Domain Name System (DNS) is a very basic protocol and service that enables Internet users and network devices to discover websites using human-readable hostnames instead of numeric IP addresses. This article provides a detailed explanation of how DNS works. If the DNS service is attacked or doesn’t function properly, your service/website may become inaccessible.
In this blog, I’ll describe the main threats to the DNS service, along with mitigation techniques, and real attack data and statistics from Imperva Cloud WAF protection.
DDoS
Distributed Denial of Service (DDoS) causes the victim’s server to become unavailable for as long as the attack prevails. DDoS attacks can hit even leading cloud providers like Amazon AWS, as shown in this article.
There are several kinds of DDoS attacks on DNS infrastructure:
Straightforward/Naive DDoS
Using a botnet made up of different endpoints, the attacker sends many DNS requests directly to the victim’s authoritative name server in the same period of time.
This kind of attack, when carried out in large volumes, can flood the DNS server with multiple requests, effectively causing it to become unresponsive, and in turn making it impossible for legitimate clients to resolve the website address.
Mitigation
Filter and rate-limit network traffic by using dedicated hardware-based network appliances or cloud-based solutions.
In a naive DDoS attack, when the attacker doesn’t spoof the source IP, the number of attacking sources is limited. It can, therefore, be mitigated by blocking those IPs.
Source IP Spoofing DDoS
Due to the nature of the UDP protocol, on which DNS relies on by default, the source IP address can be spoofed easily, so every packet can be assigned a random IP address. In these case, blocking IP addresses as a mitigation method becomes useless, and a different approach is required.
Mitigation
Use DNS cache servers to absorb most of the incoming DNS traffic.
Attackers usually use non-existent domain names in their DDoS to ensure the resolver will forward the requests. The chances are that existing domain names are saved in cache and will therefore not be forwarded. For this reason, we recommend implementing the following mitigation in the DNS cache server – limit the rate of forwarding DNS requests whose domain names do not exist in the cache.
If the total number of incoming requests crosses the threshold, require the clients to switch from UDP to TCP. Switching to TCP disables source IP spoofing as a 3-way handshake is required.
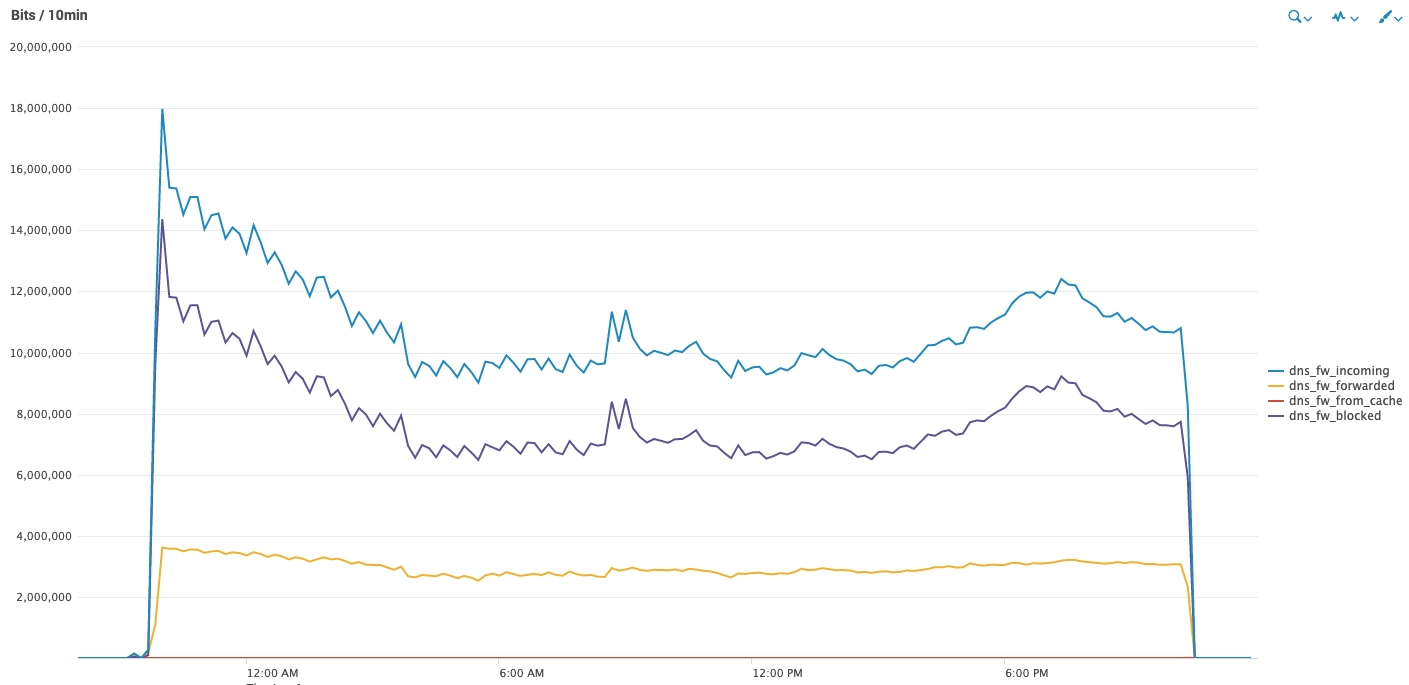
The following graph shows a DDoS attack on an authoritative DNS server protected by Imperva:
This attack lasted for 24 hours. Imperva’s DNS proxy mitigated the attack by filtering and rate limiting the requests passing to the server, so the server received only the rate configured. Malicious traffic above this rate limit was blocked.
