(Updated Oct. 19, 2022)
CVE-2022-42889 was recently added to the NVD catalog, with a critical score of 9.8. This vulnerability allows remote code execution (RCE) in Apache Commons Text. It affects version numbers 1.5-1.9, and an upgrade to Apache Commons Text 1.10.0 disables the problem by default.
Apache Commons Text, a commonly used library originally released in 2017, includes algorithms for string functionality. The library performs a process called variable interpolation, which evaluates the properties of strings that contain placeholders, in order to replace the placeholders with their corresponding values. However, in versions of the library dating back to 2018, some default lookup instances included evaluations that could result in arbitrary code execution or contact with remote servers.
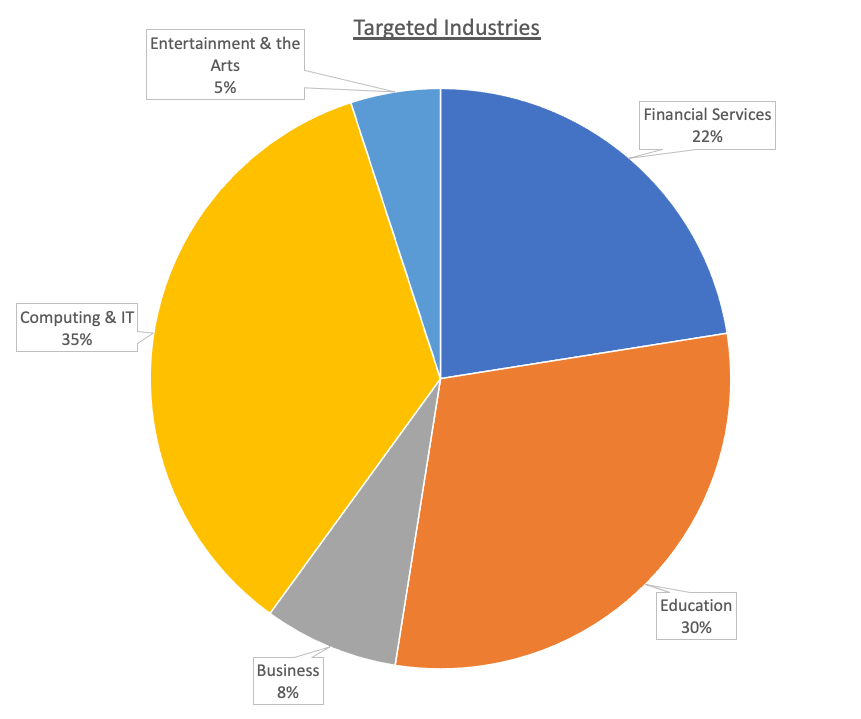
Imperva Threat Research began observing attacks using this vulnerability pick up on the 18th, and attacks are continuing to rise but still not at the rates of previous attacks like Log4shell or Spring4shell. Most attempts come from bots or the programming tool Typhoeus, which runs parallel HTTP requests. Most of the exploitation attempts we’re seeing include attempts to contact remote servers to identify vulnerable applications. However, we’ve also detected malicious attempts to take over vulnerable applications by opening a reverse shell using different programming languages, including Bash, Zshell, Python and Ruby. The US is the most targeted country overall, followed by Colombia and Brazil. Italy had the most attack requests per site, at about 135. Attacks targeted mainly financial, computing, and education sites, with pretty even distribution across the three industries.
Imperva customers are protected out of the box from this vulnerability. Users are recommended to upgrade to Apache Commons Text 1.10.0 or install Apache’s released patches as soon as possible. Although existing security rules addressed this vulnerability, Imperva has added dedicated, specific rules to block attempts to exploit this CVE in our CWAF and WAF-GW.
Try Imperva for Free
Protect your business for 30 days on Imperva.










