Recently, edge services product manager David Elmaleh and Imperva Research Labs’ data scientist Johnathan Azaria shared their DDoS knowledge in a live BrightTalk webinar about the current threat landscape and what you need to do to ensure you are adequately prepared.
David and Johnathan not only covered data highlighted in our 2019 Global DDoS Threat Landscape Report, but also offered up a never-before-seen look at attacks on a per-industry basis and commentary on how to think about DDoS during the COVID-19 pandemic. Plus, they provided additional insights on why the attacks of late require a specific mitigation strategy.
A Closer Look at Financial Services and Gaming
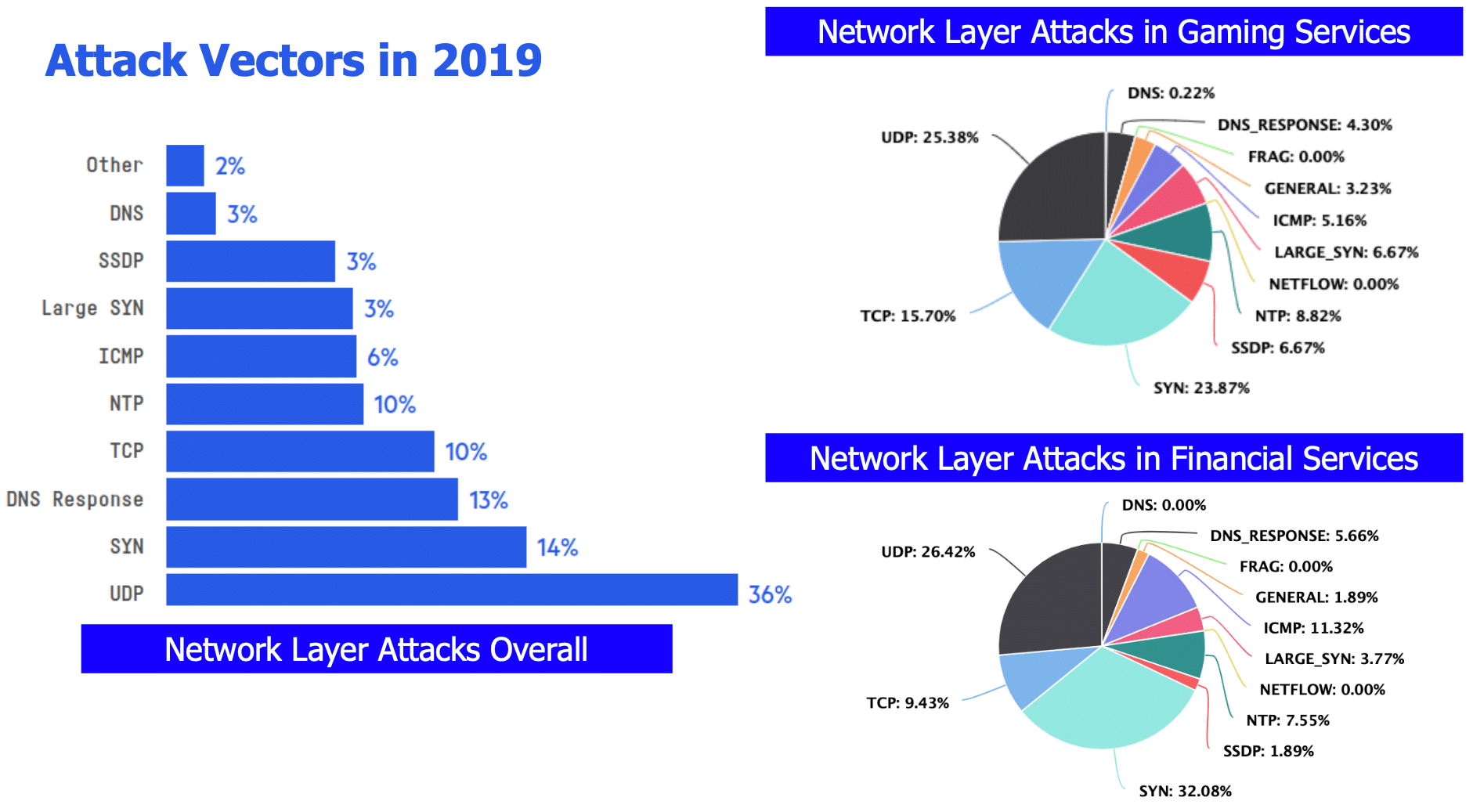
While the report covered the most popular attack vectors over the past year, Johnathan revealed a new look at the attack vector breakdown for network layer DDoS attacks on financial services and gaming.
