Today Imperva Research Labs, made up of senior researchers and industry experts who have been delivering sound and valid advice for over 15 years, is releasing a brand new Global DDoS Threat Landscape Report. The report is a statistical analysis of 3,643 network layer DDoS attacks throughout 2019 and 42,390 application layer DDoS attacks mitigated by Imperva from May to December 2019.
2019 saw the largest network and application layer attacks ever recorded, with a network layer DDoS attack that reached 580 million packets per second (PPS) in April, and a separate application layer attack which lasted for 13 days and peaked at 292,000 Requests Per Second (RPS).
However, these kinds of large-scale attacks were outside of the norm. Overall, we saw attacks that were smaller, shorter, and more persistent. While this trend may be indicative of attackers’ attempts to wreak havoc before a mitigation service kicks in, it’s no match for Imperva, where time to mitigation is near zero.
In fact, in January of this year, automation technology behind our service detected and immediately mitigated the most significant volumetric network layer DDoS attack (UDP/ICMP floods) that we’ve seen against Imperva’s own corporate websites. It was an assault of 92Gbps and 10.38 Million packets per second (Mpps).
Report Highlights
In terms of targets, the computing and Internet sectors drew the attention of DDoS offenders, ranking as the third most attacked industry segment alongside some of the more regular attack targets.
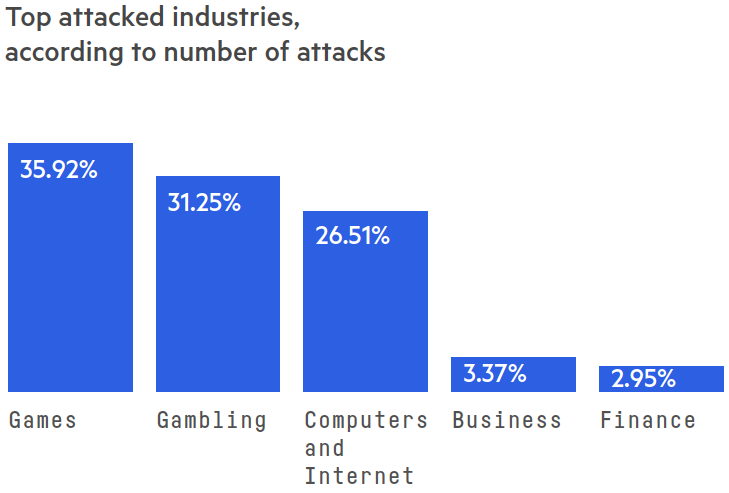
Figure 1: Top attacked industries, by number of network layer attacks
Read the full report >>
Another notable development was the high number of network layer assaults against businesses in the East Asia region, making it the most dangerous region both in terms of the number of attacks and the likelihood of being attacked. The region served as home to the 4 most attacked countries, with India topping the list. Combined, East Asia drew 77.7 percent of all network layer DDoS attacks.
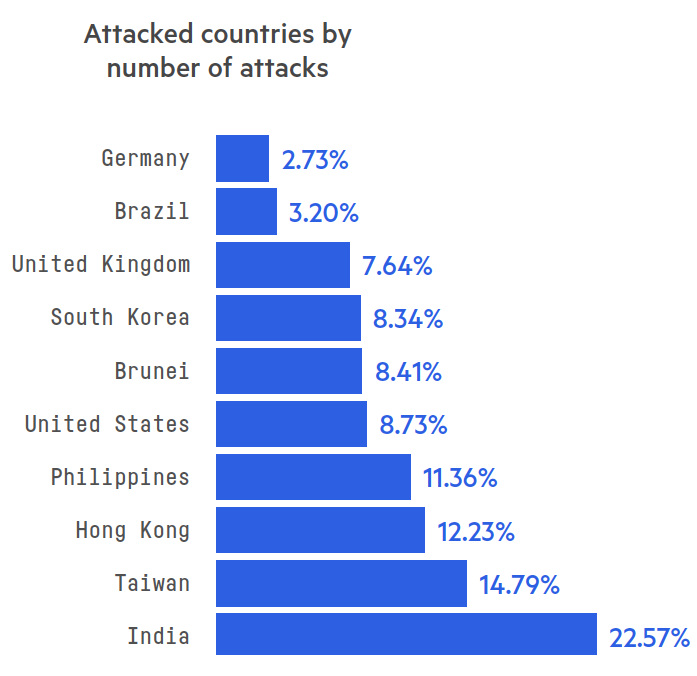
Figure 2: Top attacked countries, by number of network layer attacks
Read the full report >>
For application layer attacks, Ukraine was the biggest target, with more than 20 DDoS incidents per site on average.
