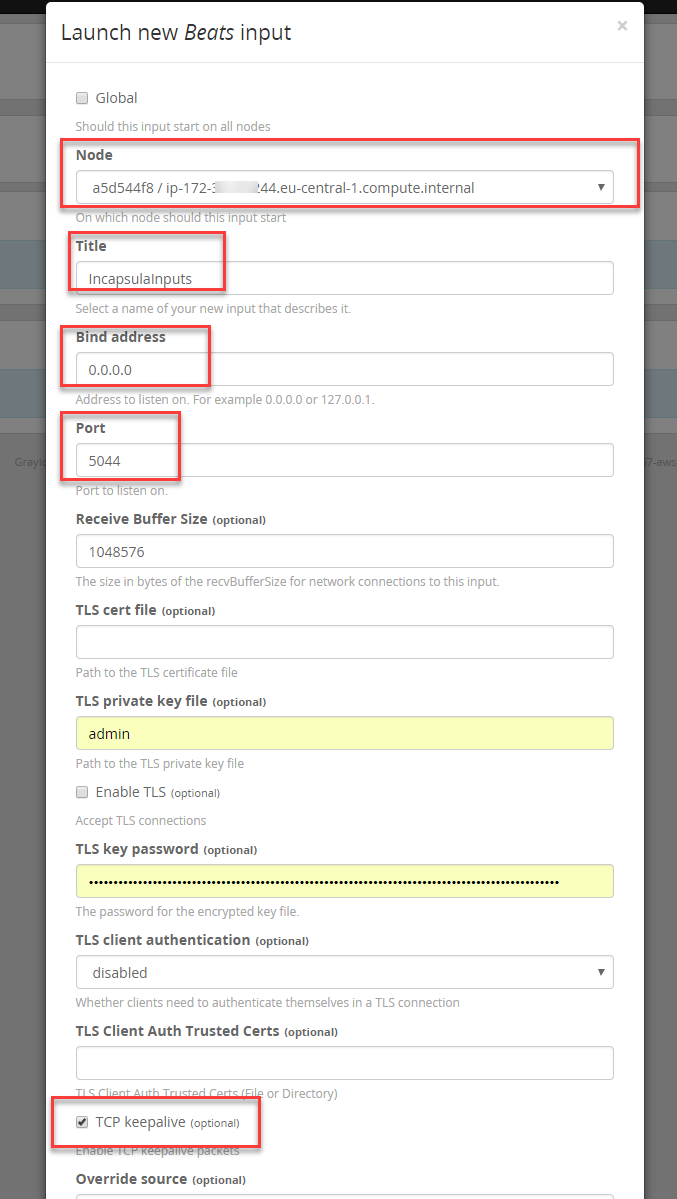 The TLS details are not mandatory at this stage as we will work with unencrypted SIEM logs for this blog.
The TLS details are not mandatory at this stage as we will work with unencrypted SIEM logs for this blog.
7. Download the Incapsula SIEM package for Graylog in Github
Reach the following link. https://github.com/imperva/incapsula-siem-package-graylog
Retrieve the json configuration of the package. It includes all the Imperva Cloud Web Application Firewall (formerly Incapsula) parsing rules of event fields which will allows an easy import within Graylog along with clear naming.
Extract the content_pack.json file and import it as an extractor in Graylog.
