As we discussed in Part 1 of this series, Imperva’s Security Labs continuously monitor cyber threat levels around the world and report on them. In the last post, we reported the breakdown of the specific types of data that get stolen and explained what organizations needed to do to mitigate the damage that breaches can cause. In this post, we will discuss the root causes of data breaches and offer you the lessons we have learned from ten years of monitoring and analyzing the Database Threat Landscape.
For more information about the Imperva Security Labs’ data breach study and monitoring process, go back and check out Part 1 in the series. You can get the full report, Lessons Learned From Analyzing 100 Data Breaches here.
What are the root causes of data breaches?
Imperva research shows us that almost 50% of data breaches begin in the Web Application, either through a SQL injection (SQLi) or some other vulnerability like Remote Code Execution (RCE) or simple information disclosure. The Web Application is the front door to an organization’s sensitive data and a reliable Web Application Firewall can mitigate these vulnerabilities and limit their exploitation.
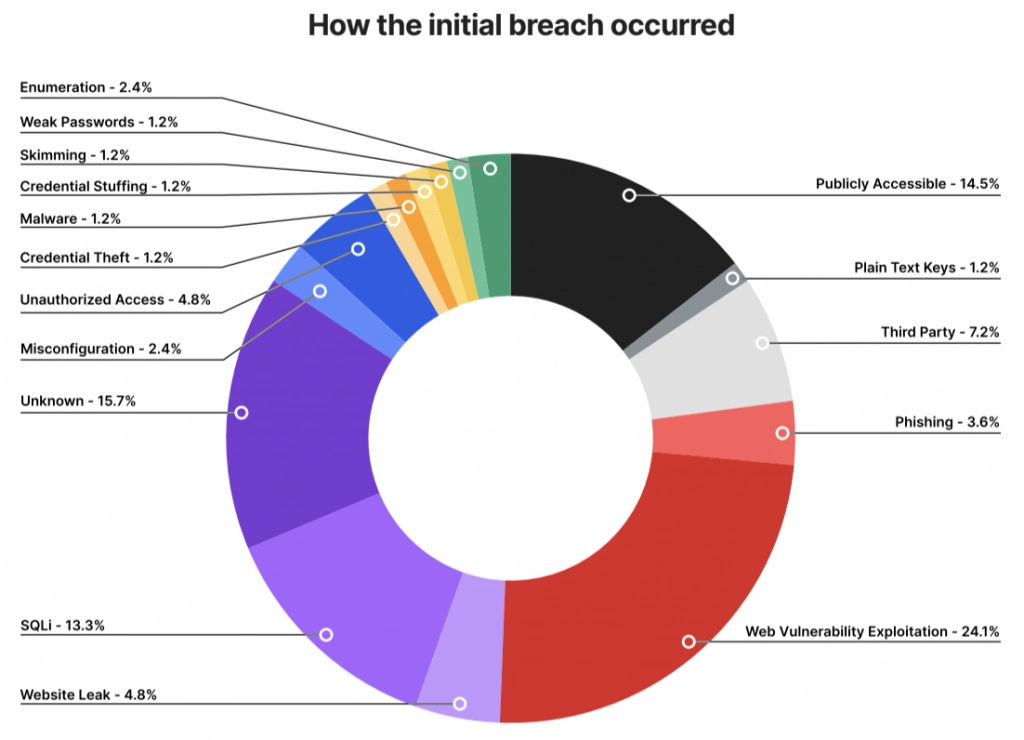
The big trend that stands out for Imperva’s research team is the 15% of data breaches whose root cause is listed as “Publicly Accessible”. A publicly open service increases the risk for a breach to happen, but in most cases this is not a failure of security practices but rather a complete absence of any security posture. For example, when there is a failure to secure non-production environments where company data may be used to perform testing. A good example of this is the 2020 Meow attack against unsecured databases. In that attack, some of the affected databases only contained testing data, but the attack also targeted some high-level victims, among which was one of the biggest payment platforms in Africa. In a 2020 article from Dark Reading, Imperva’s Senior VP and General Manager for Data Security Ron Bennatan used the high-profile Meow attack to reinforce the need for proper data security, “While perhaps not as significant or eye opening a breach as many that we will never hear about,” explained Bennatan, “the flashy Meow breaches give us an opportunity to draw attention to the major underlying issues in database security to ensure that correct measures are put in place before real damage is caused.” We’ll offer a deeper analysis of this in Part 3 of this series.
Another trend worth noting is the ever more sophisticated SQL injections that have become an increasingly popular way for bad actors to wreak havoc on organizations. The two-phase SQL injection attack on enterprise firewall company Accellion in late 2020 is a textbook example. What should be of particular concern in the Accellion attack is the brazenness and creativity the attackers employed to steal customer data, credit information, and personal data such as birthdates and email addresses subsequently to use as leverage in ongoing extortion attempts.
The growing frequency and complexity of SQL injection attacks seem to suggest that organizations still are not paying enough attention to security at the data layer. Monitoring for non-compliant, risky, or malicious data access behavior with machine learning model-driven behavior analytics and automated detection at the data level would certainly bring more up-front attention to SQL injection attacks.
Learn more about how Imperva’s Web Application Firewall mitigates the chances of data breaches beginning in the Web Application.
Try Imperva for Free
Protect your business for 30 days on Imperva.













