The digital application landscape is evolving rapidly, with APIs as the backbone of modern software development. However, amidst all this innovation lies a silent menace: the prevalence of unknown APIs. These APIs, often lurking beyond sanctioned channels, pose significant security risks to organizations. From shadow APIs born of good intentions to not fully deprecated endpoints harboring vulnerabilities and unauthenticated APIs exposing sensitive data, the dangers are many.
Shadow APIs: Unseen Threats Lurking Within
A shadow API, also referred to as an undocumented API or undiscovered API, is an API that operates outside the official and monitored channels within an organization. A shadow API, born from well-meaning intentions of previous software versions, poses a notable security risk if manipulated and exploited by threat actors. This risk extends to compromising sensitive data, potentially leading to breaches and non-compliance. Recognizing the need for comprehensive security measures, Imperva API Discovery plays a crucial role in shedding light on previously overlooked APIs.
Data from Imperva’s State of API Security report reveals an average of 29 shadow APIs per account, emphasizing the pervasive nature of this security challenge. API discovery emerges as a pivotal first step in developing a robust API Security strategy, ensuring organizations have a complete understanding of their digital landscape.
Deprecated API Endpoints: An Unexpected Risk
A deprecated API endpoint refers to a specific route or URL within an API that has been marked for removal in future versions of the software. When an endpoint is deprecated, it means that the developers or maintainers of the API have decided that it should no longer be used because it may have security vulnerabilities, outdated functionality, or better alternatives available. However, despite being marked as deprecated, the endpoint might still remain accessible and functional within the API for a certain period. This could happen for a number of reasons, including providing legacy support or the slow adoption of the newer version of the API. However in some cases, endpoints are simply overlooked during the development or maintenance process, overlooked leading to their continual presence within the API. The presence of deprecated API endpoints over a prolonged period of time raises significant concerns, primarily due to their potential vulnerability to known exploits that have been addressed in newer versions. Failing to retire these endpoints after a time can expose systems to exploitation by malicious actors, amplifying the risk of security breaches and compromises. Outdated APIs often lack the security updates present in more recent alternatives.
To mitigate the risks tied to API endpoints that haven’t been fully deprecated and are still present within your application architecture, security teams should conduct regular audits, identifying and retiring these endpoints within their systems. Continuous monitoring becomes a critical tool to detect any attempts at exploiting vulnerabilities associated with these aging APIs. Developers play a pivotal role in this process, encouraged to prioritize regular updates and upgrades, ensuring deprecated endpoints are replaced with more secure alternatives.
Imperva API Discovery analysis highlights an average of 16 deprecated endpoints per account, underscoring the urgency of addressing this lurking threat within organizational ecosystems.
Unauthenticated Endpoints: Balancing Development Speed and Security
An unauthenticated API endpoint is a route or URL within an API that does not require any form of authentication or authorization for access. In other words, clients can make requests to these endpoints without needing to provide any credentials or tokens to verify their identity or permissions. Unauthenticated API endpoints are a common occurrence driven by the need for streamlined development, often prioritizing functionality over security during the initial stages. These APIs may also stem from older software versions, lacking robust security measures persisting over time without proper authentication protocols as systems evolve.
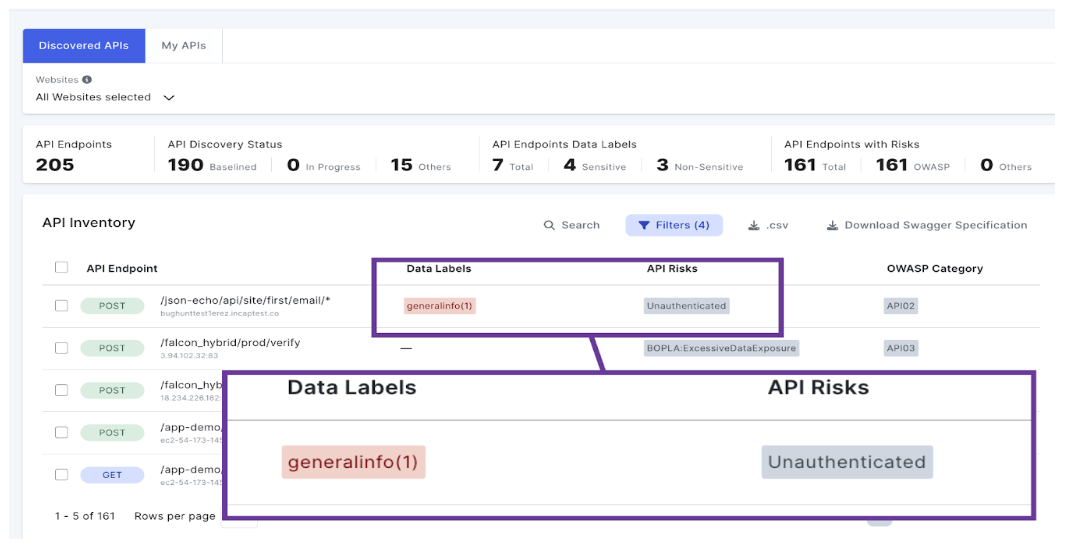
Example of an Imperva API Discovery dashboard uncovering unauthenticated API endpoints.
The existence of unauthenticated APIs poses a substantial risk to organizations, potentially exposing sensitive data or functionality to unauthorized users and leading to data breaches or system manipulation. Authentication mechanisms that are not implemented correctly make it possible for attackers to exploit flaws and assume other user’s identities. This compromises the overall security of the API. Broken Authentication is such a major threat to APIs it is listed as the number 2 risk in the OWASP API Security Top 10 threats.
Imperva’s API discovery process reveals an average of 21 unauthenticated API endpoints per account, highlighting the need for organizations to bridge this security gap and increase security measures.
In conclusion, the risks associated with unknown APIs demand a proactive and comprehensive security strategy. Monitoring through continuous API discovery and risk assessment, and identifying and protecting sensitive data as part of a holistic platform approach to API Security, which includes WAF and Advanced Bot Protection, will go a long way to safeguard against the risks posed by shadow APIs, and deprecated and unauthenticated endpoints..
The risks of APIs lacking sufficient authorization and access checks are discussed in our webinar ‘Build a Robust API Security Strategy’, available to download here.
Visit the product page to learn more about Imperva API Security.
Try Imperva for Free
Protect your business for 30 days on Imperva.












