Key signs to look for in today’s complex data threat landscape
Introduction
The most vulnerable data repositories are the ones deep in your organization’s infrastructure. Everyone assumes they are safe, but as with your home, organizations must invest in security at entry points. Otherwise, the result is unsecured valuables lying around out in the open or easy to find in obvious closets or drawers.
What happens to security when someone known to the homeowners, like a plumber, gardener, or friend, has access to the house? It becomes much easier for other people to exploit the homeowner and access the property.
The same principle applies to organizations. They deploy most of their security strategy on the perimeter and leave their “deep” data repositories vulnerable to data breaches. Bad actors have the opportunity to exploit organization insiders or third-party software components. A 2022 Forrester report revealed that 58 percent of sensitive data incidents are caused by insiders, either from non-malicious mistakes or deliberately malicious actions. The report also revealed that 82 percent of organizations do not have an insider risk management strategy or policy. It doesn’t, however, have to be this way.
Your data repositories contain the sensitive personal data of your business, employees, and customers, and, much like the valuables around your home, you should have a security strategy to safeguard them effectively. Staying with the home security metaphor, you need to consider turning the containers of your valuables into secure vessels, minimizing the number of people who could secure access, and gaining the ability to inventory losses when they happen. In data security, this means encryption, minimal entitlements, access control, and advanced analytics. Forrester data suggests, however, that not all organizations understand how to create an effective data security strategy, and their biggest mistake is not effectively addressing the insider threat.
Two critical business trends contribute to the ease with which bad actors can sneak undetected into your organization’s infrastructure and breach sensitive data, and we address them in this post. Next, we’ll explain general data breach attack flows and profile typical attackers to help you gain a better understanding of who and what to look for. Finally, we’ll make some recommendations on how you can integrate a modern data security fabric with existing tools to create an effective, sustainable data security strategy.
The cost of an intruder who has access to the “house” on an ongoing basis cannot be overstated. Every day, bad actors can exploit your vulnerable data repositories and your structured, semi-structured, and unstructured data to exfiltrate the sensitive information for which you are responsible. This can easily play a role in the data exfiltration process by acting as temporary storage or a proxy to transport the data from a secure environment to an unprotected environment and then to the outside. This is the essence of a data breach – a successful attempt to open the closet or “crack” the safe and expose the sensitive personal data contained in it.
Two business trends make organizations vulnerable
- The need to integrate with external technology providers. Some CISOs and their team members struggle to secure a business services environment, which becomes additionally challenging as business operations agility grows.
- The evolution of cloud computing. As organizations transition to the cloud, they are using third-party cloud-managed computing environments and third-party SaaS services to accelerate the migration process.
Data breaches are far more common today because of third parties
Relying on third party code and services providers means that an organization’s information technology infrastructure is exposed to suppliers that do not have a robust data security strategy aligned with the organization’s own. The risk becomes much greater as every third-party technology provider’s security vulnerabilities, in effect, become yours.
The first step for CISOs and their security teams is to secure all sensitive data assets and gain complete visibility into all data repositories that are part of the organization’s architecture. This includes legacy repositories deep in the architecture and new ones, in on-premises and cloud-managed environments. Even data repositories that you don’t know exist yet. When you have that level of visibility, then you can evaluate vulnerabilities, figure out who should have privileged access to the repositories and why, then optimize your detection and response process to deal with potential breaches.
General data breach attack flows
Most data breaches have common characteristics, no matter the details of the breach. First, the attacker needs to penetrate the organization’s IT (Information Technology) or OT (Operational Technology) environments, look around and find the asset of interest that it can take.
