Over the last week, Imperva Threat Research observed interesting data points related to CVE-2021-44228. Despite new variants being discovered and patched by our team, we wanted to share five interesting things that we’ve learned from analyzing a subset of our overall global network traffic.
Attacks & Attacked Sites
Since last week, attackers have used a combination of manual and automated tools to target 84,000 sites protected by Imperva Cloud WAF. Across the targeted sites, Imperva Cloud WAF has blocked more than 20 million attacks that were attempting to exploit CVE-2021-44228.
Imperva is proactively reaching out and working closely with customers whose sites are being heavily targeted. Specifically, we have created and delivered attack-related dashboards, reports, and statistics to highly targeted customers.
Classified Clients
One thing many people don’t realize is that we’ve built advanced client classification detection algorithms in our Cloud WAF. We leverage client classification as part of our overall security defense system, and of course share the highlights in our customer dashboards. Client values include things like web browser names (Chrome, Safari, etc.) as well as developer tools (cURL, wget, etc.).
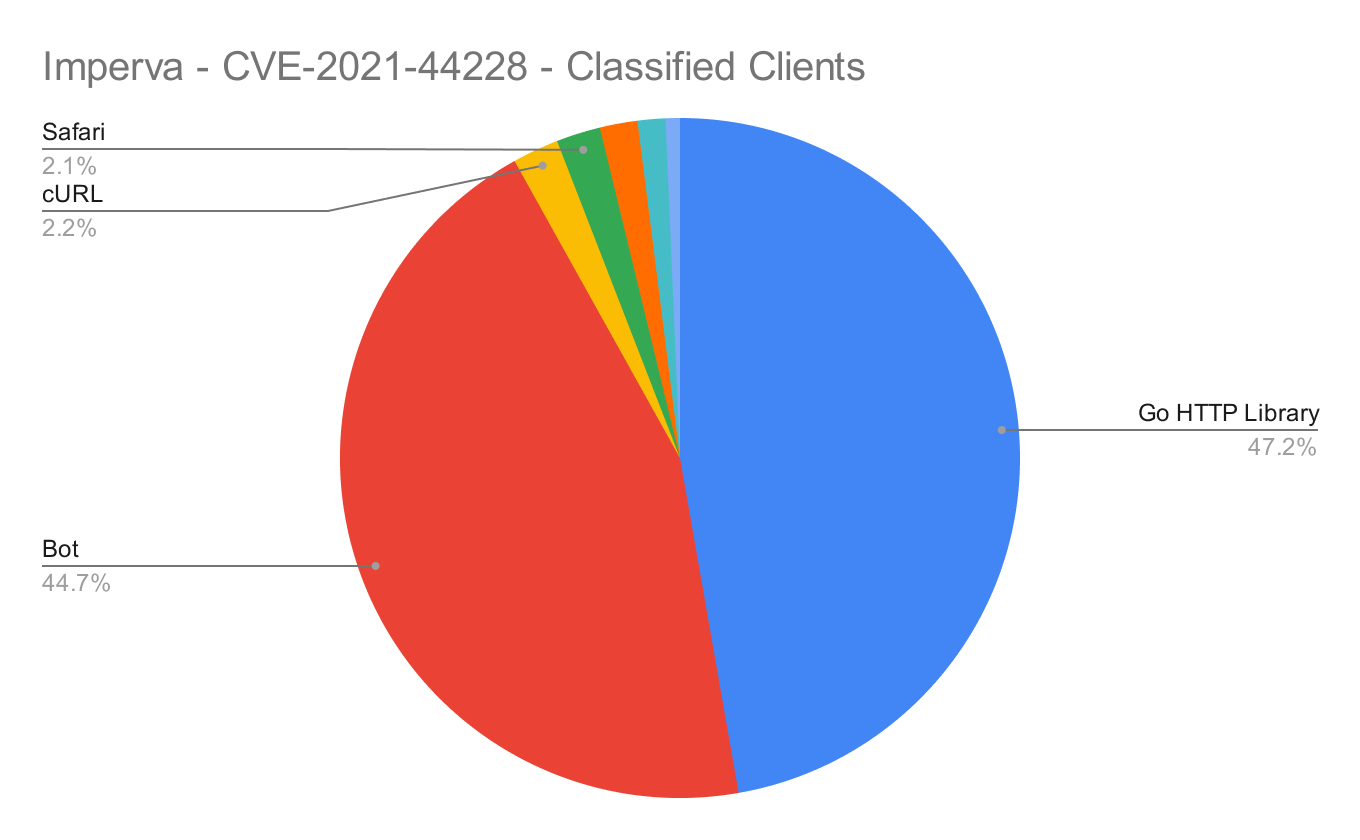
When looking at the overall logs, we found a couple of interesting data points with respect to the clients that generated this attack traffic:
- ~47% of classified clients were developed using the Go programming language. This doesn’t come as a surprise, as the Go language is popular, has a great built-in HTTP client library, and is an easy and highly performant approach for developers to execute concurrent requests (goroutines, channels, etc.). The long tail of clients that we classified were written in Ruby and Python.