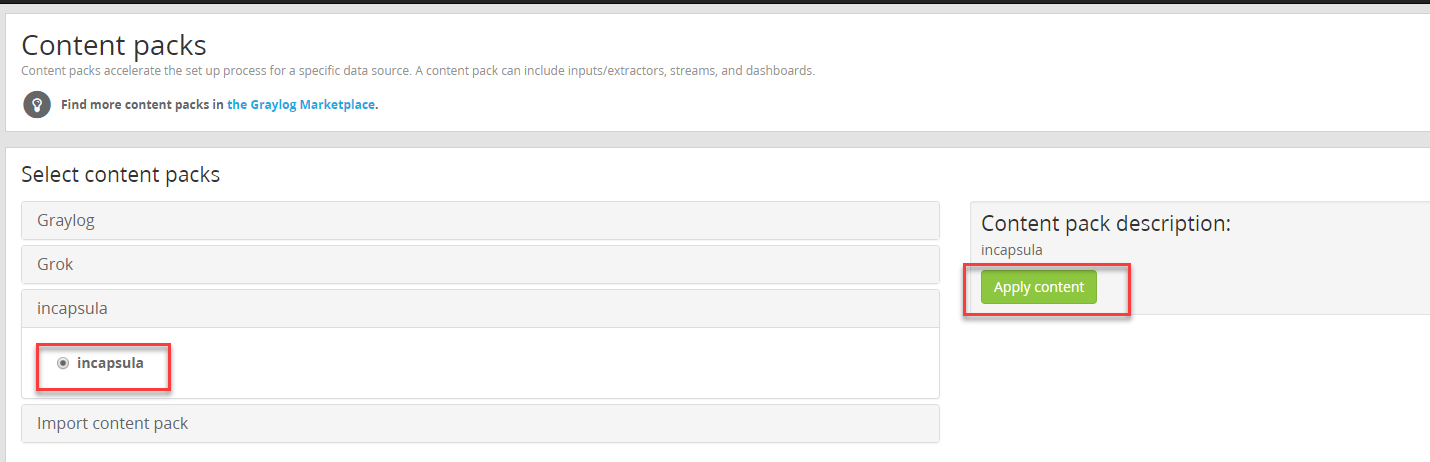
Go to System/ Content packs and import the json file you just downloaded:
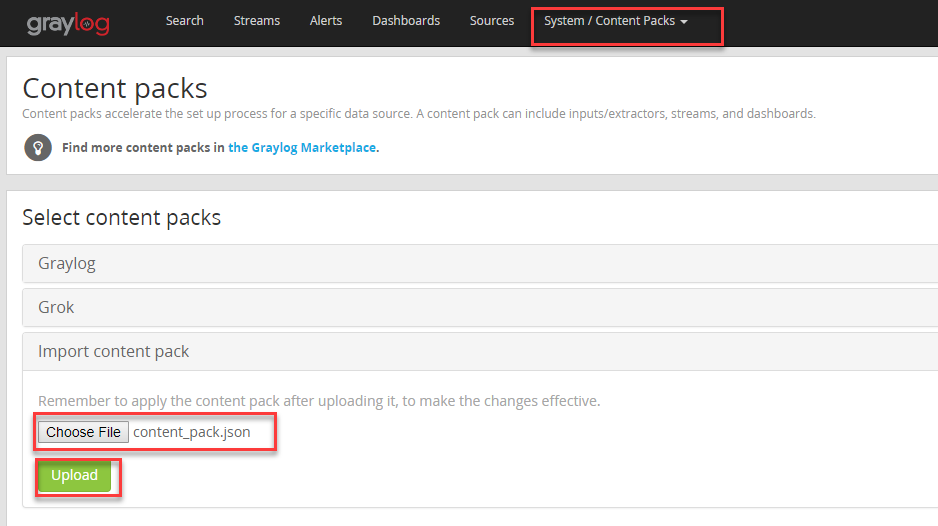 The content pack will use our legacy name and we can now apply the new content pack as below:
The content pack will use our legacy name and we can now apply the new content pack as below:
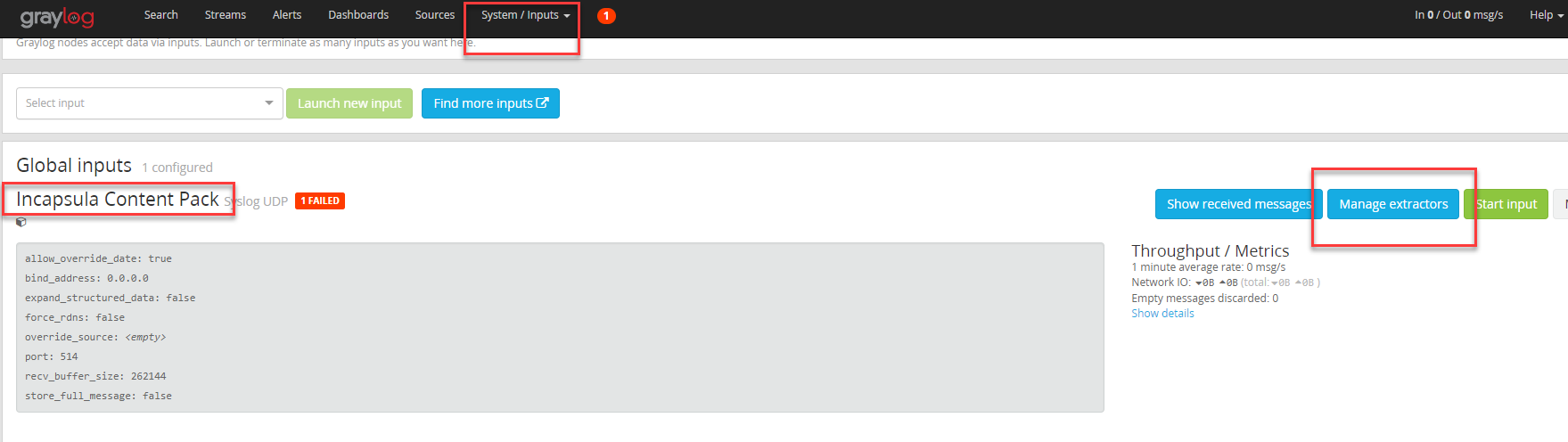
 The new content pack will be displayed in Graylog System / Input menu from which you can extract its content by clicking “Manage extractors”:
