Extortionists target industries with most to lose from an outage
Cybercriminals continue to target organizations threatening Denial of Service (DDoS) attacks in exchange for a ransom payment, traditionally demanded in bitcoin (BTC). And it seems that no matter how many times these ransom threat cycles come around, organizations are still struggling to prepare for and protect against such an attack.
InfoSecurity Magazine reports that the 11 biggest ransom DDoS attacks of 2020 resulted in the attacked organizations spending nearly US$144 million to pay a ransom, investigate and rebuild their applications. Using more sophisticated and diversified attack vectors, cybercriminals executed 50% more ransom DDoS attacks in the third quarter of 2020 versus 2019.
Imperva has helped many customers mitigate and understand how to navigate this type of extortion-based threat to ensure they do not lose valuable downtime or experience any disruption as a result. In our White Paper Protecting Against Ransom Denial of Service Attacks we outline how to protect your business in the event of an extortion-based ransom DDoS (RDoS) attack.
The first wave of ransom DDoS threats occurred in September 2020 when Imperva reported a major ransom campaign with a serious spike in the number of ransom DDoS threats affecting thousands of large commercial organizations around the world. In this first wave, the extortionists claimed a connection to notorious Threat Actor Groups Fancy Bear and Lazarus.
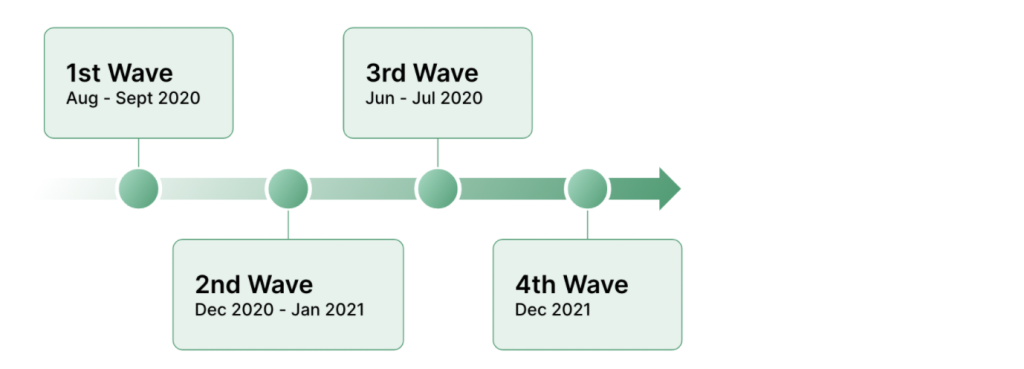
Then, between December 2020 and January 2021 ransom DDoS attacks were back again for a second wave, striking without warning and causing significant disruption to their targets. More recently, in the summer of 2021, ransom DDoS attacks reared their heads for a third time with organizations learning once again how, for a very low cost, ransom DDoS extortionists can target critical network infrastructure to cripple their businesses.
To differentiate this fourth and most recent wave from the others, targets have received the threats in the form of a request in their Web Application Firewall (WAF) platform or in the form of a SIEM request. While we have seen online forms being used to communicate ransom demands before, this is the first time we’ve recorded threats sent via a SIEM.
This example message below, which has been edited to remove the customer name, was received by a major online retail supplier in the most recent surge of attacks:
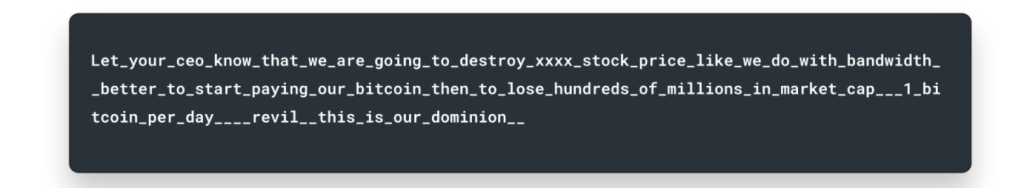
This pattern is slightly different from previous patterns where the extortionists used email to issue their demands. In this specific incident the extortionists, claiming a connection to the infamous Advanced Persistent Threat group ReVIL, sent a threat as part of the HTTP request threatening to destroy the company’s market price and cause a loss of hundreds of millions in market cap, unless they started making payments in bitcoin.
Like many previous attacks the assailants issued more than one threat demanding the ransom payment of 1 BTC, the equivalent of approximately $50,000, per day in exchange for them discontinuing the attack. The attackers launched an initial assault that lasted up to a couple of hours followed by a number of shorter attacks lasting up to 10 minutes.
