In the first two parts of this series, we gained insight into what specific types of data get stolen and what the root causes of breaches are, based on data breach information that Imperva’s Security Labs’ gathered, studied, and analyzed over the last ten years. You can get the full report, Lessons Learned From Analyzing 100 Data Breaches here.
Data breaches in open public cloud services are trending dramatically higher. This is not surprising at all. As more and more companies migrate their operations and workloads to the cloud, publicly open services just sitting out there are easy prey. This post will reveal the Imperva Security Labs’ findings on which public cloud services are used most frequently and suggest some best practices for securing them.
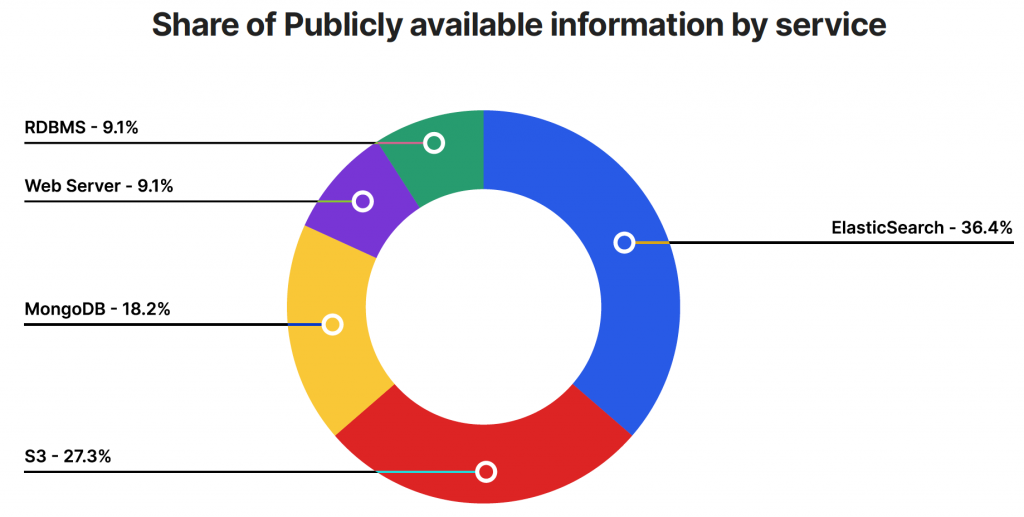
In the figure above, we see ElasticSearch as a major trending publicly open service. By nature, ElasticSearch contains big amounts of data to perform search and analysis. Since it’s a search tool and not commonly defined as a “data store” many organizations may unknowingly leave the system open to public access. There are multiple ways to target public services, from Shodan search to open source apps like LeakLocker that provide accessibility for the hunt. Even when enterprises attempt to secure them, public cloud service breaches may also be the result of cloud configuration issues, vendor defaults, etc.
A prime example of a breach in an ElasticSearch tool occurred at Autoclerk. Autoclerk, a global hotel reservation management system, had an AWS-hosted ElasticSearch database that was unsecured and exposed hundreds of thousands of bookings. Military personnel use this system heavily, and the breach revealed sensitive information about military travel, including senior officials and deployed troops.
Security researchers from vpnMentor publicized the breach, saying that they saw publicly accessible logs of US generals traveling to Moscow, Tel Aviv, and many other destinations. They also found email addresses, phone numbers, and other sensitive personal data belonging to travelers.
There are a few best practices that enterprises can employ to mitigate the risk of data breaches in their public cloud services.
Ensure data visibility
Public cloud services have many moving parts, including short-lived cloud instances and containers, elastic data volumes, and cluster-based assets (like data warehouses). If assets are invisible, you cannot protect them. Imperva’s Sonar Platform enables you to see your entire data estate, including years of retained data so you can easily monitor user accounts for policy-violating behavior.
Prevent data loss
Public cloud services are valuable targets to attack because many hold large volumes of critical information concentrated in a single repository. Imperva’s Sonar Platform ensures that you can protect sensitive structured information stored in databases, such as personal identifiable information (PII), credit card information, customer data, and medical records.
Keep your services up to date
Ensure the public cloud services you use are not exposed to vulnerabilities due to required updates or patches. This is especially important if there are known vulnerabilities that have not been resolved. In this case, the attacker knows exactly what vulnerabilities exist on your systems and how to exploit them.
Data suggests that neglect in this area is nothing less than shocking. A recent analysis of 2 million scans of 300,000 public cloud assets running on Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) revealed more than 80% of organizations have at least one neglected, internet-facing workload that is either running on an unsupported operating system or has remained unpatched for more than 180 days. The report also finds 60% of organizations have at least one neglected internet-facing workload that is no longer provided with security updates. Nearly half of the organizations (49%) have at least one publicly accessible, unpatched web server, while 44% have internet-facing workloads containing secrets and credentials that include clear-text passwords, application programming interface (API) keys, and hashed passwords that could facilitate lateral access across a cloud environment.
Audit and optimize configurations
When configuring your public cloud service, never assume you have configured it correctly. There may be configuration errors, and even if there aren’t, a configuration can change as applications and cloud resources are updated, and as workflows or users change.
Regular review of cloud configurations will ensure that no accidental changes have occurred and that any changes are safe. It also helps to identify less secure configurations, improve performance, and reduce the cost of unneeded cloud resources.
How Imperva helps protect your data
Imperva’s data security solution adds several layers of protection to your data. Imperva protects your data wherever it lives, on-premises, in the cloud, and in hybrid environments. It also provides security and IT teams with full visibility into how the data is being accessed, used, and moved around the organization.
Imperva’s comprehensive approach relies on multiple layers of data protection, including:
Database firewall—blocks SQL injection and other threats, while evaluating for known vulnerabilities.
User rights management—monitors data access and activities of privileged users to identify excessive, inappropriate, and unused privileges.
Data masking and encryption—obfuscate sensitive data so it would be useless to the bad actor, even if somehow extracted.
Data loss prevention (DLP)—inspects data in motion, at rest on servers, in cloud storage, or on endpoint devices.
User behavior analytics—establishes baselines of data access behavior, uses machine learning to detect and alert on abnormal and potentially risky activity.
Data discovery and classification—reveals the location, volume, and context of data on-premises and in the cloud.
Database activity monitoring—monitors relational databases, data warehouses, big data, and mainframes to generate real-time alerts on policy violations.
Alert prioritization—Imperva uses AI and machine learning technology to look across the stream of security events and prioritize the ones that matter most.
Want to see Imperva’s data security solution yourself? Contact us to learn more.
Try Imperva for Free
Protect your business for 30 days on Imperva.












