Executive Summary
Last summer, we investigated a massive, global phishing campaign impersonating almost 350 legitimate companies. Our continued investigation into this expansive phishing campaign revealed leaked backend source code, shedding light on the infrastructure behind the operation. This leak led us to a scammer team management platform as a service.
Through this discovery, we traced the campaign’s roots to an individual known as MrEnigman, and uncovered a broader network, operating through a Telegram channel called Haron_rent.
In this article, we go into detail about this project and its capabilities in order to provide more understanding of how the actors of this campaign operate behind the scenes.
Recap
In our previous blog, we delved into a sophisticated phishing campaign designed to mimic the popular Israeli second-hand marketplace, Yad2. A colleague’s innocuous attempt to sell a car seat exposed us to this elaborate fraud. After engaging with what seemed like a legitimate buyer, he was directed to a counterfeit payment portal, cleverly disguised with Yad2’s familiar branding and aesthetic.
Our investigation took a deeper dive by leveraging open-source intelligence, which we used to visualize the network of domains, IPs, and URLs. We revealed thousands of domains and tens of thousands of URLs.
Through static and dynamic analysis, we understood the interaction between the scammers’ server and front-end, ultimately exposing more of the operation’s deceptive tactics.
A Mysterious Leak
Our journey into the depths of this phishing campaign took an unexpected turn when we stumbled upon leaked backend source code associated with the campaign we originally analyzed in August 2023. Below, we describe this project in detail based on the analysis of the source code.