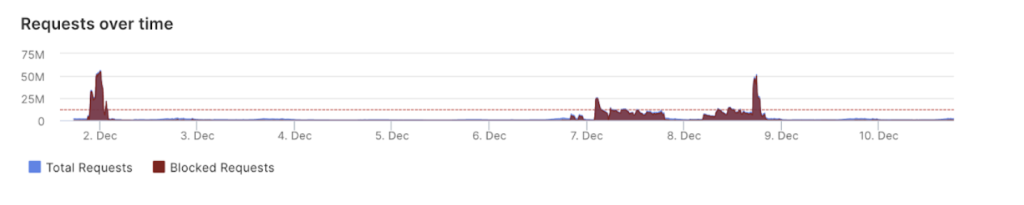
The chart below depicts how during the attack the number of requests reached 50 million in only 10 minutes with the requests per second reaching 99,000 at its highest rate.
Ransom DDoS attacks are simply DDoS attacks with an added financial consequence for targets. These attacks are incredibly easy for assailants to carry out at a very low cost. Without adequate DDoS protection measures in place for their network, the ramifications of the attack for the targeted organization can last much longer and have a more damaging financial impact.
These malicious attempts by attackers to extort your business need to be managed with caution. Imperva has produced a ‘What you need to know now’ guide to dispel some of the myths around ransom DDoS attacks and to support security teams in the event of being targeted by a ransom threat.
Not to be confused with ransomware attacks that target software vulnerabilities without your application infrastructure, a ransom DDoS threat is just what it says on the tin, a threat to disrupt your business by launching a DDoS attack to make your networks and applications fall over…unless you agree to pay up. And this is something they can do for a very low cost.
It might not cost much for a threat actor to launch a DDoS attack but when it comes to recovery the costs are high especially for those industries where an outage can cause serious damage and disruption. Take the recent example of VoIP giant for whom a DDoS attack is estimated to have cost between $9 million and $12 million for the full fiscal year due to losses incurred as a result of the outage. And these high costs are also a challenge for other high-risk industries including healthcare and financial services.
These savvy cyber criminals know which industries can least afford an outage and therefore are more likely to pay up. Take healthcare for example. In an industry where people’s lives are on the line the potential for damage beyond the initial systems recovery is much higher making them a prime target for extortionists. Likewise when it comes to the financial sector, attackers are aware of the high cost of an attack to businesses in this sector which makes financial firms the perfect candidate for a ransom threat.
FS-ISAC, a leading authority on cybersecurity for the financial services sector, published an insightful article this year on how ‘Non-Financial Risks are Increasingly Financial’. For financial firms, it is no longer enough to quantify financial risks based on markets, credit, and liquidity. In today’s digital environment non-financial risks such as fraud prevention, IT risk, and cybersecurity should also be considered. As mentioned in the article, ‘a cyber attack can not only result in operation disruption, but also customer losses, an increase in insurance premiums, lawsuits or fines, credit downgrades, and reputational damage.’
Imperva appreciates the damage that a ransom DDoS attack can do to organizations in high-risk and other sectors. And, as suggested in the Imperva 2021 DDoS Threat Landscape Report, based on our data, security teams planning their 2022 budgets should be prioritizing evaluating and improving RDoS detection and response capabilities.
As pointed out in the report, DDoS attacks are constantly evolving in size, volume, frequency, and complexity. What doesn’t change is the attackers’ focus, and that is the infrastructure that you rely on to keep your business operational. This is very true of ransom DDoS threat actors who know just how to target your critical business operations. With attack vectors evolving and becoming more sophisticated, all the time organizations need to be confident that their networks are fully protected against any type of attack and have the capability to not only react and mitigate with speed but also to recover quickly from the attack.
If you are not an Imperva customer already we recommend checking your SIEM logs for ransom threats. If you are unfortunate enough to have been targeted, and even if you have avoided being targeted on this occasion, Imperva always-on DDoS Protection for Networks gives you peace of mind knowing that attack traffic will be blocked automatically with no delays while waiting for the mitigation response to kick in. You never know when you are going to be the victim of a ransom DDoS attack but when it happens, Imperva DDoS Protection will ensure that no matter the size of the attack your business will remain up and running with no impact on your performance.
Learn more about Imperva DDoS Protection for Networks.
Try Imperva for Free
Protect your business for 30 days on Imperva.