We (the Imperva Defense Center research team) frequently investigate cases of credential theft to gain a deeper understanding of methods and tools used by cyber criminals—in particular, to learn how accounts are taken over once credentials are compromised through phishing campaigns. We recently chose to deep dive into a specific phishing attack and the person behind it. Along the way, we may have discovered a new meaning to the term, ‘Nigerian prince’ (those notorious advance-fee scams of the 90s). You’ll see what we mean as the story unfolds. Here’s how we tracked down one bad-news hacker.
A Phishing Story
As a part of our research we created multiple fake identities in platforms well-known as phishing targets. We invited attackers in by leaking the credentials of these accounts to selected phishing campaigns and traced the activity of the attackers in the accounts.
Our research began from Gmail credentials we leaked to a Google Docs phishing campaign. Almost immediately after the leak, we received a sign-in alert—indicating that an unknown device accessed our account. According to the account activity log, the connection was made from Lagos, Nigeria.
Following the Lead
A quick review of our mailbox discovered five new messages sent from the account by the anonymous intruder. Most of the messages were phishing messages sent to all contacts of the compromised account, tempting them to visit the domain dropbox-documents.us (Figure 1), which we found to be part of a Dropbox phishing campaign. One message in particular captured our attention as it had a unique title of ‘test’, blank content, and was sent to a single recipient: lvrxdnona@gmail.com.