- ~45% of classified clients were automated bad bots, and in some cases, are the same bots that have been used previously for attacks like account takeover, scraping, token fraud, etc.
Globally Targeted Industries
The top targeted industries include the following:
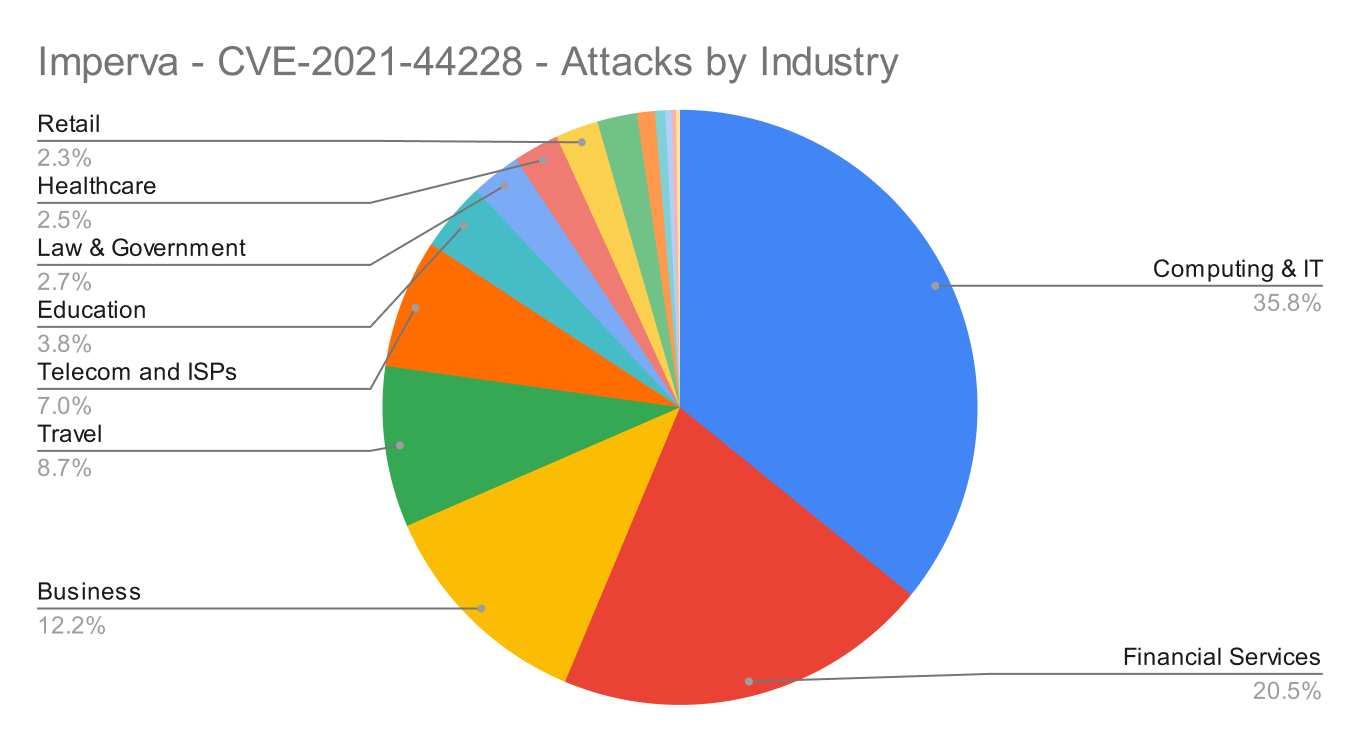
As you can see from the above chart, it appears like a normal distribution across targeted industries.
