Ransomware has loomed large in the news of late. It seems to be around every turn, and it’s not going anywhere. The untraceability of Bitcoin payments, coupled with new blackhat tools available to anyone at little (if any) cost, means extortion attempts will continue to grab headlines worldwide.
But is ransomware the only form of cybercrime extortion? The short answer is no. People commonly refer to any form of online extortion as ransomware, but it may have nothing to do with ransomware in the strictest sense of the word. Specifically, ransomware is a form of malware that encrypts files and decrypts them once a ransom is paid. But illicit demands for payment—by definition, a ransom—can be associated with other types of digital extortion requests.
This may seem like semantics. But it matters when it comes to mitigating extortionary attacks; just because a solution may detect ransomware, doesn’t mean it protects against other extortionary attacks. And we expect extortionary attacks to increase. To a certain extent, the darkweb is saturated/flooded with PII for sale. This drives down cybercriminal profits. As this occurs, it is likely many cybercriminals add extortionary attacks as they attempt to optimize their profits.
In this post, we clear the ransomware air. We’ll explain exactly what “traditional” ransomware is and how it works, and review other common digital ransom-related attack types that are often, mistakenly, labeled as ransomware.
Traditional Ransomware
The name ransomware is derived from ransom and software. It’s a type of malware attack in which the attacker locks and encrypts the victim’s data and then demands a payment to unlock and decrypt the data (see Figure 1). Ransomware attacks take advantage of human, system, network, and/or software vulnerabilities to infect a victim’s device—which can be a computer, printer, smartphone, wearable, point-of-sale (POS) terminal, or other endpoint. Ransomware can target either endpoints or file servers. It doesn’t need to be “local” to infect; ransomware that infects and endpoint can encrypt a remote file share without having to run locally on that remote file share.
WannaCry (a.k.a., WCry or WanaCryptor) is one recent, highly-publicized ransomware example. It takes advantage of systems running older, unpatched versions of Microsoft Windows. A key difference is that, like a worm, this ransomware propagates itself to connected systems by way of a Server Message Block (SMB) protocol vulnerability.
There are several kinds of ransomware distribution techniques, but perhaps the most common is email. An attacker sends an email—ostensibly from a trusted source—that tricks the recipient into clicking a link which unleashes the payload. When the victim clicks the link, visits a web page, or installs a file, application, or program that includes the malicious code, the ransomware is covertly downloaded and installed.
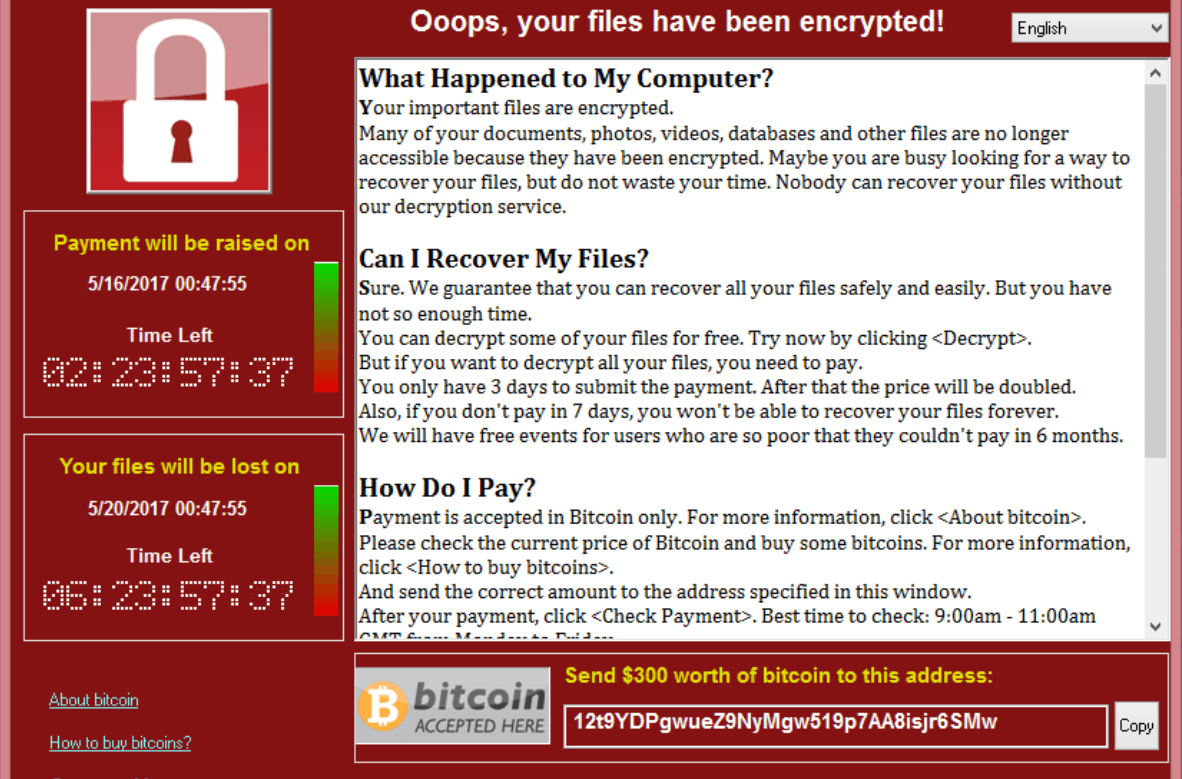
Figure 1: Example of a ransomware ransom note demanding payment.