He explained, “For gaming, UDP attacks came in first place. UDP can be spoofed, and in many cases amplified, which means you don’t need a strong infrastructure to utilize an attack. Next in line are the SYN and ACK floods, that if done correctly, can be pretty difficult to mitigate. The rest of the vectors are amplification vectors like NTP, ICMP and SSDP and other vectors that are known for being used a lot in DDoS attacks and can be mitigated as easily as they’re executed.”
In his analysis of network layer attacks on financial services, after noting that we can see that SYN came in first and UDP second, he warns that “It depends on the way the attackers implement their tool, but SYN can be a serious attack as it requires a strong infrastructure to create a high volume attack, which means that the person who’s behind this is pretty determined.
In contrast, you can see that gaming services have a slightly bigger portion of the simple attack vectors. When you compare gaming and Finance to the overall landscape, it’s easy to see that they’re hit much more by SYN floods.”
DDoS and COVID-19
Johnathan also added more insight from the Imperva Research Labs’ perspective on changing attack patterns related to COVID-19
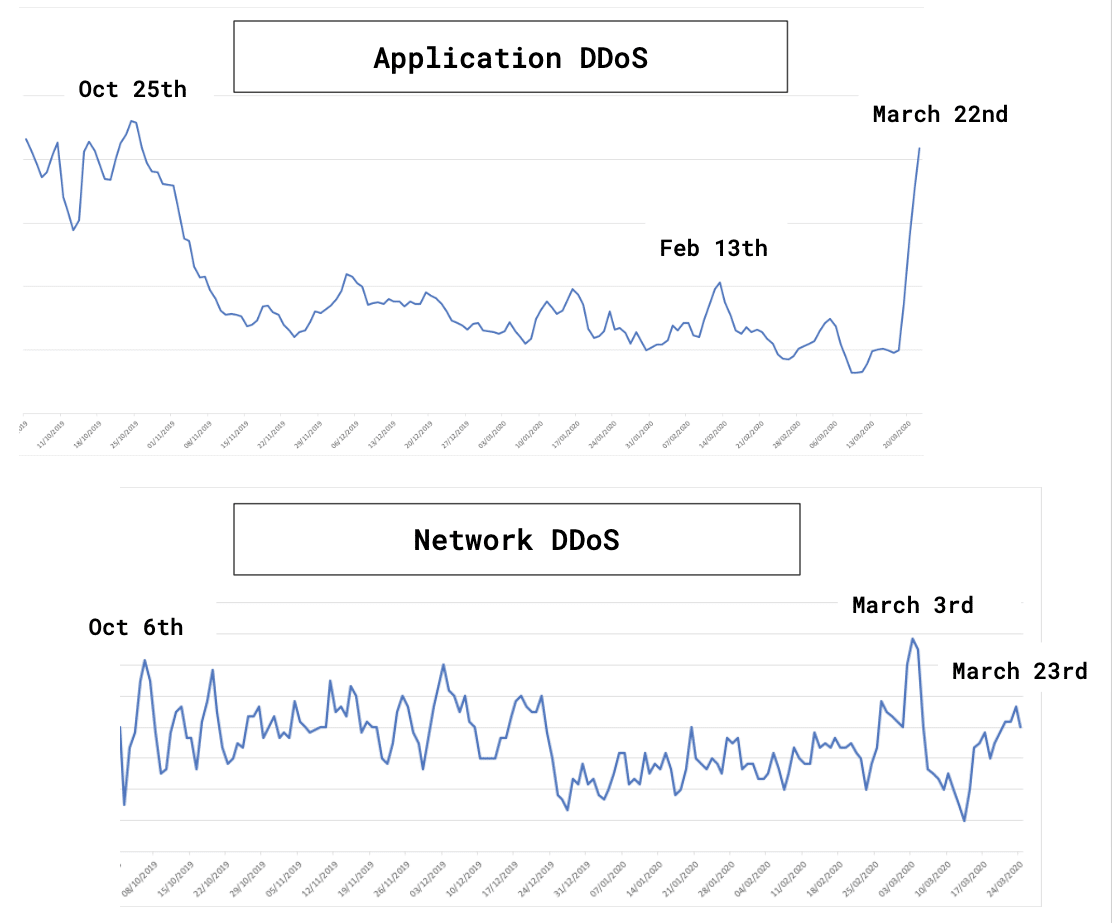
Noted Johnathan, “DDoS attacks have made a very recent comeback after dropping off temporarily. Even hackers have to take some time to adjust to working from home.”
