What is Cloud Security?
Cloud computing security is a set of technologies and strategies that can help your organization protect cloud-based data, applications, and infrastructure, and comply with standards and regulations.
Identity management, privacy, and access control are especially important for cloud security because cloud systems are typically shared and Internet-facing resources. As more and more organizations use cloud computing and public cloud providers for their daily operations, they must prioritize appropriate security measures to address areas of vulnerability.
Cloud computing security processes must take into account the security controls offered by cloud providers, and organizations must understand the division of responsibility between the cloud provider and cloud user. To prepare for the event of a cloud security breach, there should be standardized processes for business continuity and data backup of cloud systems.
Cloud Security Statistics
The driving force behind the adoption of secure cloud practices is the increasing threat from cybercriminals targeting the cloud. The ISC(2) Cloud Security Report found that 28% of enterprises experienced cloud security incidents. The UK government also reports that 32% of UK companies experienced attacks on cloud systems.
The Check Point 2020 Cloud Security Report provides additional findings:
- The biggest threat cited by respondents is cloud platform configuration error (68%), followed by unauthorized cloud access (58%), unsecured interfaces (52%), and account theft (50%).
- 55% of respondents said the lack of qualified talent, including security talent, was the biggest barrier to cloud adoption
- 82% said existing security solutions do not work at all or offer limited functionality in a cloud environment
Examples of Cloud Security Breaches
In order to understand how security breaches occur, it is instructive to see real-life examples of breaches. Here are three recent examples of security breaches that originated from cloud services, which illustrate the extent and severity of cloud system vulnerabilities.
Capital One
Capital One is the 10th largest US bank in terms of assets. Its cloud infrastructure was based on Amazon Web Services (AWS).
The following events led to the publicized breach at Capital One. First, a web application firewall (WAF) was configured incorrectly. The attacker used the misconfigured WAF to generate an access token and used the access token to fetch data from AWS storage. 700 folders and data packages containing customer information were copied to an external location.
Attackers were aware of special AWS commands and used them to perform lateral movement once they gained access. Even more concerning, the breach did not raise any alerts, and even the data transfer outside the organization’s network was carried out under the guise of normal network traffic.
Docker Hub
Docker Hub, a popular repository of container images, was compromised and 190,000 accounts were exposed, hurting container technology adopters. In a statement posted on the Docker website, the company disclosed that they discovered unauthorized access to a single central database that stores non-financial user data.
Although this vulnerability affected only 5% of Docker Hub customers, the data exposed included tokens and access keys used in the auto-build features of code repositories. This allows the attackers to bypass authentication and inject malicious code into many companies’ production pipelines, and obtain copies of proprietary code.
Autoclerk
Autoclerk, a global hotel reservation management system, had an AWS-hosted Elasticsearch database that was unsecured and exposed hundreds of thousands of bookings. The system was heavily used by military personnel, and the breach revealed sensitive information about military travel, including senior officials and deployed troops.
Security researchers from vpnMentor publicized the breach, saying that they saw publicly accessible logs of US generals traveling to Moscow, Tel Aviv, and many other destinations. They also found email addresses, phone numbers, and other sensitive personal data belonging to travelers.
Cloud Security Challenges
Below are some of the key challenges making it more difficult to secure cloud systems, compared to a traditional security perimeter.
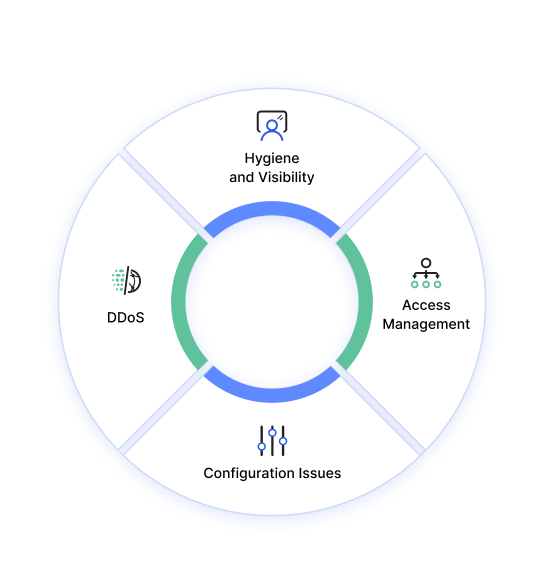
Cloud security challenges
Access Management
The cloud enables access to corporate data from anywhere, so companies need to make sure unauthorized parties cannot access that data. This can be achieved through a variety of strategies, including cloud-based data loss prevention (DLP) solutions, monitoring, and careful use and maintenance of identity and access management (IAM) systems.
Compliance Violations
As regulatory controls around the world become more stringent, organizations must adhere to numerous compliance standards. By migrating to the cloud, you may be in violation of your compliance obligations.