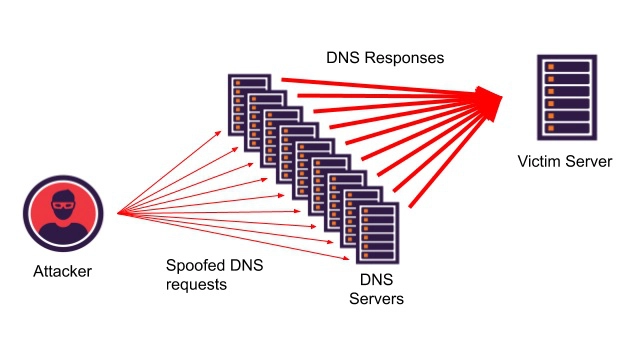
Reflected DDoS
Attackers may spoof not only the source IP address but also the destination IP, so that the DNS response from the legitimate DNS resolver will be sent back to the victim (the spoofed IP) and not to the original attacker’s IP, thus causing a DDoS on the victim.
This attack method amplifies the DDoS effect – the attacker crafts DNS requests that trigger larger DNS responses (for example “ANY” type requests or requests with multiple DNS records will trigger larger DNS responses), thus causing the amplification effect.
In this scenario, legitimate DNS servers take an active role in the attack.
Mitigation
Limit the rate of DNS requests/responses with the same source IP address.
Because DNS resolvers use a cache, their request forwarding rate is supposed to be very low, so a reasonable rate limit should be effective.
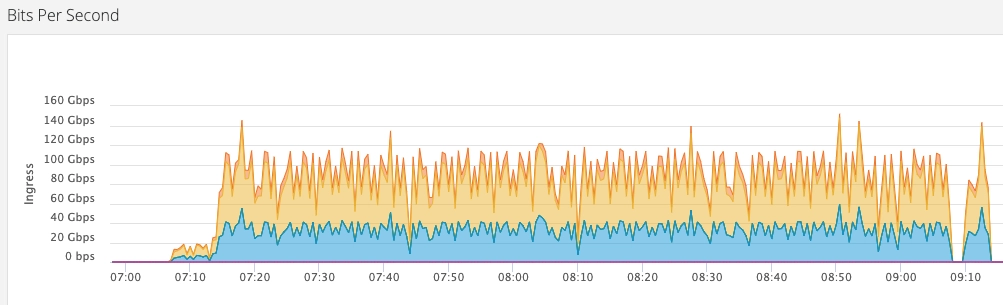
The following graph shows a serious combined DDoS attack on a customer’s infrastructure protected by Imperva:
In this DDoS the attacker combined two different methods:
- A reflected and amplified DNS DDoS attack – 70 Gbps of DNS response packets – the orange color.
- A spoofed UDP DDoS attack – 30 Gbps of UDP packets – the blue color.
Combined, the attacker achieved a 100 Gbps DDoS attack on the target.
In this attack the average size of the DNS response packets was 1,400 bytes, which enables an amplification factor of x20. So, by utilizing 3.5 Gbps BW of DNS requests, the attacker managed to amplify it up to 70 Gbps of DNS reflected DDoS. This attack was automatically mitigated by Imperva’s L3/4 DDoS protection.
The reflection attacking method is very common and powerful. The most attacked customer in the last 10 months, in terms of total attack time, spent 10.7 percent of that time under DNS DDoS attack but continued to function and serve its clients without disruption.
Cache Poisoning
Unlike DDoS attacks that aim to clog the DNS server, the goal of a cache poisoning attack is to redirect users from the real site to a malicious website.
Attack stages
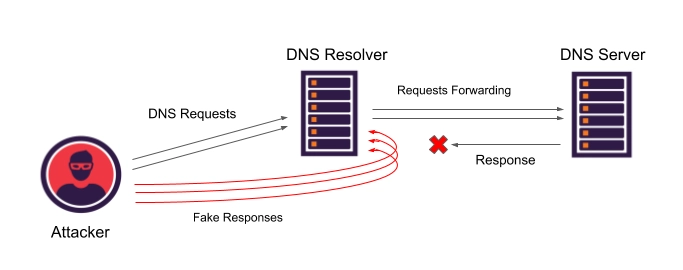
- The attacker sends DNS queries to the DNS resolver which forwards the requests to a Root / TLD / Authoritative DNS server and waits for the answer.
- The attacker “bombards” the DNS resolver with poisoned responses that contain the IP address of the malicious website. For the attacker’s response to be accepted by the DNS resolver, the attacker needs to match the right port number and the ‘query id’ field before the authoritative DNS response. The attacker can brute-force responses to increase his chances of success.
- Any legitimate user that queries this DNS resolver will get a poisoned response from the cache and will be redirected to the malicious website.
Mitigation
- Implement and use DNSSEC. DNSSEC prevents this threat by providing signed DNS responses. A DNS resolver that implements DNSSEC validates the signed responses it gets from Root, Top Level Domain and Authoritative DNS servers.
- Implement best practices that make it much harder for the attacker to succeed:
- Use a random query ID in each request.
- Use a random source port in each request.
- Discard duplicate forwarding requests.
- Ensure all relevant fields in the response match the request fields exactly – query ID, name, class, and type.
For a detailed list, see the following article.
At the time of writing, Imperva is developing a “Managed DNS service” with DNSSEC support to address this kind of threat.
Conclusion
To ensure the basic functioning of a website, you should ensure the DNS service functions properly and protect it from the kinds of attacks detailed above.
Imperva addresses these threats and offers several relevant protection services:
- ‘DNS Protection’ service to protect authoritative DNS.
- L3 DDoS protection service to protect network infrastructures.
Try Imperva for Free
Protect your business for 30 days on Imperva.