A recent IDC survey reported that 38 percent of organizations identified cybersecurity threats and regulations as the factor having the greatest impact on their technology investment planning over the next two years. The survey also revealed that for organizations taking a digital-first business approach, unifying security was cited most frequently as their principal motivation. This makes a great deal of sense; unified security technologies enable organizations to more effectively address new cybersecurity threats, data privacy, and digital sovereignty requirements.
IDC also reports that many enterprises believe APIs are key to future innovation. Today, one in four businesses derive at least 10% of their overall revenue from APIs and IDC expects that number to increase going forward. However, 27 percent of those businesses cite security, privacy, and compliance concerns as the principal barriers to more widespread adoption of APIs. Businesses are specifically concerned about the loss of control over APIs in innovation-accelerating environments such as an open ecosystem approach to development.
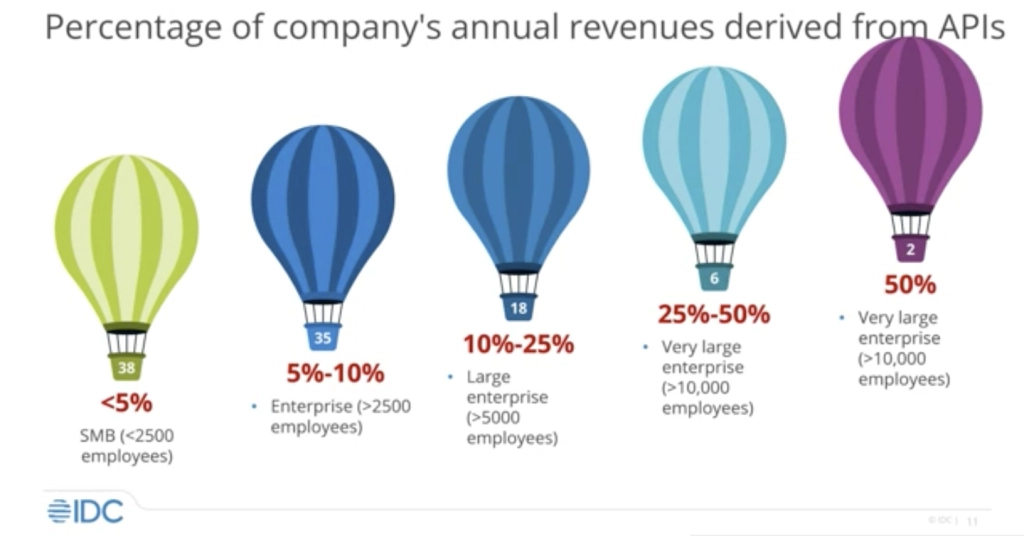
Figure 1: Percentage of company’s annual revenue derived from APIs. Source: IDC
The bottom line lesson to take from these findings is that while many organizations see APIs as critical to accelerated development, they are concerned about cyber threats and are investing in unified security technologies to overcome security, compliance, and data privacy challenges. Building an effective security system enables them to mitigate threats and leverage APIs into more revenue opportunities. In this post, we’ll articulate the threats posed to API security, and explain how organizations have managed these threats in the past and what they need to do differently to secure APIs in the future.
Prioritizing API risk and security
The most visible threats to API security are misconfigurations and DDoS attacks. Code injection and other OWASP Top 10 API-specific threats are less well known today. It is likely that bots, data leakage, fraud, and abuse may be overlooked owing to the current, fast-moving, cybersecurity landscape, but these threats are real. Threat actors target cracks in the armor. Two-thirds of the API security incidents analyzed involved improperly configured APIs and more often than not resulted in sensitive personal data leaks. When considering API security, known vs. unknown usage, public- vs. private-facing, sanctioned and controlled vs. unsanctioned and undocumented, are all important variables.