Examples of Early Signs of a Data Breach
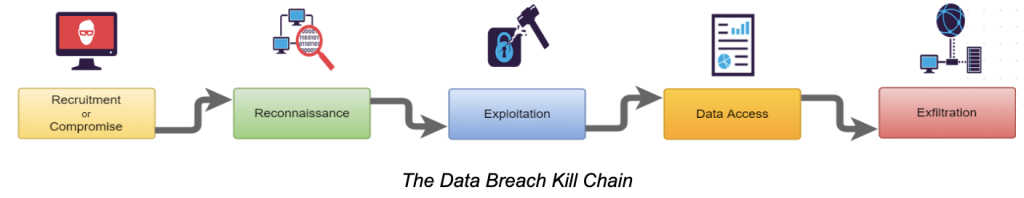
Signs in critical stages:
Reconnaissance:
- System tables scan
- Massive database scan
- Multiple login attempts
Exploitation:
- Open command shell
- Machine takeover
Data Access:
- Service account misuse
- Retrieving high numbers of records
- Accessing business-critical data
General Signs:
- Work/activity in unusual hours
- Use of dynamic SQL
Data breach attacker types
Hit & Run
This “Opportunist” identifies an opportunity; whether it is a vulnerability, a publicly open database, or something else. The bad actor decides to take what they can and leave. This kind of attacker will not try to search for other databases or penetrate the organization’s network, or try to execute exotic exploits, etc. They will just take what they can, and then sell it to the highest bidder.
The Curious
This attacker usually sets out with a purpose, but may decide to look deeper. They may look around a little bit, but not too much. They are still focused on their original purpose, malware deployment, data exfiltration, etc.
The Resident
The most dangerous type, as in the “Equifax” breach, the Resident will gain access to the organization’s network and will stay for months, sometimes years. They will use keyloggers, sniffers, and other methods to steal credentials and compromise databases, using “Low and Slow” and other methods to stay undetected.
Common data breach attack examples
The attacks that cause the greatest damage are ‘The resident’ attacks. Let’s consider some examples to understand how these attacks are forged.
The resident attack
Infosec disasters are typically the result of multiple failures. Invariably, post-breach analysis reveals several security weaknesses that allowed attackers to steal terabytes of information from supposedly secure systems.
There are several well-known, high-impact incident reports, such as Equifax, Anthem Inc., and the U.S. Office of Personnel Management that describe pre-breach progressions falling under this category.
Typical attack flow
- The initial hack is done via a web-facing application, one example can be the Equifax customer complaint portal and its CVE-2017-5638 vulnerability. ThreatPost: “Equifax has been intensely investigating the scope of the intrusion with the assistance of a leading, independent cybersecurity firm to determine what information was accessed and who has been impacted. We know that criminals exploited a U.S. website application vulnerability. The vulnerability was Apache Struts CVE-2017-5638.”
- Attackers exploit weaknesses in the company’s security posture, notably the lack of proper segmentation.
- In almost all major breaches, a lack of continuous security patching of servers and databases contributes to the attack’s success.
- Unpatched servers and databases provide the resident attacker room to operate freely within the company’s network for a protracted amount of time.
- In almost all these attacks, the intruders were in the company’s environment for months, customizing their attack tools over and over again until the sensitive data was successfully compromised.
Ransomware attack
This type of attack is designed to disable critical systems or prevent sensitive data access by privileged users until a specified amount of money is paid. Ransomware attacks have become more and more sophisticated. They typically involve:
1. Penetrating the organization’s IT environment
- Malware installed on an endpoint operating system via a phishing attack.
- Account Takeover (ATO) attacks use stolen credentials to penetrate the organization’s environment.
2. Analyzing network resources to allocate databases that hold personal, financial, or business-critical information.
3. Making the original data stored unusable by:
- Encrypting the data.
- Extract data either to a hidden file in the network or outside.
- Modify data values stored.
Ransomware attack detection example
In this attack, the data is moved from the original database to a readme file.
