Account Takeover (ATO) describes when an online account is accessed and/ or used by someone other than its legitimate owner, usually for malicious purposes. Account Takeover attacks happen when an attacker is trying to get unauthorized access to an account or when the account has already been compromised and the attacker uses the account for a malicious purpose, such as unauthorized access or data theft.
Although the risk is not new, Account Takeovers pose one of the top risks for financial loss for corporations and individuals today. The reality is that businesses rely on limited detection methods like static security rules, rate limit and basic bot protection. These methods work well on technical attacks like SQL injection or cross site scripting. When part of an integrated multi-layered solution, they also help provide defense-in-depth that can help slow down the momentum of a wide variety of attacks.
However, those methods are less effective against business logic attacks such as ATO that target, for example, user logins. These methods can be easily bypassed as today’s ATO attackers use advanced tools and a widely-distributed infrastructure that allows them to operate at a slow steady rate, impersonate legitimate clients and to morph the attack when needed.
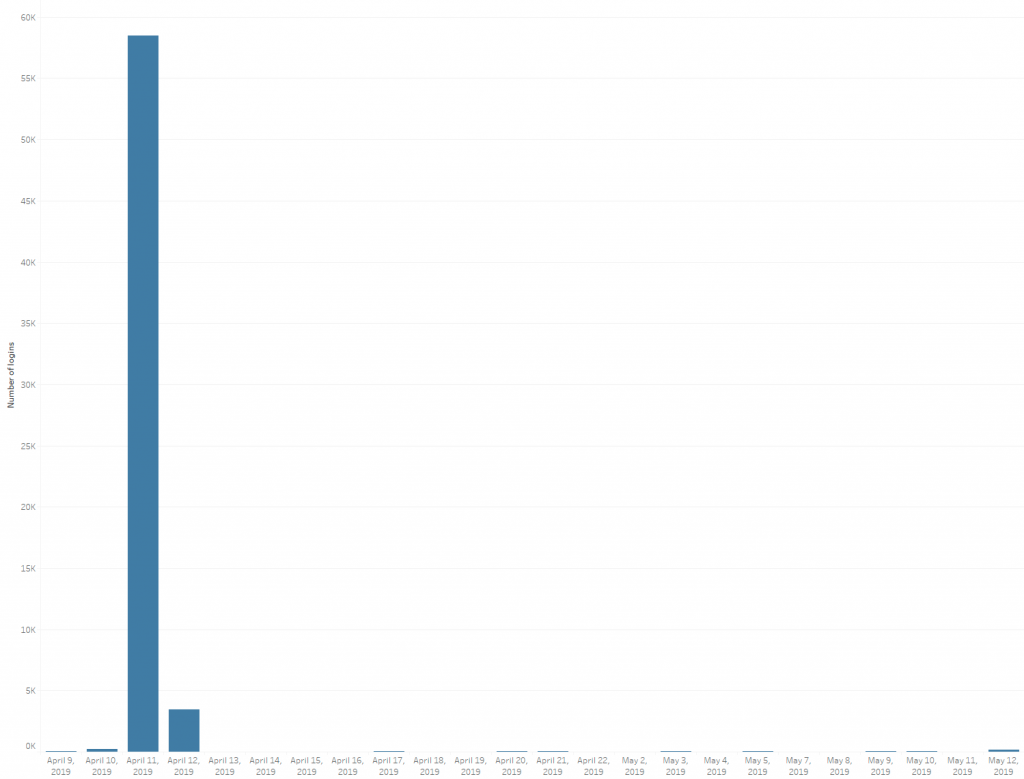
To better understand the problem, let’s look at this real life example of site login traffic (figure 1). The daily volume is almost the same, except for one specific day. When looking into this day using traditional security controls, we cannot point out any suspicious activity — no strange errors, no known attacks, no device operating at a high rate and no hacking tools or other bad bots involved. This incident would likely be considered benign and overlooked in the sea of potential security events that the SOC team handles daily (click on graphics below to enlarge).
Figure 1 – login requests distribution over time in a single site
Now let’s look at this example again from a different angle with a different security control — behavioral-based detection.
Behavioral-based detection methods analyze deviations from normal user behavior, providing more advanced security controls that can deal with complex attacks.
In the context of account takeover, we talk about the behavior of a user or a device when accessing the login page or the authentication API. There are many potential variables that can be used to define normal behavior: the ratio of successful vs. failed login attempts, the ratio of weak passwords or common users, usage of leaked credentials, number of users per device, etc. Of course, your security solution would need to be aware of the context of the requests that it examines, whether they are indeed login attempts, the provided user, and the password and login attempt result. In addition, prior knowledge of common users, weak passwords, leaked credentials, and way to keep these lists updated, are all required. Once you have all that in place, you can start learning what is normal behavior and detect anomalies that may indicate account takeover attacks. The learning phase and the certainty of the learned behavior are determined by the amount of data that you inspect. If you inspect a lot of data then you might be able to build a reliable behavior model. Taking this one step further, you can also aggregate the attack data and run analytics on it. Running analytics on a single site may prove useful; if you run your analytics on top of hundreds of thousands of sites, you can get much more interesting results.