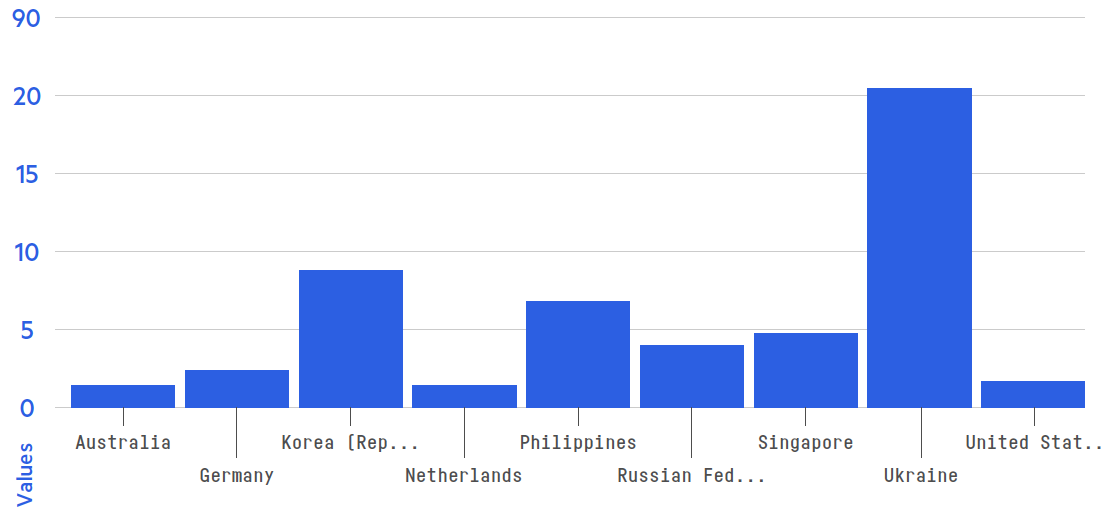
Figure 3: Top attacked countries, by average number of application layer attacks per site
Read the full report >>
In 2019, application layer attack requests overwhelmingly came from the Philippines and China. Those source origination points were notedly the location of the machines used to carry out the attacks, not necessarily the location of the attackers themselves.
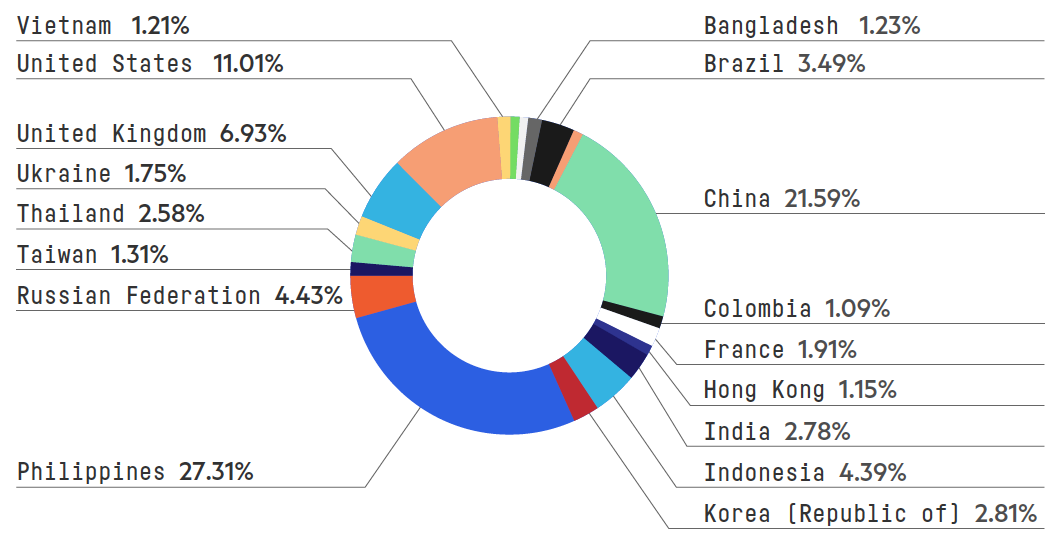
Figure 4: Top attack source countries, by number of application layer attacks
Read the full report >>
While most network attacks were short, with 51% lasting less than 15 minutes, the vast majority were also persistent and aimed at the same targets. Attackers either launched DDoS assaults in short streaks – two-thirds of targets were attacked up to five times – or were ultra-persistent, with a quarter of targets attacked 10 times or more.
We can theorize that the motivation here is attackers aiming to cause as much disruption as possible before their target’s DDoS mitigation service jumped into action. However, we know that this tactic is uniquely ineffective against targets secured by Imperva DDoS protection services, where mitigation against any attack of any size typically takes place in less than one second. It’s also backed by a 3-second mitigation guarantee, under SLA – the industry’s best.
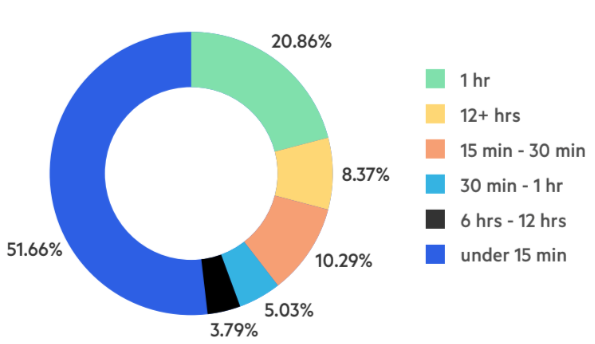
Figure 5: Network layer attacks by duration
Read the full report >>
Try Imperva for Free
Protect your business for 30 days on Imperva.