Scamming Platform Simplified Infrastructure
The leaked source code revealed that the project is composed of two different node servers.
One of them is the web server exposing the phishing content we described in the previous blog.
The second server is a NodeJS application using the telegraf library. This library enables the application to interact with a Telegram bot. This server uses CloudFlare API to dynamically associate newly registered domains with the phishing servers to make the operation more evasive.
All relevant information – such as credit card numbers, phishing links and fake profiles – are being stored into a MySQL database.
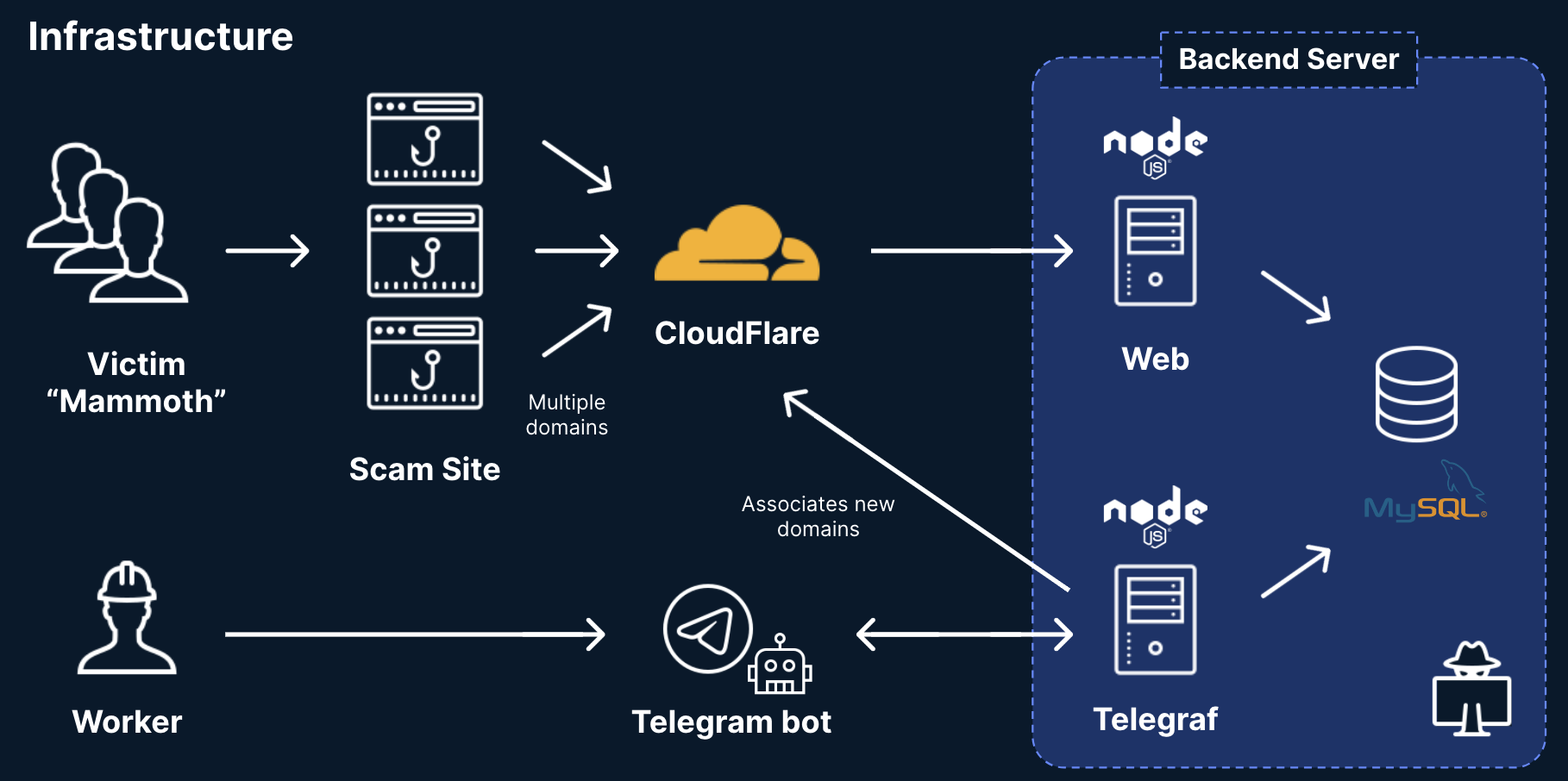
Figure 1: General infrastructure
But before we start digging into the capabilities of this platform, let’s talk a bit about the attackers behind this operation. When we first investigated the phishing page, we were eager to discover who was behind this operation, and how they operate behind the scenes.
Unmasking the Mastermind: MrEnigman
During the review of the leaked source code, we discovered a link to the private repository of an individual known as MrEnigman.

Figure 2: Mention to MrEnigman’s repository
Searching this actor led us to an underground forum, where we found an advertisement for a scamming team management platform.
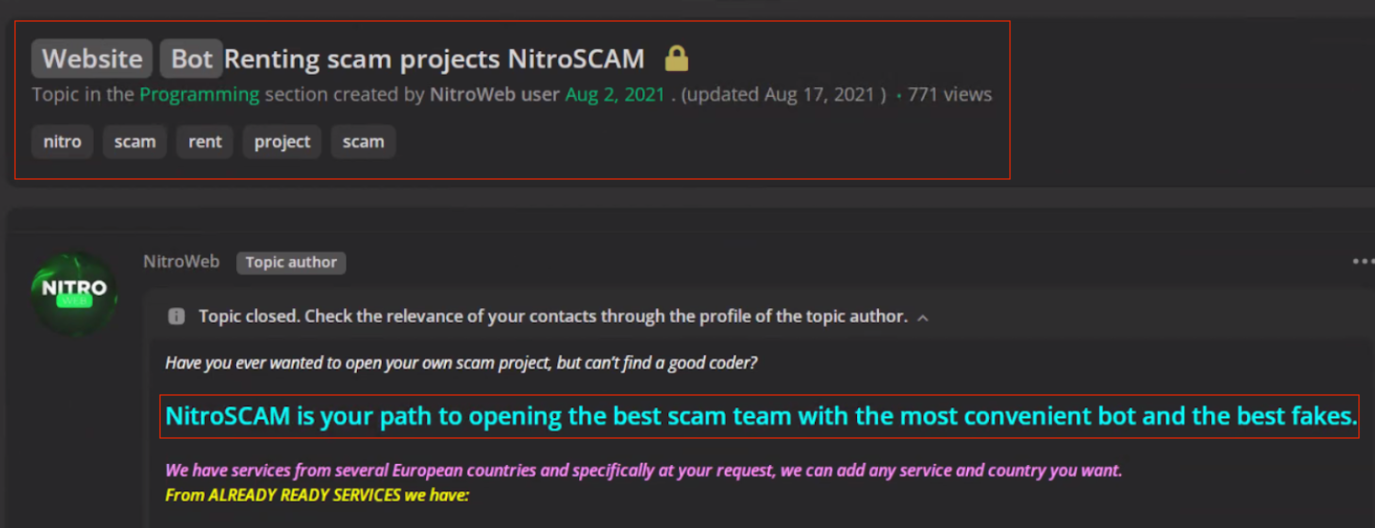
Figure 3: Underground forum advertising a “scam team project”
The ad redirected us to a first Telegram channel called @nitroscam that eventually led us to a Telegram channel named Haron_rent, which boasted around 400 members. This channel provided significant insights into the scale and the inner of this phishing campaign.