Figure 1: Dropbox phishing page, dropbox-documents.us
We realized the suspicious address lvrxdnona@gmail.com recurred in most of the messages. At this point, we began to suspect that lvrxdnona was more than just an innocent victim of this campaign and might be related to the person behind the attack. In some cases, the lvrxdnona@gmail.com address wasn’t found, but we noticed another suspicious address, larrysimons12@gmail.com, which we later discovered, was also connected to the attacker.
Following are phishing emails sent from the compromised account (Figures 2 and 3):
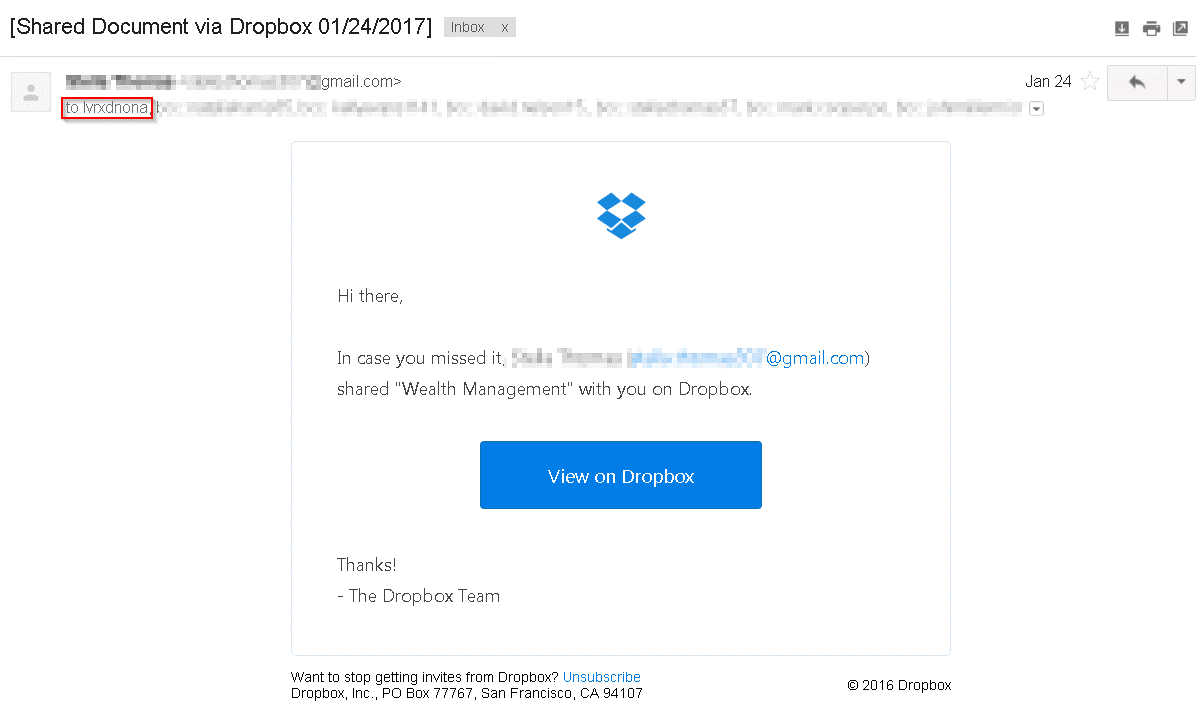
Figure 2: Dropbox phishing email
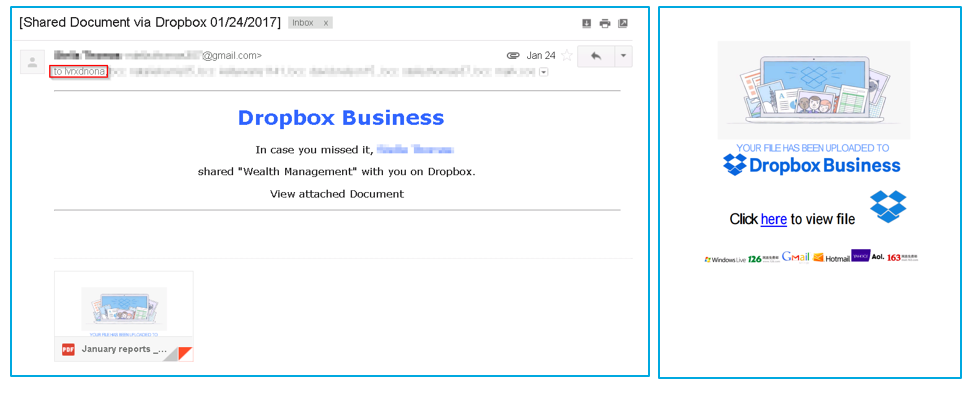
Figure 3: Dropbox phishing email with PDF attachment
Digging into the Phishing Server
With a phishing domain in hand, our next step in the investigation was to search for the owner of the dropbox-documents.us domain. Using the Whois database we found that this domain was registered on November 28, 2016 by someone called Lvrxdnona (sound familiar?) with the contact email address lvrxdnona@yandex.com, via domain reseller Namecheap on a server located in Los Angeles, California (USA).
In the search, we found another suspicious domain, dropbox-business.us, also registered to Lvrxdnona, but at the time of our investigation, that domain was unavailable.
Investigation of Lvrxdnona’s server provided some interesting insights and exposed several hacking and phishing resources. In addition to phishing landing pages for Excel Online, OneDrive and Google Docs, we also found several do-it-yourself (DIY) deployments kits for these campaigns (Figure 4).

Figure 4: Directory listing on Lvrxdnona’s server
Following is a screenshot of the Microsoft Excel Online landing page we found on the server (Figure 5):

Figure 5: Microsoft Excel Online phishing page
As we already suspected, we found the lvrxdnona@gmail.com address as the recipient for emails containing the victims’ details hardcoded in the backend PHP files within the phishing deployment kits (Figure 6). This confirmed our suspicion that the attacker added their email address to the phishing messages as a call-home feature, probably to receive confirmation that the messages were indeed delivered, and to keep record of the phishing activity.