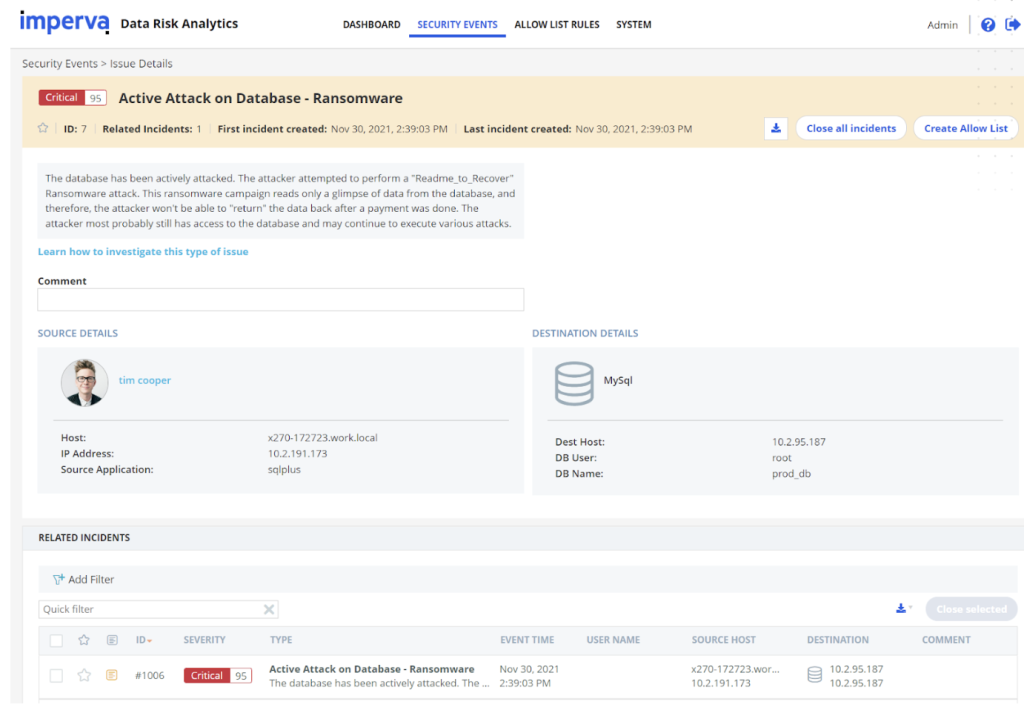
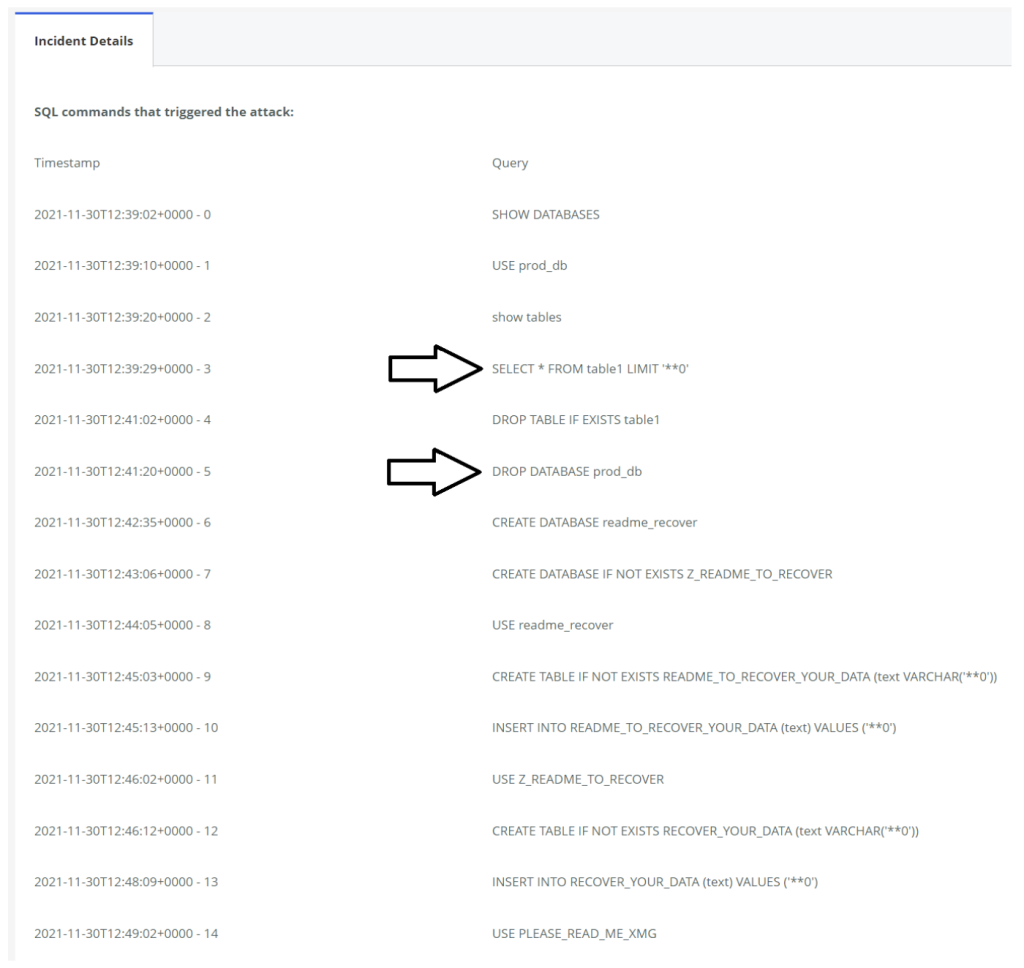
DB breach flow:
- Attacker query for databases list.
- Attacker selects prod_db.
- Data is being stolen from prod_db using the ‘select’.
- Prod_db is being deleted using ‘drop’.
How should organizations protect their home environment
Imperva research shows that much like using a safe at home, when organizations secure their data repositories with a data-centric security fabric, and when a hostile penetration occurs, they dramatically reduce data exfiltration risk by turning all open repositories into well protected alarmed enabled safes. This shortens the path from breach to detection to response.
As business innovation and the services that support it are digitally transformed, the perimeter boundaries have blurred. The “walls” that protect data repositories have cracks that allow attackers to put their hands on sensitive data, effectively ending the days of protecting assets within the network perimeter. The security of an organization is only as strong as the weakest link in the security chain. In many cases, better architecture and cross-organization security practices would do the trick, but those practices are not easy to implement and control, nor do they account for the risks presented by third-party technology providers. You must secure all the data repositories they manage, not just the applications and networks that surround them.
The cause of most breaches is the lack of an in-depth data security strategy. As we discussed before, you can reduce the attack surface by securing your data repositories, but you must gain visibility into them. Next, eliminate excessive privileges from key users and deploy strong authentication