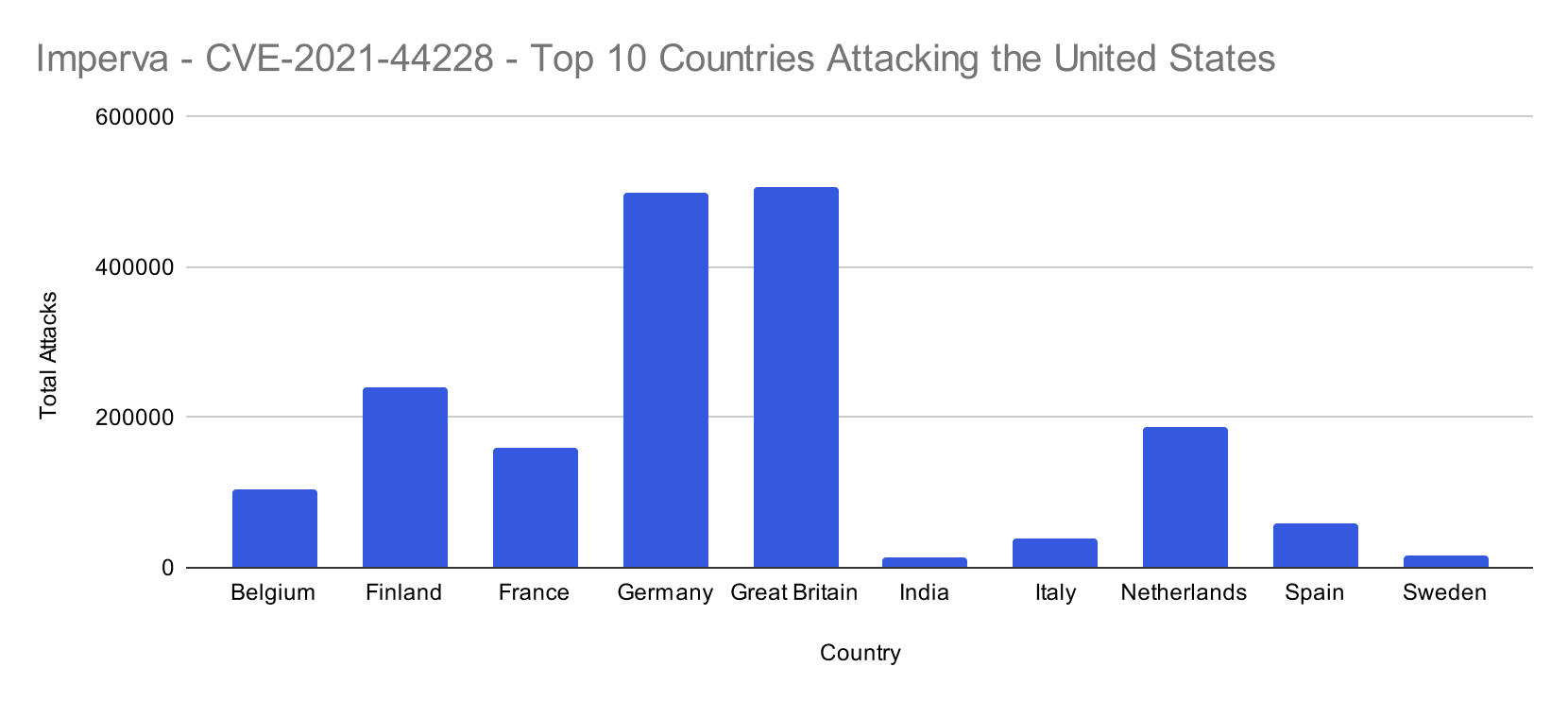
Top 10 Countries Attacking US Customers
When factoring in the attacking country of origin targeting the United States, the data reveals several interesting points.