He continued, “With that being said, changes in traffic patterns means it’s even more important to be able to distinguish between a legitimate increase in traffic and attack traffic, or to distinguish between a legitimate shift in traffic distribution vs. attackers trying new attack methods. We need to make sure that this change in traffic is a legitimate change.”
In terms of the changes, Johnathan reminded us that in some cases, they’re due to a shift in the services consumed by clients.
However, he explained, “In other cases it will be because of workers working from home. So this means more VPN traffic or a decrease in internal traffic coupled with an increase in external traffic. Workers are now logging in from the outside instead of the inside, which will change the traffic pattern. We saw exactly this case in our network.
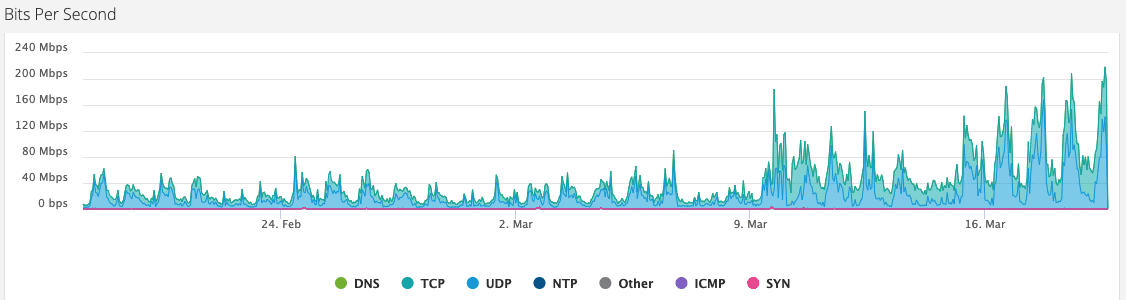
The rise in TCP and UDP traffic is significant and the last thing you want is false positives preventing people from logging in from the outside.”
In addition, Johnathan warns that this is also a new opportunity for attackers to exploit a distracted security team.
He said, “Attackers may be launching more attacks, or using these new vectors in order to piggyback on them, slipping in some kind of an attack. For example, the increase in UDP traffic due to VPN activity might mask a UDP amplification attack, and the increased loggings can mask an account takeover attack.”
