Data breaches continue to be the thorn for most organizations despite the sophisticated and innovative cybersecurity tools that are used to stop what is now the inevitable cost of doing business in a hyperconnected world.
In this blog post, I’ll explain how organizations can increase the effectiveness of their cybersecurity programs to protect digital assets. But first, if any system is to achieve an effective rate that is both measurable and meaningful to the business, there has to be a full understanding of threats, tactics, and techniques that pose risks to critical data. Given the growing complexity of attacks through advanced automation, simply throwing resources at responding lacks the scale necessary to effectively manage sophisticated threats. Therefore, it is imperative to develop an ontological view of digital assets and how they are consumed by users and entities.
The Ontological Perspective
Data ontology is a key concept used by data scientists to understand the relationship between processes and datastores. When this concept is extended to data security, it can help to organize data, applications, APIs, devices, and users into structures and establish the relationships between the different elements to enhance the detection of anomalies. The relationship between data and the entities that consume that data is what yields the outcome of digital transactions.
Unlike data taxonomy which describes the hierarchical structures of data, for the purpose of cybersecurity, data ontology helps practitioners develop a holistic strategy to protect critical data by factoring in the independent elements of digital transactions and their impact on the journey of critical data.
The complexity of understanding the relationship between data, users, and entities comes from not understanding the context of their interaction. In the domain of cybersecurity, if the context of users, entities, and their use of data can be established as a baseline, and monitored, identifying anomalies that can lead to data breach comes as a natural byproduct.
Flattening the relevant attributes of attacks, we can summarize them within the Five W’s:
- What – What happened? Data breach or service disruption?
- When – When did it happen? Is it an active attack or a contained event?
- Who – What is the profile of the attacker(s)?
- Where – Where did the attacker come from (internal or external) and through which systems?
- Why – Can we deduce the motive of the attack? Fraud or/and disruption?
To qualify the five W’s which are essential in contextualizing threats, we can break them out into pivotal elements of data ontology:
- User: An individual who uses the system or service. Attributes may include user ID, user name, access level, user role, etc. In the case of external access, a user denotes the service consumer.
- Device: A piece of hardware that a user interacts with. Attributes may include device ID, device type (e.g., mobile, desktop), operating system (OS), etc.
- APIs: APIs can be defined as the protocol that enables the abstraction of complex data structures through normalizing of datasets into consumable chunks. This standardizes the representation of data and information exchange across all devices.
- Application: Software that is used for tasks. Attributes could be application ID, application type (e.g., office suite, browser), version, etc.
- Data: Information that a user can create, read, update, or delete. Attributes can include data ID, data type (e.g., personal, financial), data classification (e.g., public, confidential), etc.
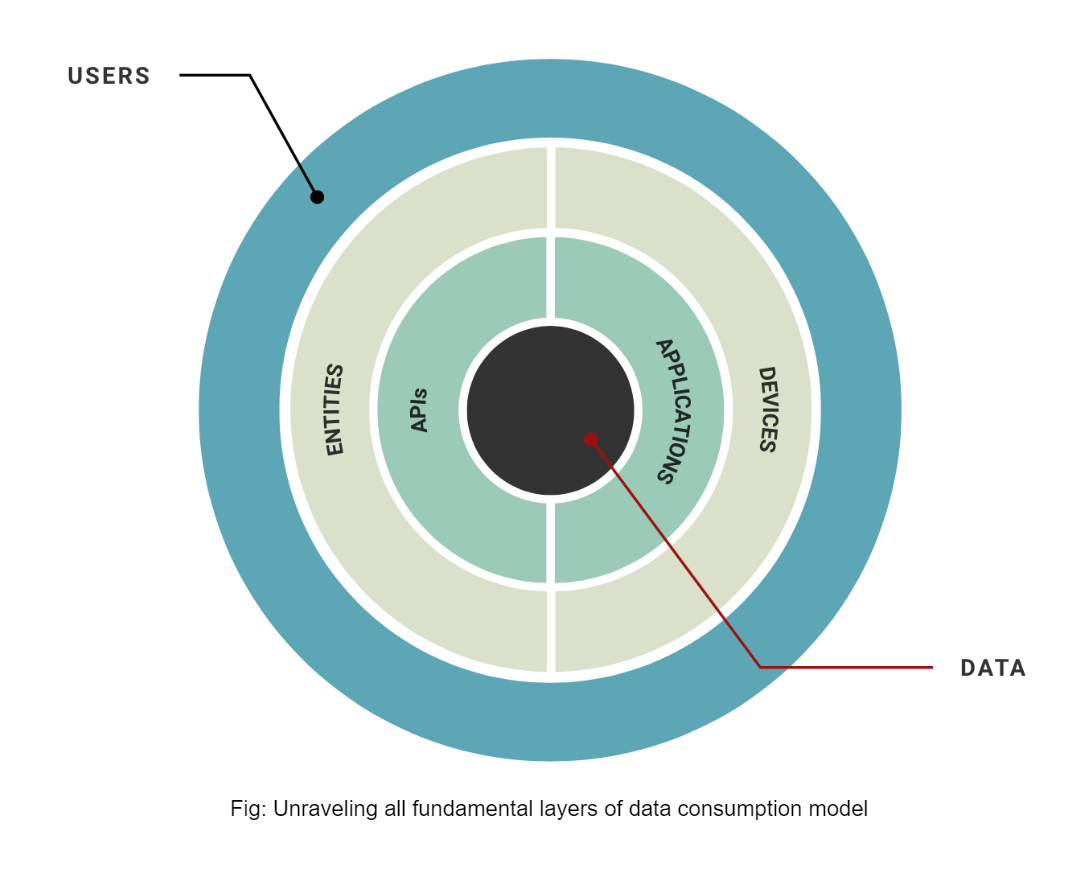
In normal operating procedure, let’s consider a simplified context whereby “users” interact with “entities” like “devices,” to access “APIs” for microservices that provide services within the scope of an “application” stack to access “data”. But likewise, in every data breach involving a fraud use-case, these common elements are often abused to yield results for adversarial actors. Therefore, understanding the relationships across all the elements is material to creating a functional response strategy that can sense when each of the elements is abused then nullify the implication in an expeditious manner.