Most regulations and compliance standards require businesses to know where data is located, who can access it, and how it is managed and processed, which can all be challenging in a cloud environment. Other regulations require that cloud providers are certified for the relevant compliance standard.
Denial of Service (DoS/DDoS attacks)
Distributed Denial of Service (DDoS) attacks are designed to stream large amounts of traffic to a web server or other critical system, preventing it from responding to legitimate requests.
Cloud computing is based on shared distributed computing resources and uses different types of virtualization technologies, making DDoS more complex and difficult to detect and prevent.
For example, new types of DDoS attacks involve attackers overwhelming virtualization resources like hypervisors; hijacking virtualization management systems to create new compromised VMs, and compromising migration and backup systems to create unneeded copies of production systems.
Unsecured APIs
Application program user interfaces (API) are the most common way to operate and integrate cloud systems.
APIs can be used internally by company employees and externally by customers, via mobile or web applications. APIs can provide many types of data, including sensitive data that can be valuable to attackers. Because APIs are publicly available and their inner workings are well documented, they are a prime target for attackers.
Cloud Security Best Practices
Follow these best practices to improve security for business-critical cloud-based systems.
Ensure Hygiene and Visibility
Cloud environments are characterized by many moving parts, including short-lived cloud instances and containers, elastic data volumes, cluster-based assets (like data warehouses), and serverless functions.
Use an automated method to compile an inventory of all current and historical cloud assets, to prevent chaotic growth and control your attack surface. If assets are invisible, you cannot protect them. So being able to quickly and reliably see the assets you own, the user accounts they are exposed to, and events taking place on each asset is the first step to creating a security perimeter.
Prevent Data Loss by Setting Up Backup and Recovery Solutions
Data moves fast in the cloud. Because systems are highly interconnected, a single error or malicious command can delete large amounts of data or destroy entire data volumes. A compromised account, or an account held by a malicious insider, can quickly elevate privileges and cause catastrophic damage.
Compared to local systems, in the cloud ransomware spreads faster and does more damage, while local systems are more isolated and have clear security boundaries.
You can avoid data loss by configuring the following solutions:
- Backup—use cloud-based backup systems to protect redundant copies of your data in different physical locations.
- Archival—archiving is ideal for large amounts of data that do not need to be used frequently, and can also be isolated from production workloads.
- Recovery—set up automated disaster recovery, with orchestration enabling fast recovery of entire environments, to recover quickly from data breaches.
Keep your Services Up to Date
Ensure cloud systems are not exposed to vulnerabilities due to required updates or patches. This is especially important if there are known vulnerabilities that have not been resolved. In this case, the attacker knows exactly what vulnerabilities exist on your systems and how to exploit them.
In some systems, you may only need to accept updates and patches. In other cases, you will have to create your own patch to resolve a specific vulnerability. Use automated tools to continuously verify that all software systems are running the latest version.
Additionally, use threat intelligence platforms or open-source data like vulnerability databases, to ensure you don’t miss vulnerability announcements. This allows you to protect yourself as soon as a vulnerability is announced, even if a patch is not immediately available.
Audit and Optimize Configurations
When configuring your application and infrastructure, never assume you have configured it correctly. There may be configuration errors, and even if there aren’t, a configuration can change as applications and cloud resources are updated, and as workflows or users change.
Regular review of cloud configurations will ensure that no accidental changes have occurred and that any changes are safe. It also helps to identify less secure configurations, improve performance, and reduce the cost of unneeded cloud resources.
You can perform these audits using a variety of tools and processes, including automated scanners, penetration testing, and manual audits. All major cloud services offer some form of configuration analysis service. A new category of tools called cloud security posture management (CSPM) provide holistic testing and analysis of security vulnerabilities, including configuration issues, across a cloud stack.
Cloud Security with Imperva
Imperva provides a cloud security solution that protects applications, APIs, and Databases on Amazon Web Services, Microsoft Azure, and Google Cloud, with one pane of glass for application and data security. It is provided in two deployment options: security solutions as a service, or self-managed VMs.
Key features of Imperva cloud security:
- Protects cloud workloads – stops web applications, and API attacks that can lead to data theft, mitigates DDoS attacks without disrupting user workflows.
- Ensures compliance – helps meet PCI, GDPR, SOX, and other compliance standards in a complex cloud environment. Supports compliance with a combination of network edge security (WAF), application security (RASP), and data security (DAM).
- Mitigates risk – tracks access to data and applications, as well as data activity by cloud administrators, DBAs, and users, across applications and microservices. Provides split-second response against threats to protected data.
- Accelerate digital transformation – provides a simple way to deploy Imperva security products and services across a multi-cloud environment.