And this is exactly what we have done 😉
Running an analysis on the attack data, we managed to uncover several botnets whose sole purpose is to take over accounts. We also discovered why, from a single site point of view, these attacks are so difficult to defend from.
The Data
The data was collected by our Account Takeover Protection solution based on behavior anomalies detected when a user or a device accessed the login page or the authentication API as explained above. Since Imperva protects more than 100,000 websites that receive millions of login attempts each day, we are talking about a lot of data. This data stored in our data lake has generally been hashed or masked of personal data, and allows us to run all kinds of analytics. In this case, we used a machine learning algorithm (dbscan) to cluster ATO attacks events based on the magnitude of the attack, time of occurrence and similar credentials to establish a correlation between various devices that form a botnet.
In the following section we will focus on a specific botnet, a group of devices that are highly correlated based on the above mentioned features, that operated between April 7th to April 22nd this year.
The Botnet
The botnet contained 2,500 IPs overall and attacked more than 300 sites while active. Each day, 800* IPs (figure 2, right side) were active attacking 30* sites with 150,000* login attempts (*median value). 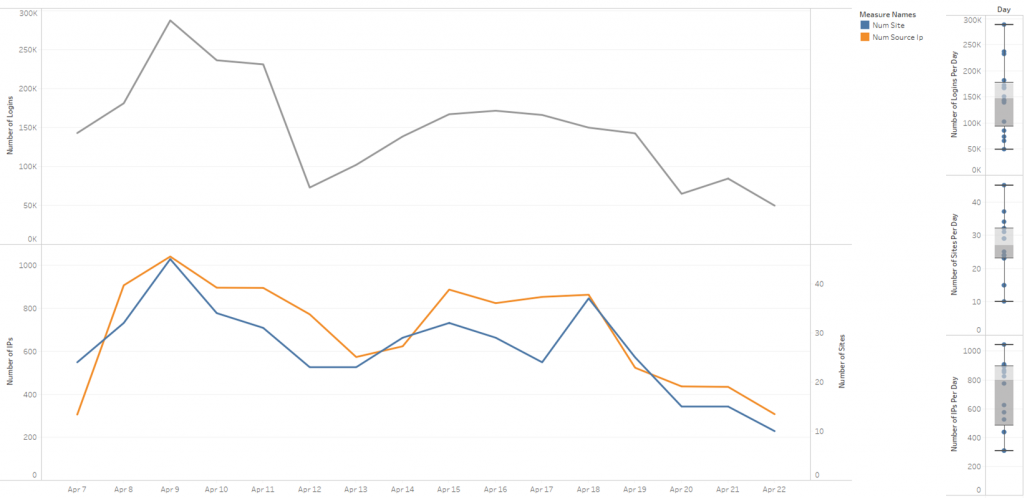
Figure 2 – overall botnet activity (left side) and its statistics (right side)
Looking at this botnet from the victim site perspective, we found that each site was attacked for 7* hours (figure 3) by 500* IPs (figure 4) sending 7,000* login attempts (figure 5) with 7,000* different credentials (*median value).
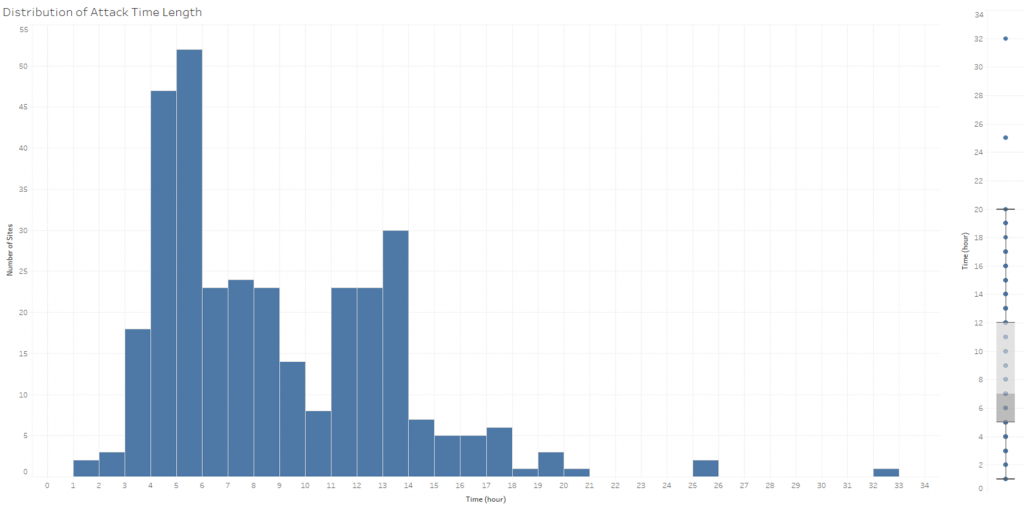 Figure 3 – Distribution of botnet activity over time (left side) and its statistics (right side)
Figure 3 – Distribution of botnet activity over time (left side) and its statistics (right side)
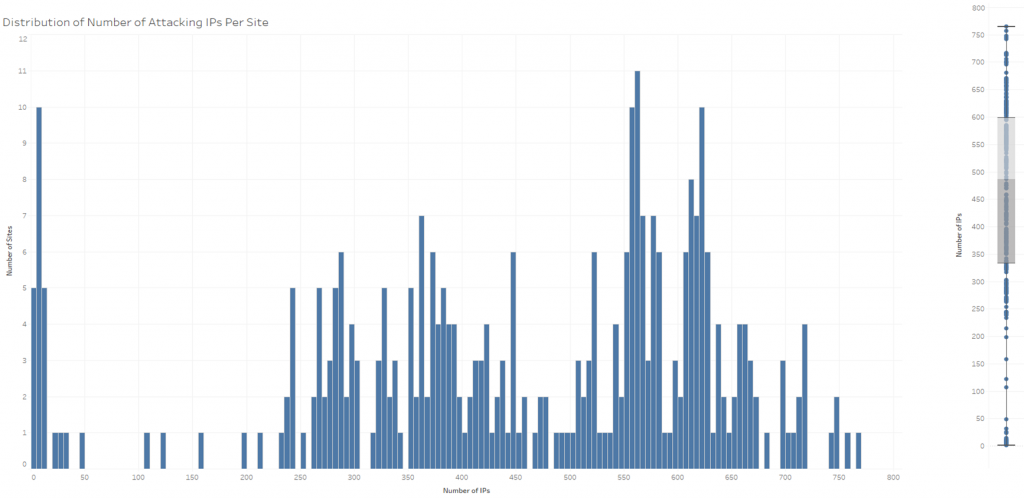 Figure 4 – Distribution of botnet IPs per site (left side) and its statistics (right side)