In particular, so-called email phishing attempts have become increasingly more sophisticated. TechTarget says such “messages usually appear to come from a large and well-known company or website with a broad membership base, such as Google or PayPal. In the case of spear phishing, however, the apparent source of the email is likely to be an individual within the recipient’s own company—generally someone in a position of authority—or from someone the target knows personally.”
DDoS Ransom Notes
A 2015 FBI public service announcement says it all: “The Internet Crime Complaint Center (IC3)… received an increasing number of complaints from businesses reporting extortion campaigns via e-mail… the victim business receives an e-mail threatening a distributed denial of service (DDoS) attack to its website unless it pays a ransom. Ransoms vary in price and are usually demanded in Bitcoin.”
An Imperva Incapsula survey found that “46% of DDoS victims received a ransom note from their attacker—often prior to the assault.” Figure 2 below shows a ransom note from a hacker group calling themselves the Armada Collective that was blackmailing hosting providers in Switzerland:

Figure 2: A ransom note from Armada Collective announcing an impending DDoS attack
Today DDoS-for-hire is readily available at very inexpensive prices, making it easy for anyone to launch an attack on the scale of those unleashed by the infamous Lizard Squad. In wrapping up 2016, the Imperva Global DDoS Threat Landscape report stated, “…the higher number of persistent events can be interpreted as a sign of professional offenders upping their game.” On the other hand, the preponderance of short attack bursts can be attributed to the growing popularity of cheap botnet-for-hire services preferred by non-professionals.
Another security survey revealed that “80 percent of IT security professionals believe that their organization will be threatened with a DDoS ransom attack in the next 12 months.”
Data Theft and Extortion
Dubbed extortionware (a.k.a., doxware), another common threat involves the theft of personal or sensitive data coupled with a threat to openly release it—perhaps to the internet at large—unless a ransom is paid. Author and enterprise threats expert Nick Lewis describes extortionware as “…when a cybercriminal threatens a person or organization with some sort of harm by exposing personal or sensitive information. For example, a criminal could compromise a database with sensitive data and then tell the enterprise [they] will post the sensitive data on the internet if [their] demands aren’t met.”
Another type of ransom-related attack is akin to the threat above, but in this case the enterprise doesn’t retain access to its data. A recent widely known example of this is when an entity calling itself The Dark Overlord, earlier connected to a health care breach, claimed to have stolen several new episodes of Netflix’s popular Orange Is the New Black show and demanded an unspecified ransom in exchange for their return.
Like a similar theft involving the BBC, Netflix confirmed that one of its production vendors—also used by other studios—had been breached. The Guardian suggested that, “Pirated copies of the show could dent Netflix’s subscriber growth and the company’s stock price.”
What You Can Do
For any of these threats, it’s back to basics: protect your systems and data. The ransom/ransomware trend is expected to continue as incentives increase and it becomes easier for cybercriminals to execute shakedowns armed with new ransomware-as-a-service (RaaS) tools, BYOD user vulnerabilities, improved encryption methods and untraceable Bitcoin payoffs.
A good defense begins with running regular backups and always using accounts having the fewest permissions. The ability to dynamically assign and, more importantly, retract user permissions through machine learning and granular data inspection is a solid best practice.
Ideally, you want to immediately detect ransomware behaviors and quarantine impacted users before ransomware can spread to network file servers. One approach is deception-based ransomware detection, which consists of using strategically planted, hidden (decoy) files to identify ransomware at the earliest stage of the attack. The decoy files are planted at carefully planned file system locations in order to identify ransomware encryption behaviors before they can touch legitimate files. Having monitoring and blocking measures in place—in addition to admin alerts and granular activity logging—would also help minimize the disruption to your core business processes were a ransomware attack to occur.
When it comes to preventing DDoS attacks, organizations can also invest in always-on DDoS protection that automatically detects and mitigates attacks targeting websites and web applications, as well as protects against DDoS attacks that directly target your network infrastructure.
Along with these measures, other basic defenses such as business continuity and disaster recovery planning should be part of any comprehensive information security program.
Learn more about Imperva’s deception-based ransomware detection, specific vulnerabilities, ransomware variants and malware trends in our report: Insider’s Guide to Defeating Ransomware.
Try Imperva for Free
Protect your business for 30 days on Imperva.




