What is WannaCry Ransomware
WannaCry is ransomware that spreads itself by exploiting a vulnerability in the Windows Server Message Block (SMB) protocol. The SMB protocol enables communication between Windows machines on a network, and Microsoft’s implementation could be tricked by specially crafted packets into executing an attacker’s code.
WannaCry has four components:
- The DoublePulsar dropper, a self-contained program that extracts the other components
- An application that encrypts and decrypts information
- Documents containing encryption keys
- A copy of Tor, an open source software program enabling anonymous communication
The kill switch
Even if a PC is infected, WannaCry does not necessarily begin encrypting documents. It first tries to access a long, gibberish URL. In case it can access that domain, WannaCry shuts itself down. This is known as the WannaCry “kill switch”.
Some investigators believe this functionality is a way for the malware creators to abort a WannaCry attack. Others think it’s an attempt to stop researchers from running the malware and assessing it in a “sandbox” environment. Whatever the reason, the kill switch was used by the authorities to slow down the spread of WannaCry.
WannaCry Attack Examples
WannaCry Ransomware exploded in 2017, infecting more than 230,000 computers around the globe and causing damages valued at billions of dollars. Additional waves of the ransomware were seen in 2018. Below are two examples of industry sectors that were badly affected by the attack.
Healthcare organizations
The healthcare sector was adversely affected by WannaCry because of its extensive use of Windows computers, many of them outdated and unpatched. The attack rendered many critical systems unavailable, leading to extreme measures like closure of emergency rooms, and isolation of critical health equipment from the network. Devices like MRIs, which are used for time-sensitive, life-saving customer care and diagnosis, were rendered ineffective.
Large manufacturers
USA-based aircraft maker Boeing utilizes a large number of Windows machines, many using old, vulnerable operating system versions. Boeing was hit by WannaCry in 2018 and announced a company-wide crisis situation, bringing in all company VPs to manage the crisis. At the end WannaCry only affected a few machines and did not cause significant damage.
Rendition Infosec, a security advisor, said to the media that it had confidential information about three other large manufacturers in the USA that were hit by WannaCry attacks, and unlike Boeing, suffered costly production outages.
How Did WannaCry Spread?
WannaCry was spread by EternalBlue, a zero-day exploit that uses an old version of the Server Block Message (SMB) protocol. The exploit is believed to have been discovered by the USA National Security Agency (NSA), and was later obtained by a hacker group called Shadow Brokers. They published the exploit, hidden within a Medium post, on April 8, 2017.
Microsoft had detected the vulnerability a month prior and published a patch, but many systems remained exposed. WannaCry started spreading rapidly on May 12, 2017.
The WannaCry worm uses a transport mechanism that can spread itself, without user intervention, unlike most Ransomware threats that spread by means of social engineering.
The transportat code scans for vulnerable systems and then installs the DoublePulsar dropper, and executes a copy of itself. Researchers discovered WannaCry is able to use DoublePulsar on machines that were previously infected with this dropper, allowing it to spread even more quickly.
Anatomy of a WannaCry Cyber Attack
WannaCry goes through the following steps once it infects a Windows computer:
- When executed, WannaCry checks to determine whether the kill switch domain is available.
- If it is unavailable, the ransomware does not encrypt data on the computer, but still attempts to spread to other computers online and via the local network.
- If available, WannaCry encrypts all data on the machine.
- Victims are asked to pay $300 in Bitcoin within three days or $600 within a week. Security experts advise not to pay the ransom: in most cases, WannaCry attackers do not decrypt the data, and may even have no way to technically do so.
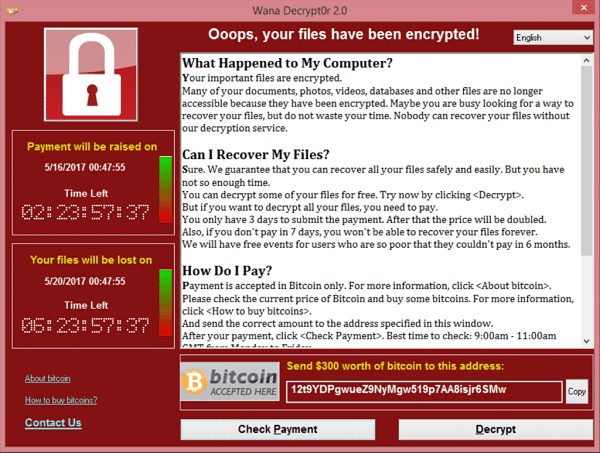
WannaCry ransomware notice displayed after it encrypts files on a machine
- An infected computer looks for devices accepting traffic on TCP ports 135-139 or even 445, indicating that the machine is configured to run SMB.
- It initiates an SMBv1 connection and uses a buffer overflow attack to compromise the system and install the ransomware.
WannaCry Patch
If you run old versions of Microsoft Windows, make sure you have installed security update MS17-010, available at this URL:
https://support.microsoft.com/en-us/help/4023262/how-to-verify-that-ms17-010-is-installed
This security patch protects Windows machines from the EternalBlue vulnerability. It is available for Windows Vista; Windows 7, 8.1, 10; and Windows Server 2008, 2008 R2, 2012, and 2016. Newer versions of Windows and Windows Server are not vulnerable to the attack.
Imperva Data Protection Solutions
Imperva File Security can detect ransomware activity, like a Wannacry attack, before it does widespread damage, using policy-based monitoring and deception technology. Imperva identifies suspicious file access behavior in real time, and quarantines infected users or devices which may be affected by ransomware. It also provides data that can help security teams investigate and report on ransomware activity.
In addition, Imperva Imperva monitors data access and activities of privileged users to identify excessive, inappropriate, and unused privileges.
In addition to ransomware detection and prevention, Imperva’s data security solution protects your data wherever it lives—on premises, in the cloud and in hybrid environments. It also provides security and IT teams with full visibility into how the data is being accessed, used, and moved around the organization.
Our comprehensive approach relies on multiple layers of protection, including:
- Database firewall—blocks SQL injection and other threats, while evaluating for known vulnerabilities.
- Data masking and encryption—obfuscates sensitive data so it would be useless to the bad actor, even if somehow extracted.
- Data loss prevention (DLP)—inspects data in motion, at rest on servers, in cloud storage, or on endpoint devices.
- User behavior analytics—establishes baselines of data access behavior, uses machine learning to detect and alert on abnormal and potentially risky activity.
- Data discovery and classification—reveals the location, volume, and context of data on premises and in the cloud.
- Database activity monitoring—monitors relational databases, data warehouses, big data and mainframes to generate real-time alerts on policy violations.
- Alert prioritization—Imperva uses AI and machine learning technology to look across the stream of security events and prioritize the ones that matter most.