It gets even more interesting when breaking down the attacking countries targeting industries:
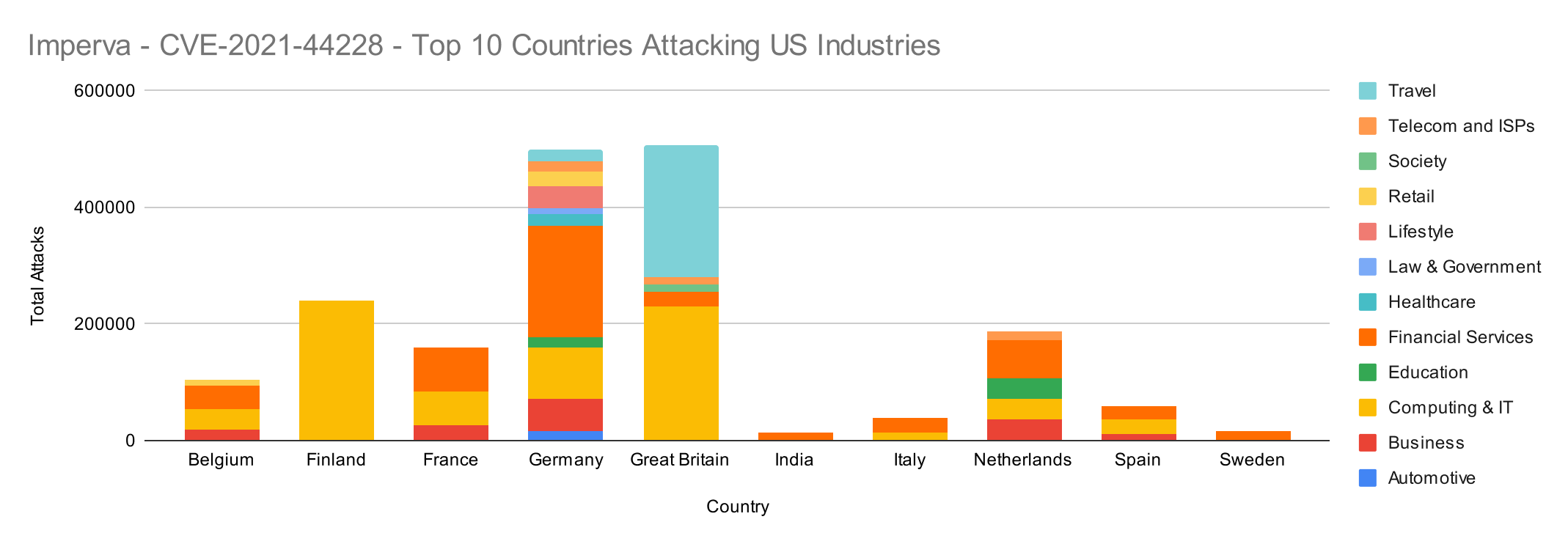
- 9 of the top 10 attacking countries are European. These 9 countries focused on customers in Computing & IT, Financial Services, and Travel.
- Finland was the largest source targeting Computing & IT.
- India was the only non-European country in the top 10 attacking countries list. Attackers in India, like Sweden, exclusively focused on Financial Services.
Imperva Threat Research is currently working on an exciting report around attack variants, how we responded, and even some video demonstrations. We look forward to sharing that report on the Imperva Blog in the coming days.
Learn how Imperva is continuing to stay ahead of CVE-2021-44228. For customers looking for support, please access the Imperva Support Portal. If you’re looking for protection from CVE-2021-44228, please contact us.
Try Imperva for Free
Protect your business for 30 days on Imperva.