How Imperva Helps
Imperva focuses on the boundaries beyond the conventional access control management to data by looking at the relationships between users and data at the query and protocol level. This allows Imperva to rapidly identify the legitimacy of users and how they consume data:
- Who – ascertain the legitimacy of users and entities
- How – monitor how connections are established to data (device, applications, APIs)
- What – what the user is doing with their access to data
- When – time that user initiated access and the significance of it to their behavior
- Where – Validate the legitimacy of the user’s location
- Why – use all available data points to deduce the intent of the user
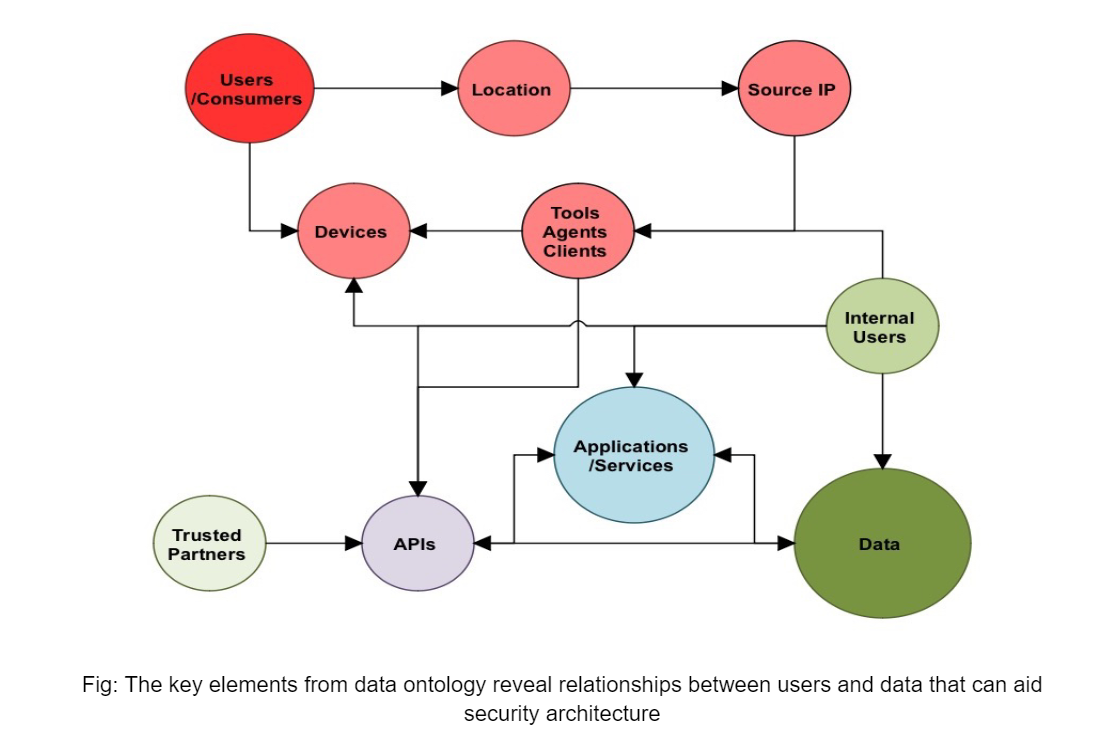
Imperva uses the information from application, API, and data activities to understand the acceptable behavior of users and when bad actors deviate from acceptable standards to effectively stop data breaches.
Imperva Helps to Contextualize and Stop Threats at the Data Layer
Imperva resolves this gap by continuously monitoring the journey of each user at the data layer by analyzing millions of queries to datastores and discerning anomalous behaviors from queries that can eventually lead to data breach. This is made possible because Imperva products understand the language used at the data layer and the concept of data ontology to eliminate blind spots. This capability is a fundamental requirement for securing digital assets. By taking an ontological view, Imperva understands the relationship between users and data which helps customers derive meaningful context.
Understanding the relationship between users and devices is essential for protecting applications and APIs. By understanding key elements of data ontology through reputation intelligence and client classification, Imperva can preemptively stop malicious attacks on APIs and critical applications.
The Imperva suite of data and application security products provides organizations the foundational controls necessary to detect fraudulent activities at the application and API layer. Beyond that, at the data layer, Imperva products can protect critical digital assets and data from theft and abuse.
Try Imperva for Free
Protect your business for 30 days on Imperva.