The new content pack will be displayed in Graylog System / Input menu from which you can extract its content by clicking “Manage extractors”:
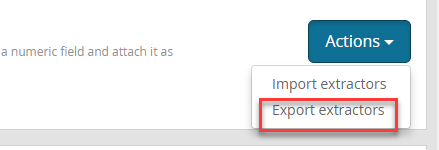
 And you can now import it in our predefined extractors to the input we previously configured.
And you can now import it in our predefined extractors to the input we previously configured.
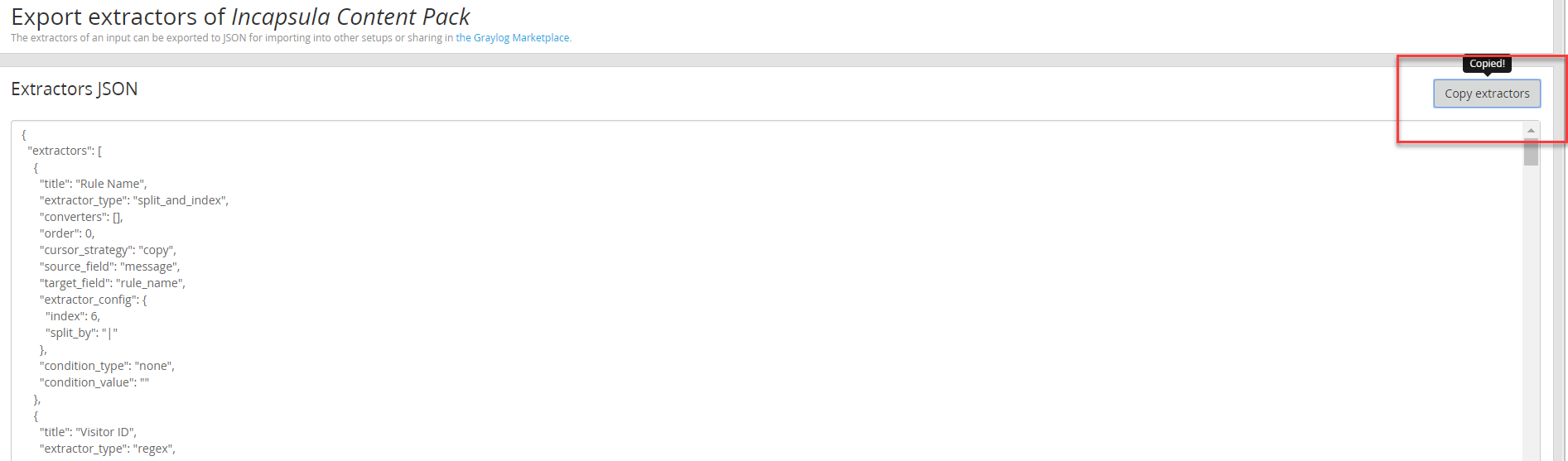
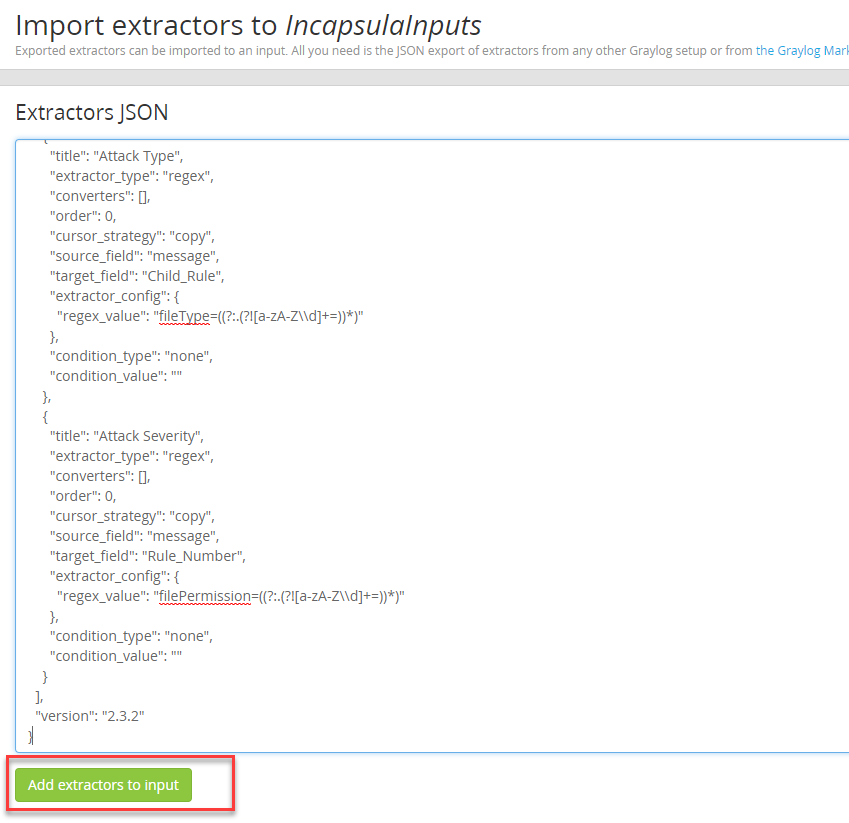
 Paste the content of Incapsula content pack extractor:
Paste the content of Incapsula content pack extractor:
 If all works as expected, you should get the confirmation as below:
