Imperva Snapshot is a free AWS RDS security assessment tool. You can use this tool to gain in-depth visibility into your data and get a deep understanding about what data resides in your RDS and where your RDS database security gaps are. Acquiring this intelligence is a key element and critical first step toward achieving safe cloud migration and usage. Addressing your security gaps while at the same time knowing if specific data is sensitive will prevent cloud security incidents which typically have severe outcomes. For more on this, check out my last blog.
Imperva Snapshot generates meaningful insights with zero performance impact on your environment. Sounds like magic, but we’ll pull the curtain up on how it works in a future post.
Upon a scan completion, Imperva Snapshot generates a report that includes insights in three categories in which security admins and cloud operators need to pay attention for alerts: Misconfiguration & bad practices, vulnerabilities, and sensitive data.
The correlations among these three categories provide a unique glimpse into your database security posture and help you understand which data is at risk.
This post will demonstrate how to read your Imperva Snapshot report, help you understand what each of the sections includes and explain how to get the most value and insights from the Imperva Snapshot tool.
Executive summary
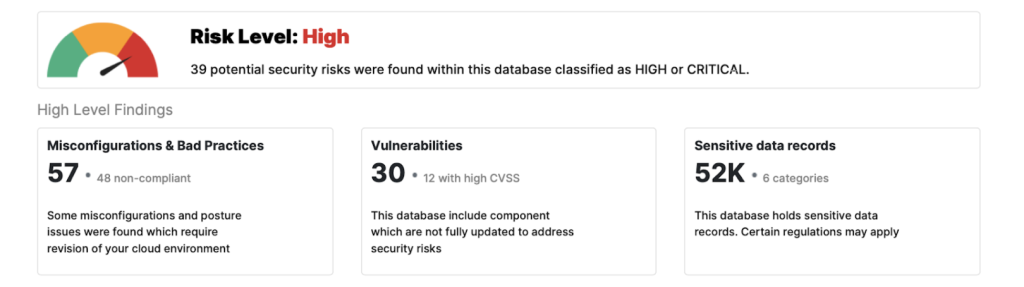
The Imperva Snapshot summary provides an immediate capture of your recent data security assessment. The image captures in the rest of this post indicate the health level as well as a high-level security posture status for each category.
This one glimpse enables you to understand where your focus should be and allows you to get a quick assessment of your database security posture.
Report breakdown by category
The first section shows misconfiguration and bad practices. Human error is the root cause of many cloud incidents, and these errors often occur during the deployment or configuration process.
The Imperva Snapshot runs hundreds of assessments on the database during the test; including auditing, access, resource control and password protection, to name a few. Tests that match your database are labeled as assessments and those assessments are classified based on the results. In the example below, out of the 125 total assessments there are 34 misconfigurations, 23 issues that require attention and about half of the tests have no issues. You can also find a severity breakdown for the security risks. Lastly, the section includes the total of non-compliance assessments found, based on some of DISA & CIS compliance checks, In the example below, there are 48.

Continuously, those alerts are gathered per assessment category. For the top misconfiguration you have specific details and severity labels. This can also be found on the report appendix, which includes more technical information.

The second part of the Imperva Snapshot examines CVEs. You will find a list of all unpatched CVEs on your database and their severity. Critical CVEs are usually vulnerabilities that require your immediate response.
You will also find a vulnerability breakdown by year. Older CVEs mean outdated databases which represent higher vulnerability risk to your security posture. That means the CVE was probably weaponized and its exploit code mechanism is very likely to be widely spread.

The last category is dedicated for data, sensitive records, and compliance issues.
Initially one needs to know the volume of sensitive records stored in a database. In the example below 2% of the database tables are sensitive, which is represented by 52K sensitive data records out of 14M stored records. Those records are then categorized and labeled based on columns and total number of records.
You will also find dedicated visibility for personal data, based on PCI & Personal Data. In cases where Personal Data was detected, GDPR and CCPA compliance standards may apply, based on the location of the data and where it is being accessed from.

We can now see the correlation between risks and data. As data experts, Imperva’s engines can read the content, identify, and classify it. As an admin you will know what the risk level on your security posture is. And you will also know what data is on the edge to be exposed. Armed with this intelligence, you can set a clear mitigation plan and prioritization.
The last and more technical section of the report is the appendix. In which you can find a description and labeling for each one of the assessments over all the categories. This explains the issue of each assessment and provides high-level mitigation suggestions for closing those security gaps.

For further inquiries and support you are welcome to reach out through email to imperva-snapshot-support[@]imperva.com or through the support team.
Try Imperva for Free
Protect your business for 30 days on Imperva.



