The WannaCry ransomware attack caught the world off guard—and may have even literally left some crying. The attack infected more than 230,000 computers in 150 countries by encrypting data on networked machines and demanding payments in Bitcoin.
According to Malwarebytes researchers, the attack spread via a process that finds vulnerable public-facing Server Message Block (SMB) ports. It then used the alleged NSA-leaked EternalBlue exploit to access network resources. Then the DoublePulsar exploit (also NSA-alleged) was employed to establish persistence in order to install the WannaCry ransomware itself. Equipment affected included computers, MRI scanners, blood-storage refrigerators and even theater equipment.
Once a computer is breached by WannaCry, the worm contacts central servers to activate file encryption across the network. Once those files are encrypted, it delivers a message to the targeted organization, demanding payment to decrypt the files or else…data destruction or worse. Some of the attacks used timers with increasing payment scales designed to promote urgency.
Deception-based Ransomware Detection Protects Files
When it comes to ransomware, time is of the essence. The best way to prevent an attack like WannaCry is to immediately detect ransomware file access behaviors before the ransomware spreads across the network and encrypts file servers. Once detected, you can quarantine impacted users and workstations.
One approach is to strategically plant hidden decoy files on file system locations throughout the network and then monitor for ransomware behavior on those decoys. Any write/rename actions on the hidden decoy files trigger automatic blocking of the infected user or endpoint. Once decoy behaviors are detected, the user exhibiting the behaviors is blocked, ensuring that legitimate files are walled off from the infection to prevent the spread of an attack.
How to Configure Deception-based Ransomware Protection in Imperva SecureSphere
With Imperva SecureSphere File Firewall, organizations can secure sensitive unstructured data where it resides to prevent breaches, along with their resulting exposure, costs and brand damage.
Configuring deception-based ransomware protection in Imperva SecureSphere File Firewall (V11.5 and above) is a straightforward process. Just follow these 10 steps:
1) In the Main workspace, select Setup > Sites. In the Sites Tree pane, select the server group you want to protect against ransomware. The server group is displayed in a pane next to the Sites Tree
2) In the Definitions tab, verify the IP address of the server you want to protect against ransomware appears in the Protected IP Addresses
3) In the Servers tab, expand the server you want the decoy files planted on and under the Ransomware Protection section, select the Protect from Ransomware check box.

4) In the Sites Tree pane, select the file service associated with the server group you want to protect against ransomware.
5) In the Definitions tab, under the Share Monitoring Definitions section, verify that the share groups you want to protect against ransomware appear under Monitor Specific Shares and the Monitoring check box for each of the share groups is selected.
6) In the Operation tab, expand the Advanced Settings section and select the Monitor system or hidden files check box. Click Save.
7) In the Main workspace, select Policies > Security. In the Policies pane, under the File Custom section, select the File – Ransomware Protection. The policy is displayed in a pane next to the Policies pane.

8) If your MX is configured with multiple IPs:
- In the Match Criteria tab, expand the Source IP Addresses criterion and set the Operation to Exclude all.
- Select User Defined and add all these IPs.
9) In the Apply To tab, select the share groups you want to apply this policy to. Click Save. Deception-based protection is now configured.
10) Verify all is working properly by running the Ransomware Protection job and checking that it finishes successfully.

This protection also prevents many types of other ransomware, not just WannaCry. It protects against legacy attacks as well as future incidents that have yet to materialize. Every type of ransomware strategy, including encryption, file wipeout, and data tampering are covered with SecureSphere File Firewall.
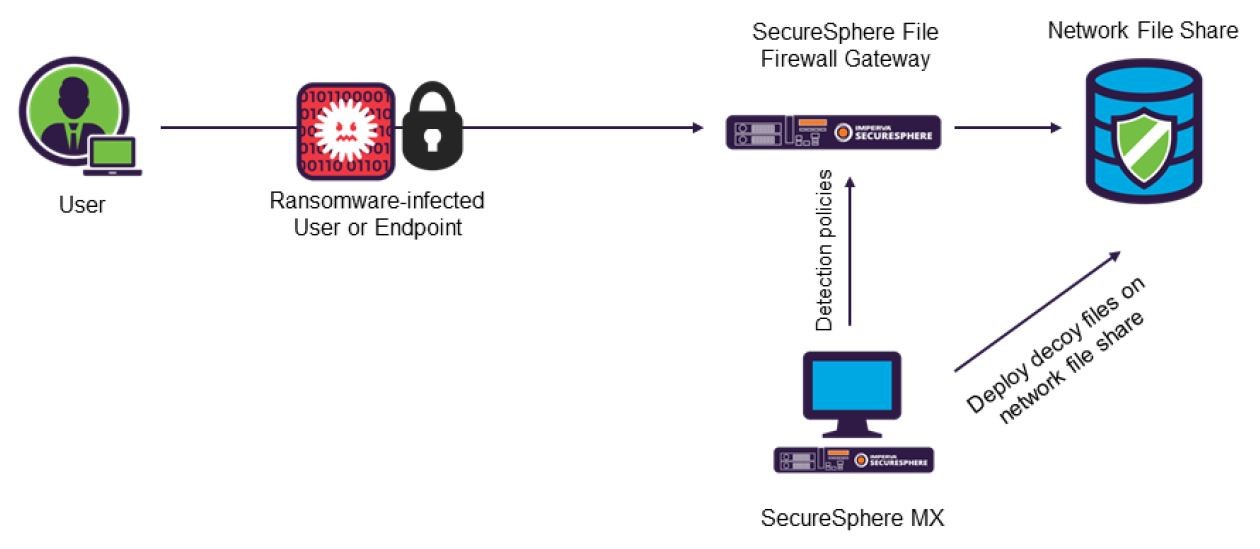
Deception-based method for protecting against ransomware using Imperva SecureSphere.
Policy-based Ransomware Detection
SecureSphere also leverages policy-based detection to identify and block common types of ransomware such as CryptoLocker and CryptoWall, which modify all files found in a drive mount and change their file names.

Based on extensive tests, Imperva found that internal users typically perform no more than five rename operations over a 5-minute time period within a single session. Therefore, it’s recommended to use the following match criteria of 10 or more rename operations within five minutes for a single user. This policy will detect ransomware behavior, block the infected end user from accessing the file share and prevent ransomware from rendering the files unusable across the organization.

What to Expect Moving Forward
Ransomware is not going away anytime soon. Ransomware attacks like WannaCry, CryptoWall, SamSam, Jigsaw, Chimera and CryLocker have proven to be huge money-making machines. Experts anticipate an escalation of this trend, with most new computer viruses and worms following the ransomware model, where extortion follows up the initial breach of data. At the end of the day, malware will also infect the networks which is why it’s important to place security controls around the data.
Learn more about the future of ransomware. And understand ransomware trends, why common security solutions aren’t enough, and how you can protect data at the source in our eBook: “Insider’s Guide to Defeating Ransomware: Protect Your Data at its Source.”
Try Imperva for Free
Protect your business for 30 days on Imperva.