If all works as expected, you should get the confirmation as below: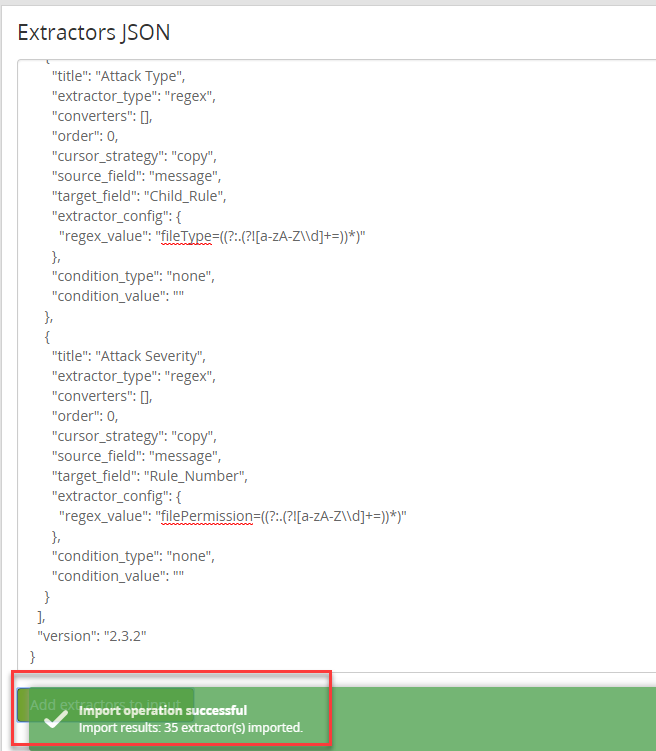
You should now see that the headers that will be parsed by Graylog have been successfully imported and will have appropriate naming as can be seen in a screenshot below:
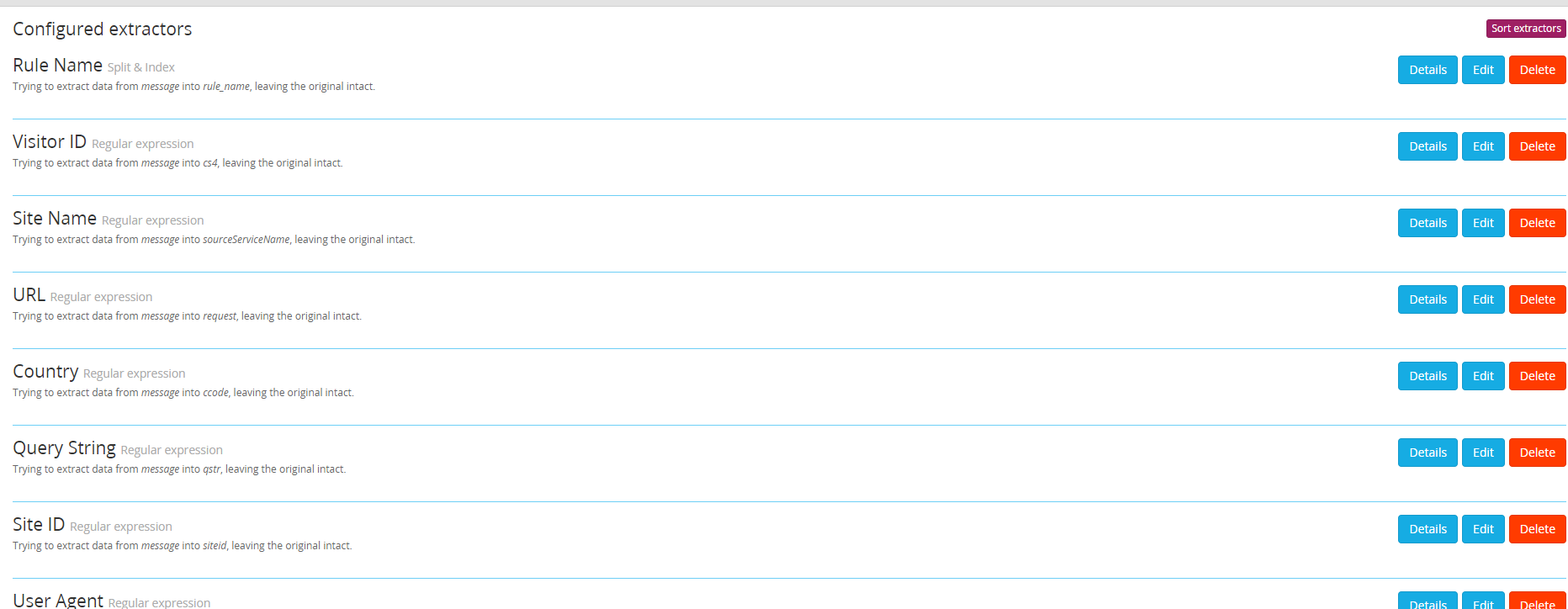
Field extractors for Incapsula (or Imperva Cloud WAF) events in Graylog SIEM:
8. Restart the sidecar collector service
Once all is configured you can restart the sidecar service with the following command in the server command line:
sudo systemctl restart collector-sidecar