Hybrid Solutions Won’t Cut It
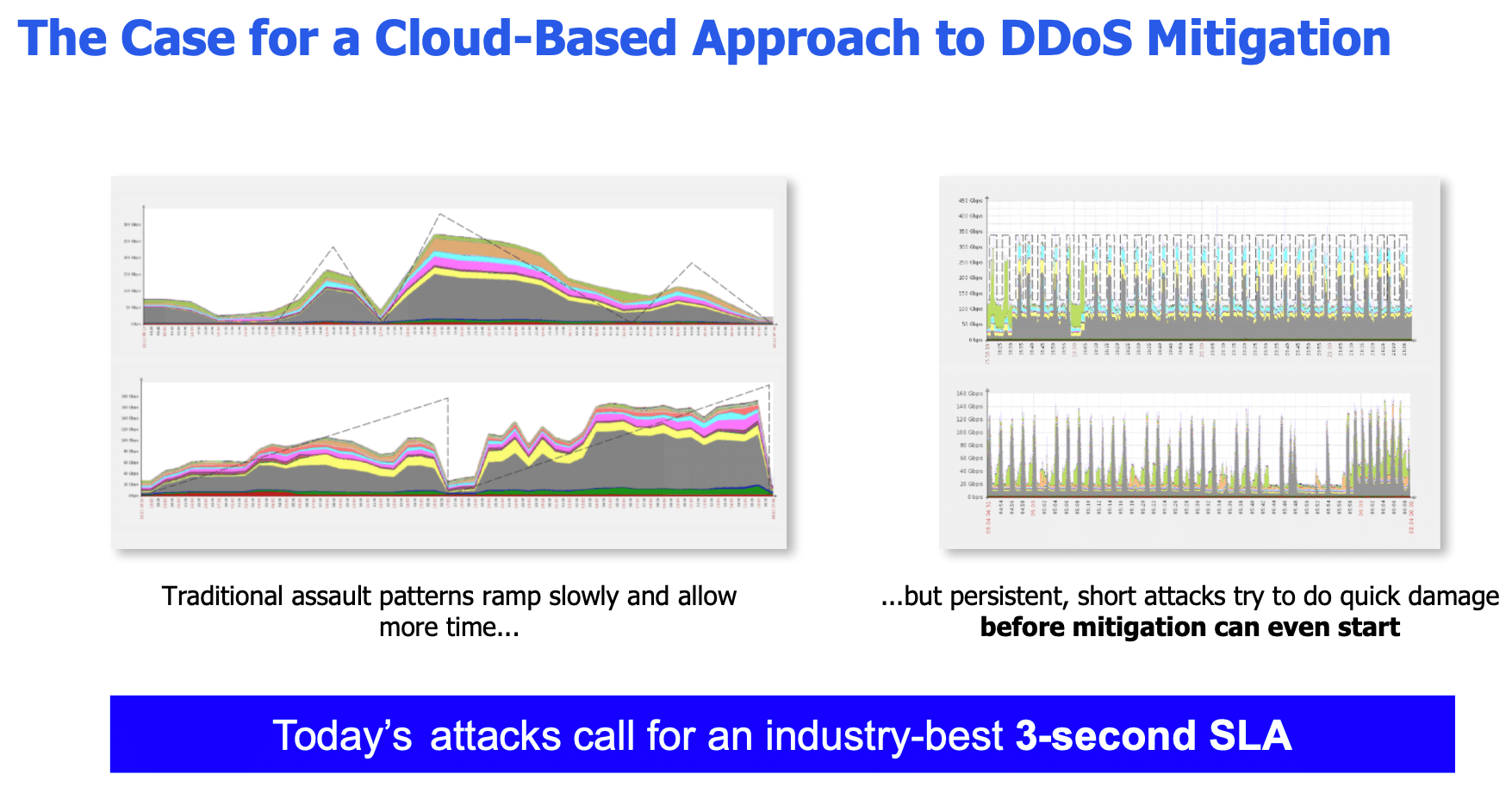
Interestingly, David dug into the research and insights of the DDoS report further by discussing the problem with hybrid DDoS mitigation deployments. They pose an issue when it comes to combating the highly persistent attacks which our researchers found dominate as of late – like the continuance of pulse wave attacks.
Said David: “In a traditional pattern for a DDoS attack, the assault is progressive and there is time for the solution to be able to understand the attack and to start the mitigation. But in a burst attack which is going to launch very high spikes of traffic, the challenge is its capability to congest the pipe very rapidly.”
He further explains, “With an appliance it is a necessity to signal to the cloud to start the mitigation. And since the pipe is congested, there is no possibility to communicate and that’s why the solution becomes ineffective.
Then a pulse wave attack repeats itself. Once recovery occurs, there is another pulse again congesting the pipe and the on-prem appliance can’t communicate with the cloud. So the DDoS attack is very successful and the pipe is completely congested. There’s no possibility for mitigation and you face complete downtime.”
Indeed. A cloud-based approach is the best bet to overcome pipe congestion, and it also doesn’t slow down mitigation by relying on an appliance to signal to the cloud. And a service like Imperva DDoS Protection offers an additional unique benefit in that it consistently blocks any attack – no matter the size or how fast it ramps – in less than one second, guaranteed by a 3-second SLA.
If you’d like to see the entire talk and get more valuable insights from David and Johnathan, check out the full webinar.
Try Imperva for Free
Protect your business for 30 days on Imperva.