Figure 6: lvrxdnona@gmail.com address hardcoded in the backend PHP files within the Excel Online phishing deployment kit
The signature lvrxdnona was found in additional modules, but this time in conjunction with Skype nickname lvrxdnona and ICQ number (Figure 7):

Figure 7: lvrxdnona’s Skype contact information
In addition to DIY phishing kits, we also found a DIY botnet kit (/botnet/Panel.zip) for set up and management of a botnet infrastructure. Most likely that botnet serves its owner as the primary distribution vector for as many phishing campaigns as possible. The number, complexity and ease of use of the DIY kits we found suggest once again that the DIY phishing trend plays a major role in the recent increase of phishing threats.
Digging Deeper: Pony Password Stealer
Further investigation of files on the server revealed a Pony 1.9 HTTP Password Stealer infrastructure containing an admin panel, control and configuration PHP scripts, and Pony Builder, which takes a configuration file and builds the actual malware file to be executed on a victim’s machine. Upon execution, Pony collects passwords stored on the victim’s machine, sends them to the cyber criminals, and then downloads another piece of malware.
The following is a directory listing of Pony infrastructure (Figure 8):

Figure 8: Pony deployment kit found on the server
Digging into configuration files revealed the admin-panel username and password. We were able to access the Pony admin dashboard and see victims’ information (Figure 9):

Figure 9: Pony admin dashboard
Once we looked at the time stamps of collected credentials and uploaded time stamps of Pony deployment kits we detected the exact timeframe of this Pony campaign. It’s a relatively new campaign carried out during the first couple of weeks of February 2017 (Figure 10).

Figure 10: Victims’ stolen credentials
Furthermore, in another directory on this server we found a malicious executable, crypted.exe, which likely would be downloaded and loaded to victims’ machines by Pony. This malware is a remote access Trojan (RAT) that leverages an aggressive keylogger, as well as several other malicious features, that allows an attacker to gain full control over a victim’s machine.
Who are you lvrxdnona?
We were curious to know who lvrxdnona is, so we searched for this signature on Google and found several mentions in hackers’ underground forums, anti-spam lists and social networks.
We discovered that the young man is not so beloved in the hacker community; he was banned by other users in several forums and classified as a Bot\Scammer – Fake Sale Threads Poster (Figures 11 and 12).

Figure 11: lvrxdnona banned by another user from Bit’s Hack forum

Figure 12: lvrxdnona banned from the Nulled cracking community
We found lvrxdnona in the Nigerian Best Forum (NBF), which is the biggest Nigerian online community, where he appeared as a 28-year-old student from Lagos (Figure 13).

Figure 13: Nigerian Best Forum (NBF)
Lvrxdnona has a wide range of dubious interests. He published an attractive Money Making Tutorial 2016 on the eMoneySpace forum, which promises participants a profit of $100-200 per day (Figure 14).

Figure 14: Money Making Tutorial 2016 on eMoneySpace
We noticed lvrxdnona is also an active member of carding forum (carding.com) and Leak Forums (leakforums.net). On Leak Forums lvrxdnona sells the Citadel Atmos botnet and builder “at good price” and mentions the same ICQ number we saw inside the phishing deployment kit (Figure 15):

Figure 15: Citadel Atmos botnet (Banking Trojan) for sale
Moreover, lvrxdnona was found in a list of Nigerian spammers on www.stopforumspam.com (Figure 16). It is important to note that the lvrxdnona signature appears in the list along with the email address larrysimons12@gmail.com, which appeared as a recipient in one of the phishing emails we received.

Figure 16: Stopforumspam.com Nigerian spammers list
Finally, we found lvrxdnona in social networks such as Snapchat, Instagram, INK361, Twitter and Facebook.
Cyber-Sleuth Summary
While the cybercrime world is mostly comprised of organized groups operating in an industrial fashion, there are still individual entrepreneurs like lvrxdnona (perhaps today’s new ‘Nigerian prince’). This is attributed to the low cost, simplicity of operation, and availability of servers and DIY kits. This story certainly proves that financial motivation is a key factor in cybercrime for players big and small and that increased cyber-criminal activity is a real threat to individuals and enterprises. Our story also shows that with some effort and a little detective work the people behind cyber-criminal operations can be tracked.
Try Imperva for Free
Protect your business for 30 days on Imperva.