We can also enforce sidecar collector to run at the server startup:
sudo systemctl enable collector-sidecar
Let’s check that the collector is active and the service is properly running: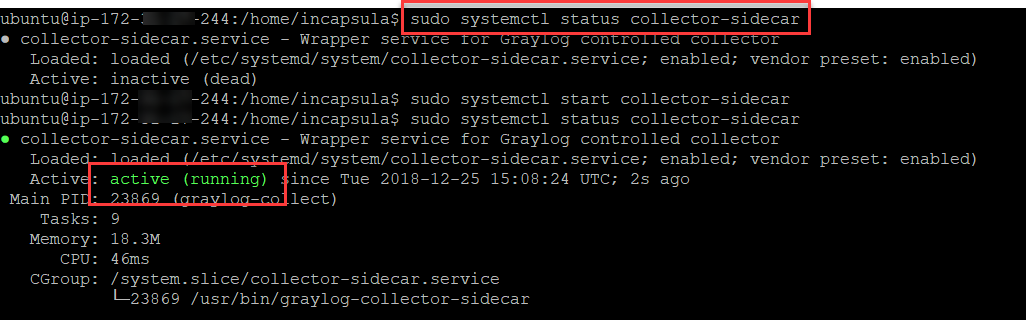
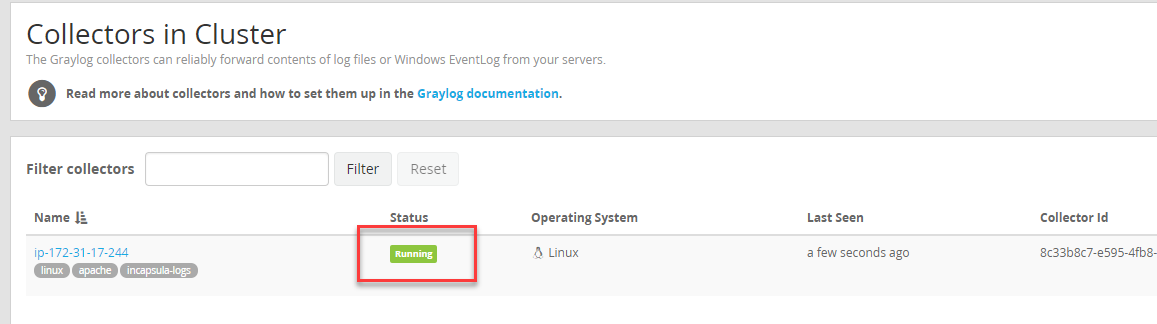
The collector service should now appear as active in Graylog:
9. Check that you see messages and logs
Click on the Search bar. After a few minutes you should start to see the logs displayed.
Give it 10-15 minutes before troubleshooting if you don’t see messages displayed immediately.