Figure 4: Haron_rent advertisement
The channel featured videos detailing the step-by-step process of generating phishing links, offering a glimpse into the tools and techniques employed by the scammers.
We noted that the leaked code was posted the same week the Telegram channel posted a message announcing the end of collaboration between the platform owner and a developer due to disagreeing “moves”. Although the origin of this leak remains unknown, this suspicious timing leads us to suspect it may have been leaked by the disgruntled developer.

Figure 5: Possible origin of the leak
Profiling the Threat Actors
From the information found on the channel, we were able to understand the following elements about these threat actors:
- They’re most likely Russian, as the only language used in the Telegram channels is Russian and the currency mentioned to rent the platform is RUB.
- The workers operate as scamming teams and even as communities. Indeed, the platform provides the ability to register teachers and mentors for new scam workers.
- The platform is proposed for the price of $100 per month. Therefore, the entry bar is definitely accessible for a small team.
- It seems that the community is composed of youngsters young adults, since the vocabulary used in the channel include a lot of slang and colloquial terms ( e.g. “нахуй” (damn), “ебашим” (working hard), “плотнейший ворк” (tight work), and “чувихи” (girls))
The Scale of the Campaign
The discovery of the Haron_rent channel, with its hundreds of members– each of them possibly managing a team– provided a good explanation for the massive scale of the phishing campaign.
By pursuing the investigation in Telegram channels and bots, we were able to discover several scam teams using this platform. Some of them gathered more than 500 members.
From the messages on these channels, it appears that many scammers were able to generate more than a few thousands dollars.
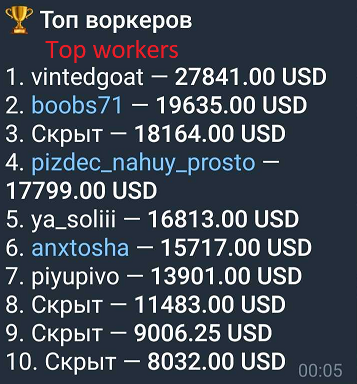
Figure 6: Top earners from one channel
Therefore, based on the numbers above, it’s reasonable to estimate that the market associated with this type of scam is measured in tens of millions of dollars at least.
The organized and professional approach, combined with the efficient tools at their disposal, highlights the significant threat posed by these cybercriminals.
The Telegram Bot Project
The leaked source code revealed that the project was, in fact, a NodeJS application using the Telegraf library. This library enables a Node application to interact with a Telegram bot. This architecture enables all threat actors to rely on the security and anonymity provided by Telegram.
The victim is usually referred to as “the Mammoth”, potentially to relieve guilt from the scammer. This is a practice we already reported in our previous blog post. Below is shown a simplified graph of the infrastructure of the scamming platform.
The general workflow is the following:
- The potential scammer submits an application to be part of a scamming team.
- The administrator of the team validates the application.
- The potential scammer becomes a worker and can now generate phishing links customized for specific victims.
- The worker shares the phishing link via a 3rd party application, for example SMS or WhatsApp.
- Then, the worker can interact with the victim via a fake “support chat interface” through the Telegram bot.
- The victim falls into the trap and shares his private details.
- The administrator has access to all stolen information and pays a percentage to the worker via his cryptocurrency wallet.
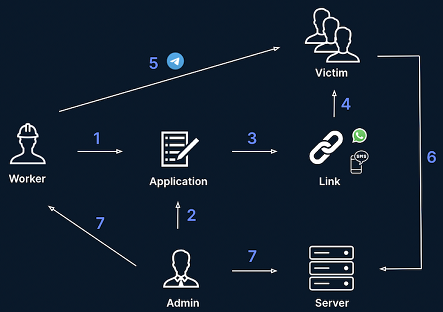
Figure 7: General workflow of the scammers
In the following sections, we will cover the workflow main steps.