mechanisms. Never forget that securing data repositories is a never-ending process, you must always work toward optimizing your security architecture, policies, and practices, both for your assets and employees. Continuously performing data discovery and classification to locate sensitive personal data is a great way to maintain an enterprise-grade data security strategy and eliminate bad practices inside on-premises and cloud-managed environments. Together with implementing Imperva’s Web Application Firewall (WAF) and Imperva Data Security Fabric, it is possible to protect against most potential data breach scenarios.
On-Demand Webinar: Detecting Attacks on Your Data. How can we do it right?
Security Analytics are an essential part of the toolkit to protect against data breaches. Are you using Imperva Data Risk Analytics (DRA)? Imperva Data Risk Analytics tools have been purpose-built to recognize threats such as suspicious data access or signs of potentially compromised accounts. But did you know Imperva recently added new features that can recognize the attack signatures of active exploits so you can be instantly notified of an attack in progress?
In this webinar, Product Manager Oren Graiver, will describe how you can use Imperva Data Risk Analytics to augment Imperva vulnerability assessment and data activity monitoring and transform your security posture to proactively prevent data compromise incidents. Topics covered will include:
- Where breaches are found
- Understanding data breach detection
- Early signs of a breach
- Kill chain and data compromise
- Real life example of a breach DRA can detect – Ransomware
- What’s on the roadmap?
Try Imperva for Free
Protect your business for 30 days on Imperva.