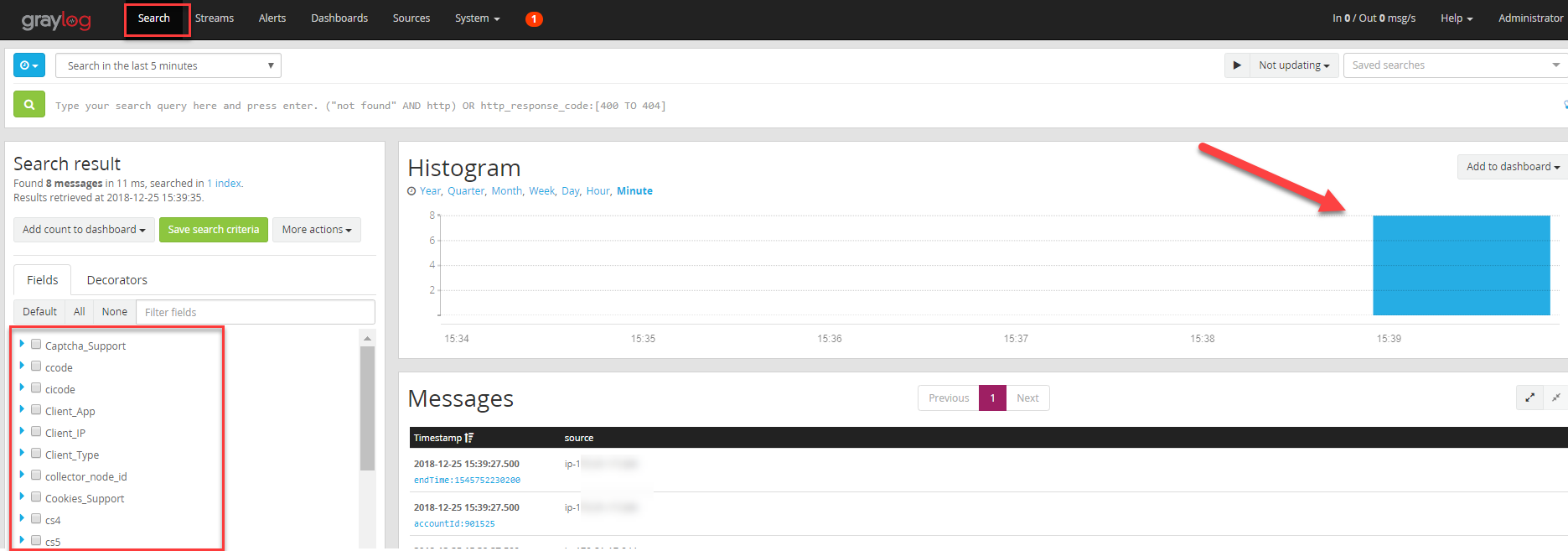
You can see on the left panel that the filters and retrieved headers are in line with Imperva. Client_IP are retrieved from the Incap-Client-IP and are the real client IPs, Client App are the client classification detected by Imperva Cloud WAF etc…
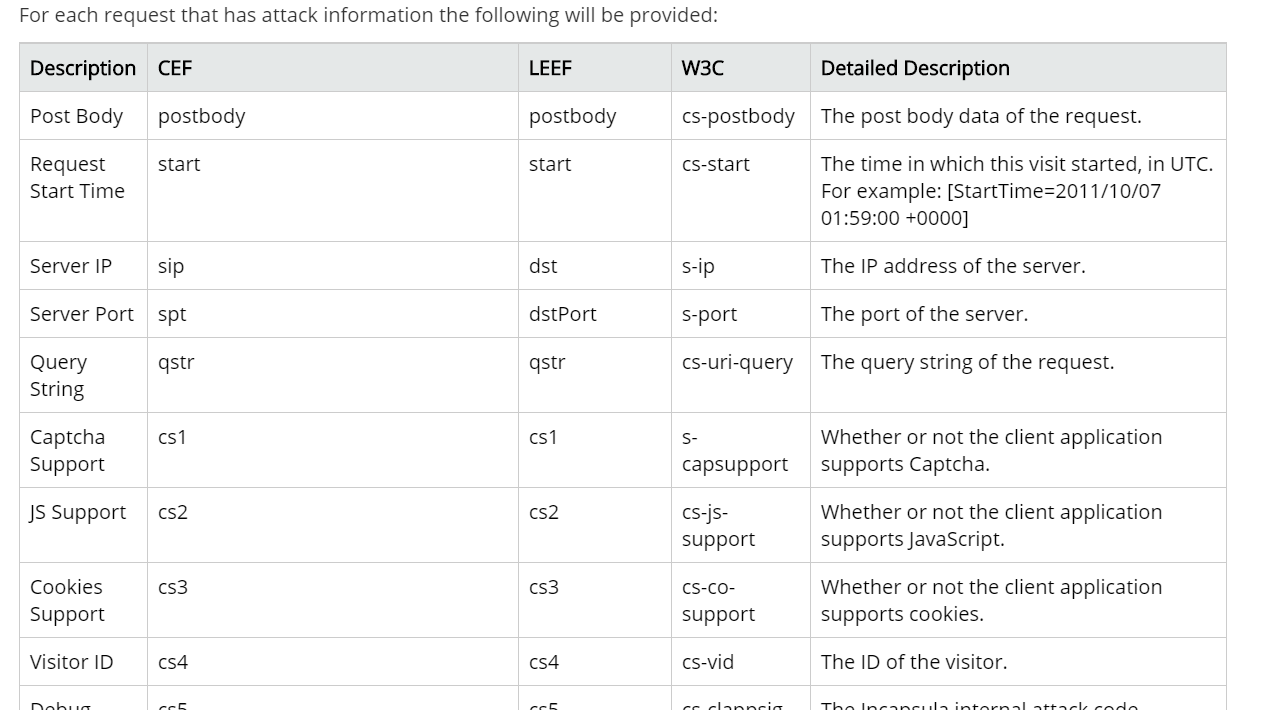
The various headers are explained in the following headers that you can see:
https://docs.incapsula.com/Content/read-more/log-file-structure.htm
10. Congratulations!
Congratulations, we are now successfully exporting, collecting and parsing Imperva Cloud WAF/Incapsula SIEM logs!
In the next article, we will review the imported Imperva Cloud WAF dashboard template.
If you have suggestions for improvements or updates in any of the steps, please share with the community in the comments below.
Try Imperva for Free
Protect your business for 30 days on Imperva.



 Step 3: Creating Log Inputs and Extractors with Incapsula (now named Imperva Cloud Web Application Firewall) Content Pack for Graylog
Step 3: Creating Log Inputs and Extractors with Incapsula (now named Imperva Cloud Web Application Firewall) Content Pack for Graylog