Scam Worker Recruitment
First of all, there is an interface to enable a vetting process of recruiting new members into a scam team.
The following questions are asked prior to the recruitment process to evaluate the reliability of a candidate. Then, the administrator needs to accept the worker’s application.
| Russian Text | English translation |
| В каких командах работал ранее? | Which teams have you worked in previously? |
| Общая сумма профитов? | Total sum of profits? |
| Откуда узнал о команде? | How did you find out about the team? |
Once the application is accepted, the worker has access to the main worker interface.
Initial Bot Interface
Once the vetting process is successfully achieved, a worker has access to the following minimalist interface. From there, he can generate phishing links associated with a customized scam page, manage them, and interact with the victims through a dedicated Telegram interface.

Figure 8: Screenshot of the main worker interface showcasing its functionalities
For the administrator the interface includes many more capabilities like workers or mentors registration and management, domain rotation, etc. It is displayed below:

Figure 9: Administrator panel
Phishing Pages and Links Generation
To generate a phishing link, the scammer needs to create a fake profile that will be used to interact with the victim. Then, the steps are straightforward. Eventually, the pages associated with the generated phishing links look like the following:
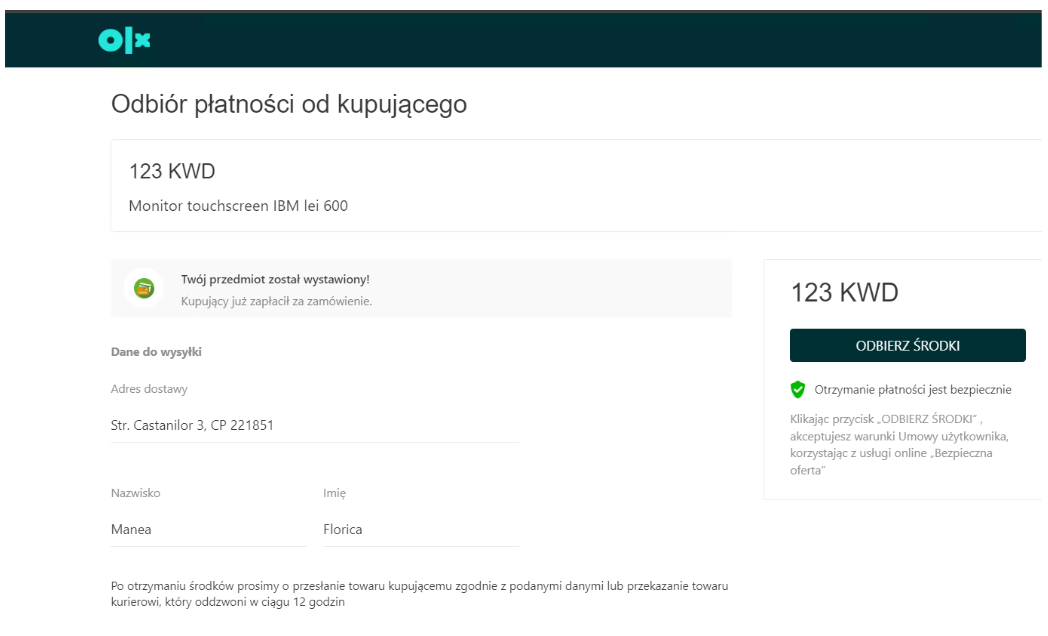
Figure 10: OLX Phishing page in Polish

Figure 11: Posta phishing page in Hungarian
Interactions with the Victim
The Telegram bot provides notifications when the victim is on the phishing page, and enables the worker to send and receive messages through a deceptive support chat. You can see it live in the following video.