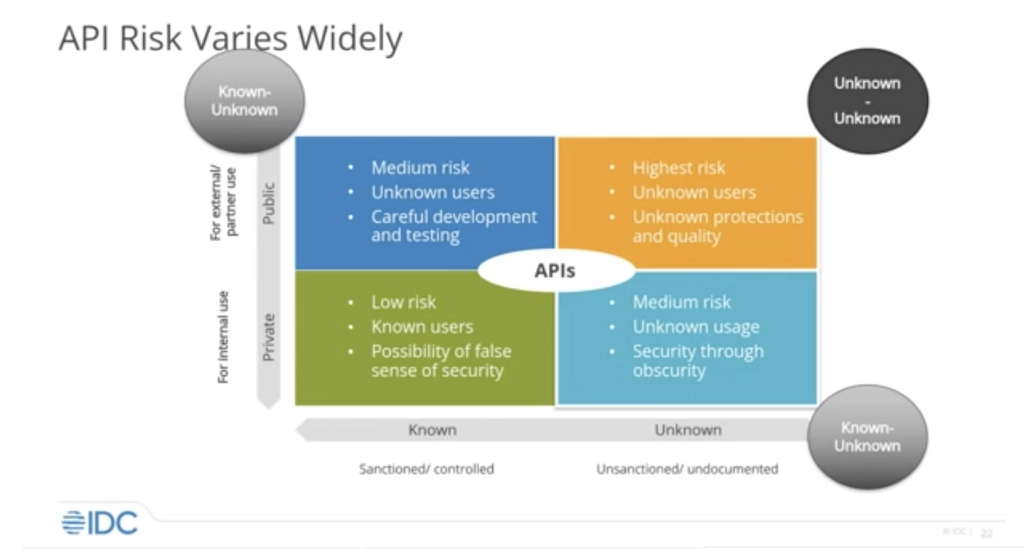
Figure 2: Prioritizing API security risk. Source: IDC
API security beyond WAAP
API Access Management Gateways are commonly offered as part of an API Management Solution. Many gateways include an extensive list of API management functions, such as data transformation, call routing, and queuing, that are not commonly recognized as security functions. Some of the security-related features of API Access Management Gateways focus on access authentication/authorization, some level of rate-limiting, and call validation.
In recognition of the critical role the Web Application Firewall (WAF) plays in protecting APIs, WAF is evolving its product category name to Web Application and API Protection (WAAP). Besides WAF features such as Bot Protection, DDoS Prevention, an API-specific feature implemented in today’s WAAP is API Schema Validation. For a security specialist who can obtain up-to-date API specifications, the operator can upload them to a WAAP to validate API requests. The issue is that not many security people can find accurate API specifications, let alone have them updated by DevOps because they change their API implementations so frequently. In reality, most security teams today are implementing a WAF+API Gateway combination, not a true WAAP.
API security is designed to see all the specialized requirements of APIs automatically. API security provides a more complete view, including detecting shadow APIs, data discovery and profiling, advanced protection against bad bot attacks, automated online fraud detection, and next-generation security analysis. APIs are designed to communicate quickly and efficiently and deliver a frictionless experience. To accomplish this performance level, organizations require holistic application security that includes API gateways, WAAP, and specialized API security solutions that deliver the aforementioned functionality.
3 steps to managing API security successfully
- Embrace a division of responsibilities. Whenever possible, security should be “baked in” to the API at the coding stage. When it is not, you need a dedicated independent security team and a solution to ensure that security is implemented properly after the API is created.
- Foster collaboration rather than competition. DevOps and SecOps teams will often have competing requirements and priorities. DevOps prioritizes speed to release. SecOps prioritizes security upon release. Management must use relevant metrics and KPIs to ensure a balance has been achieved between the needs of both groups.
- Security platforms are a must. Organizations need integrated, multi-function, unified solutions to manage all threat vectors that challenge application and API security.
To learn more about API security from industry experts, watch the on-demand webinar, API Security: Demystifying Risks of the Next Big Attack Vector with Lebin Cheng, Head of API Security at Imperva, and Chris Rodriguez, Research Director, Security and Trust, IDC.
Try Imperva for Free
Protect your business for 30 days on Imperva.












