Did you know that 86% of organizations surveyed in CyberEdge’s Cyberthreat Defense Report this year were compromised by cyberattacks?
Since the first known incident in 1989, ransom DoS attacks have become increasingly sophisticated over time. If you are not well versed on the potential threats they include, understand that: your website and network can be brought down, your staff may not be able to do their jobs, you’ll lose income derived from the services you provide, and you risk the loss of customer trust.
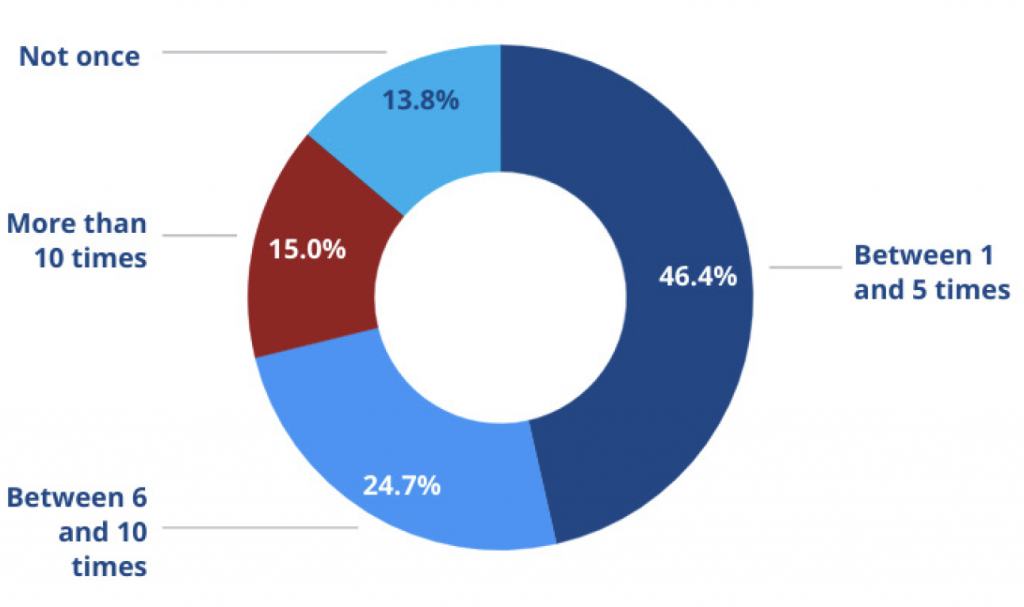
Frequency of successful cyberattacks in the last 12 months
Source: 2021 Cyberthreat Defense Report
The four stages of a ransom DoS attack
Each ransom DoS (RDoS) attack is unique, however the general approach that the attackers take have a basic pattern:
- Make contact via emails, chats with sales reps, and social media messages
- Threaten a brief demonstration attack, demonstrating familiarity with the network infrastructure
- Offer an ultimatum with a grace period — enough time to get cryptocurrency, but not enough time to mount a defense
- Warn you that the fine for non-payment increases for each day the ransom isn’t paid
The technical skills required to execute RDoS attacks are relatively low, and the tools attackers need to do reconnaissance on your networks are publicly available. Even the technology used to keep IT systems working and accessible, like search engines, make it simple for hackers to collect information about all of your network ranges and networking services, and make your systems easier to attack.
It all begins with the initial contact, which is usually addressed to several directors and key leaders in the company. Invariably, leaders will begin asking the same questions: Should we wait and see if it’s a real threat? Should we call the authorities? Should we pay the ransom? Do we understand how much they’ve infiltrated our systems?
Five common myths about ransom DoS attacks
It’s also important to recognize the common misperceptions and false assumptions associated with ransom DoS attacks, so you can conquer them and come at the problem with the best chance to overcome it.
- “Pay the ransom and they will go away.” More than two-thirds of organizations were victimized by ransomware and most (57%) paid the ransom, inevitably leading to more ransomware attacks, finds CyberEdge Group.
- “My internet service provider (ISP) will protect me.” The primary focus of an ISP is to protect their services and their other clients, your RDoS attack is not likely to be a priority for them.
- “My cloud service provider (CSP) or my infrastructure can scale to handle the load.” Scaling up only helps against the smallest attacks, and you will pay for the excessive traffic. It also won’t prevent future attacks.
- “My on-premise mitigation solution can handle it.” On-premise solutions are limited by the capacity of your ISP, require manual management and upgrades, and often fail against sophisticated attacks.
- “The attackers don’t know my infrastructure.” Your infrastructure information is publicly available and must remain this way to function.
What is the actual cost of a ransom DoS attack?
The cost isn’t limited to paying the ransom. To gain an understanding of the true costs, you must quantify factors such as the impact on web traffic, call and reservation centers if you have them, labor costs of stopping regular operations to focus on attack mitigation and recovery. And worst of all, the possibility of not recovering your lost data. These costs are likely far greater than the ransom.
Three Ransom DoS Solution Strategy Must-Haves
There are no silver bullets for protecting against ransom DoS. That said, a robust and appropriate security solution will:
- Deliver complete visibility into your data assets. If an attack does occur, your response team is immediately aware of the issue and can adjust the defense strategy as needed.
- Offer accuracy. An inferior solution could limit legitimate traffic, negatively impacting your business in a way similar to a DoS attack.
- Operate without manual intervention and leave less room for human error. Cybercriminals don’t wait to execute an attack during business hours, your solution must provide automated 24/7 protection.
The first step: plan ahead

It is critical that you evaluate the risks and understand your organization’s exposure prior to a ransom DoS attack. For example, you need to be able to quantify the potential cost of downtime that is the result of an attack. You must understand the different mitigation strategies and build a response plan that includes a partner who can help your business be resilient, even when under an attack.
For attackers, the risks are extremely low and the rewards potentially very high. As the attack surface grows along with technology advances, predictions claim that this type of activity will continue. Make sure your organization can stop it before it impacts you.
Where to go for more help
Get Imperva’s free report, Protecting Against Ransom Denial of Service Attacks today. For specific questions, contact an Imperva Solutions Consultant.
Try Imperva for Free
Protect your business for 30 days on Imperva.