Data Management
Once the victim falls into the trap, his information is shared in a dedicated Telegram Channel, and stored in a MySQL database. In addition, this database stores information regarding the deceptive the ad, the fake profiles generated by the worker and all relevant information as you can see below:

Figure 12: Stolen Credit Cards
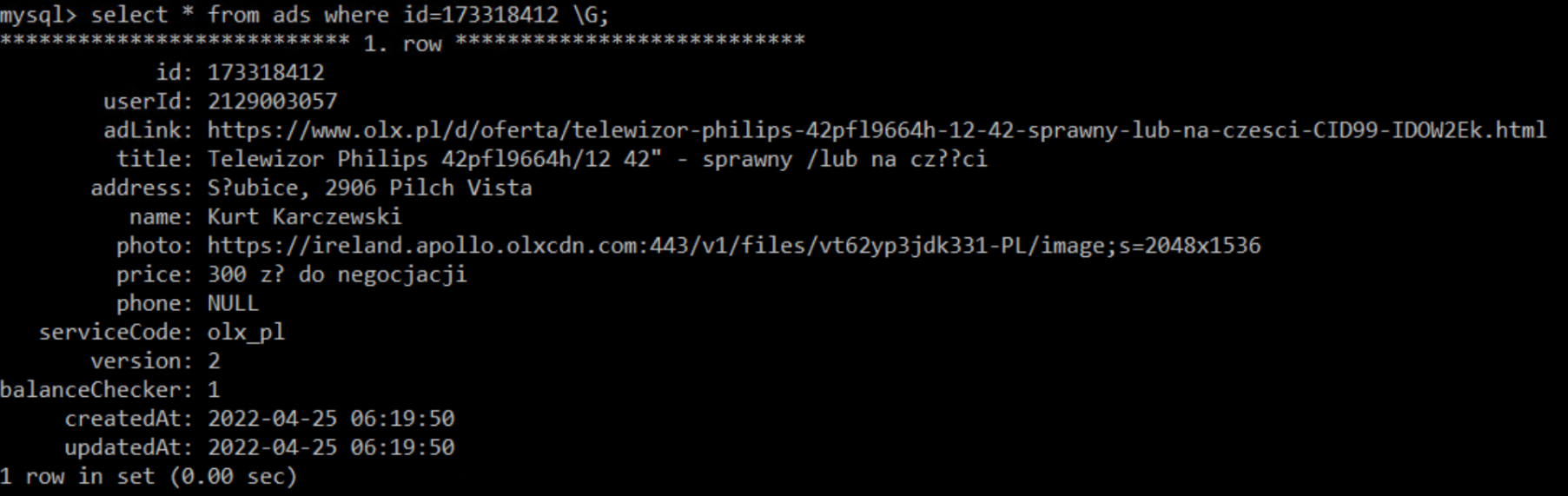
Figure 13: Phishing ads, leading to scam page
Workers Management
The worker receives a percentage of the amount stolen from the victim, depending on the platform’s configuration. The administrator is responsible for managing workers, profits, scam domains and so on.

Figure 14: User management page from the administrator panel
Mentors Management
The platform also includes a mentoring function, where more experienced scam workers can support new members. In addition to enabling continuous improvement of the scammers’ social engineering techniques, it creates a kind of community spirit and an incentive to recruit more scamming workers. This makes the operation even more effective.
Conclusion
All of these components of this platform contribute to the efficiency of the platform. Our investigation in Telegram channels showed teams using this platform including more than 500 members.
Yara Rules
The YARA rule is provided for informational purposes only. It is not intended for use without first being validated through your organization’s own internal testing to ensure appropriate performance and detection rates. We are not responsible for any issues or damages that may arise from their use. Not all files of the campaign are covered by it.
rule Hunting_Haron_Rent_1
{
meta:
author = "yohann.sillam@imperva.com"
sha1 = "17840f9c9c492493d8a6e5cf6e2940e587e048d3"
date_created = "2024-06-19"
rev = "1"
context = “Searches for JS artifacts of Haron_rent phishing scripts”
strings:
$s1 = "testSDNservsssfg.com" ascii wide
$s2 = "/root/create-bank" ascii wide
$s2 = "/root/create-platform" ascii wide
condition:
all of them
}
Summary
This second episode in our investigation series delved into the details of the infrastructure behind the large-scale phishing campaign presented in our last blog post. It also presented the workflow and the profile of the threat actors behind it.
Our team is committed to continuing the investigation to uncover more details and ultimately shut down this operation. We will keep monitoring the activities of this threat actor and provide updates as we gather more information. Stay tuned for more updates as we delve deeper into this malicious operation.
Imperva Threat Research remains at the forefront of tracking and combating evolving cyber threats. Our team of analysts, researchers, data scientists, and security engineers is dedicated to protecting our customers and informing the broader community about emerging threats.
Try Imperva for Free
Protect your business for 30 days on Imperva.