Figure 4 – Distribution of botnet IPs per site (left side) and its statistics (right side)
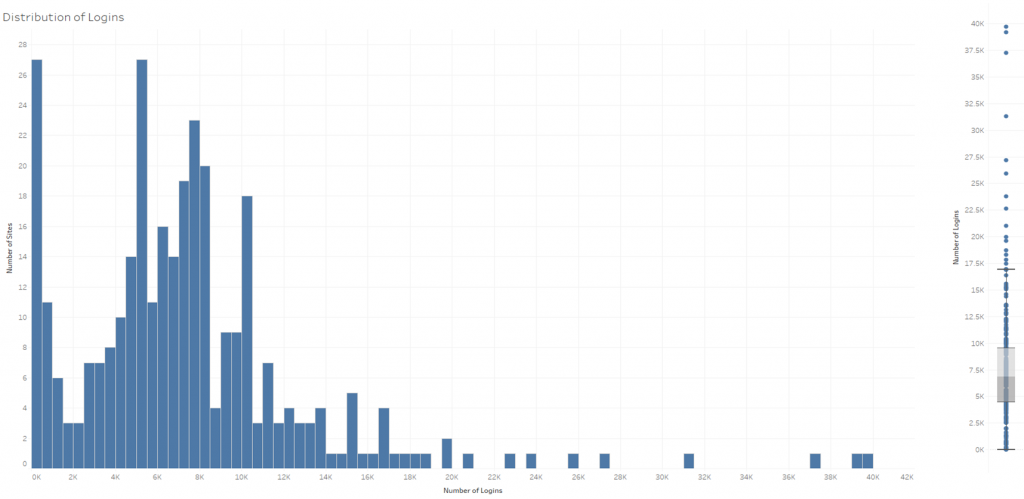 Figure 5 – Distribution of botnet login attempts per site (left site) and its statistics (right side)
Figure 5 – Distribution of botnet login attempts per site (left site) and its statistics (right side)
From a single site perspective, each botnet-controlled IP was responsible for ~14 login attempts during the attack time, or ~2 login attempts per hour. This is called a “low and slow” attack – the botnet uses a lot of devices, each sending only a handful of requests, to masquerade its attack with legitimate traffic.
It is clear now why traditional security controls couldn’t have identified this attack. Since Imperva Account Takeover Protection relies on behavior-based detection, we were able to detect this activity and protect the relevant sites. Moreover, the botnet activity started on April 7th and this particular site was not hit until April 11th. That means we can use this knowledge to provide Account Takeover Protection before a website admin would be aware of a potential attack.
Conclusions
Business logic attacks such as account takeover require more advanced detection tools. It is difficult to defend against ATO attacks using traditional defense mechanisms since, as demonstrated above, attackers use advanced tools and wide infrastructure that allows them to spread the attack and to go undetected for a long period of time.
As attackers progress technologically, so should defenders. Behavioral-based detection takes defenders one step forward in this long path, as it can provide an effective way to find anomalies that highlight ATO attacks.
Account Takeover Protection is available to Imperva FlexProtect customers and is part of the Imperva Application Security suite. For broader protection against bots, including Account Takeover attacks, Imperva also offers its Bot Management solution acquired from Distil Networks.
Try Imperva for Free
Protect your business for 30 days on Imperva.