A Proven Record Tracking Cybersecurity Trends
This time of the year is always exciting for us, as we get to take a step back, analyze how we did throughout the year, and look ahead at what the coming year will bring. Taking full advantage of our team’s expertise in data and application security, and mining insights from our global customer base, we’ve decided to take a different approach this time around and focus on three key, and overriding trends we see taking center stage in 2019.
2018 brought with it the proliferation of both data and application security events and, as we predicted, data breaches grew in size and frequency and cloud security took center stage globally. With that in mind, let’s take a look at what next year holds.
(Also, web application firewalls (WAFs) are quickly evolving into the next phase of application security, WAAP, according to Gartner. Read their whitepaper to learn about the merits of WAAP and why your enterprise may need it.)
Data breaches aren’t going away anytime soon, which will bolster regulation and subsequent compliance initiatives
Look, there’ll be breaches, and the result of that is going to be more regulation, and therefore, more compliance, this is a given. In fact, the average cost of a data breach in the US 2018 exceeded $7 million.
Whether it’s GDPR, the Australian Privacy Law, Thailand’s new privacy laws or Turkey’s KVKK; it doesn’t matter where you are, regulation is becoming the standard whether it be a regional, group, or an individual country standard.
Traditionally when we looked at data breaches, the United States lit up the map, but as regulatory frameworks and subsequent compliance measures expand globally, we’re going to see a change.
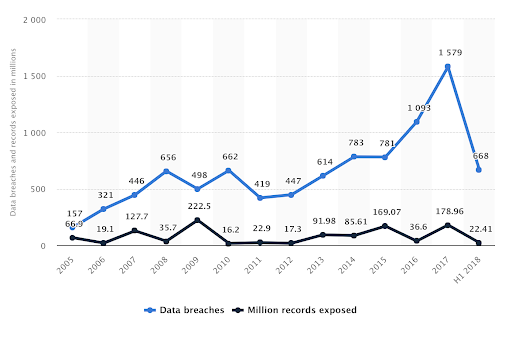
The annual number of data breaches and exposed records in the United States from 2005 to 2018 (in millions) [Statista]
Let’s unpack this for a second. If you were going to steal private data or credit card details, why would you do it in an environment that has world-class, or even mediocre cybersecurity measures in place? If everyone else is even slightly less protected, that’s where you’re going to find people targeting data, but we hear more about it in regions where regulation and compliance is a major focus.
To that end, we don’t necessarily see 2019 as the year where regulators start hitting companies with massive fines for compliance. Maybe by the end of the year, or if you see outright egregious negligence. But, you’ll find that companies have put in the legwork when it comes to compliance.
Having your head in the cloud(s) when it comes to managing risk… not a bad idea
McKinsey reports that, by 2020, organizations will be spending more than six times on cloud-specific products than they do on general IT services; and according to a survey by LogicMonitor, up to 83% of all enterprise workloads will be in the cloud around that same time.
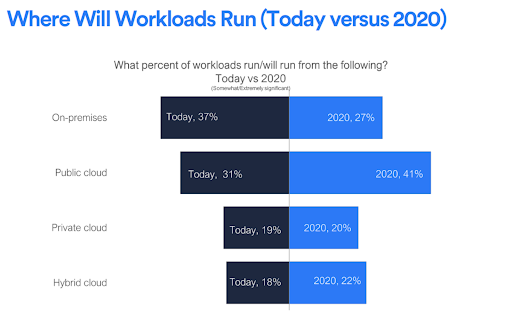
LogicMonitor’s Future of the Cloud Study [Forbes]
Teams need to recognize that, as they transition their data to the cloud, they transition their awareness of what’s in the cloud; who is using it, when they’re using it, and why they’re using it. 2019 isn’t going be the year that businesses figure out they need to do that. What we will see, however, is increasingly cloud-friendly solutions hit the market to solve these challenges.
Social Engineering and the rise of AI and machine learning in meeting staffing issues
One of 2019’s most critical developments will be how the cybersecurity industry steps up to meet the increasing pressure on security teams to perform. According to the Global Information Security Workforce Study, the shortage of cybersecurity professionals will hit 1.8 million by 2022, but at the same time, a report by ESG shows just nine percent of millennials are interested in a career in cybersecurity.
What we’re going to see is how AI and machine learning in cybersecurity technology will close the gaps in both numbers and diversity of skills.
Organizations today have to solve the problem of cybersecurity by hiring for a host of specialized competencies; network security, application security, data security, email security and now, cloud security. Whatever it is, underscore security, those skills are crucial to any organization’s security posture.
Here’s the thing, there aren’t a lot of people that claim to know cloud security, database security, application security, data security, or file security. There just isn’t a lot. We know that and we know businesses are trying to solve that problem, often by doing the same old things they’ve always done, which is the most common solution. Do more antimalware, do more antivirus, do more things that don’t work. In some cases, however, they’re doing things around AI and trying to solve the problem by leveraging technology. The latter will lead to a shift where organizations dive into subscription services.
There are two facets driving this behavior: the first is the fact that, yes, they realize that they are not the experts, but that there are experts out there. Unfortunately, they just don’t work for them, they work for the companies that are offering this as a service.
Secondly, companies are recognizing that there’s an advantage in going to the cloud, because, and this is a major determining factor, it’s an OpEx, not CapEx. The same thing is true of subscription services whether that be in the cloud or on-prem, it doesn’t matter. Driven by skills shortages and cost, 2019 will see an upswing in subscription services, where organizations are actually solving cybersecurity problems for you.
We should add here, however, that as more organizations turn to AI and machine learning-based decision making for their security controls, attackers will try to leverage that to overcome those same defenses.
Special mention: The ‘trickledown effect’ of Cyberwarfare
The fact is, cyber attacks between nations do happen, and it’s a give and take situation. This is the world we live in, these are acceptable types of behavior, quite frankly, right now, that won’t necessarily lead to war these days. But someone still stands to gain.
Specifically, they’re attacking third-party business, contractors and financial institutions. That’s why cybersecurity is so important, there needs to be an awareness that somebody might be stealing your data for monetary gain. It might be somebody stealing your data for political gain too, and protecting that data is just as critical, regardless of who’s taking it.
Now, while state-hacking isn’t necessarily an outright declaration of war these days, it doesn’t end there. The trickledown effect of nation-state hacking is particularly concerning, as sophisticated methods used by various governments eventually find their way into the hands of resourceful cybercriminals, typically interested in attacking businesses and individuals.
Repeat offenders
No cybersecurity hit list would be complete without the things that go bump in the night and, while all of them might not necessarily be ballooning, they’ll always be a thorn in security teams’ sides.
- Following the 2017 Equifax breach, API security made it onto the OWASP Top 10 list and remains there for a good reason. With the expanding use of APIs and challenges in detecting attacks against them, we’ll see attackers continuing to take aim at APIs as a great target for a host of different threats; including brute force attacks, App impersonation, phishing and code injection.
- Bad actors already understand that crypto mining is the shortest path to making a profit, and continue to hone their techniques to compromise machines in the hope of mining crypto-coins or machines that can access and control crypto-wallets.
- Low effort, easy money, full anonymity and potentially huge damage to the victim… what’s not to like when it comes to ransomware? It’s unlikely that we’ll see these types of attacks go away anytime soon.
If there’s one overriding theme we’d like to carry with us into 2019 it’s the concept of general threat intelligence, the idea that it’s better to have some understanding of the dangers out there and to do something, rather than nothing at all.
We often talk about the difference between risk and acceptable risk or reasonable risk, and a lot of companies make the mistake of trying to boil the ocean… trying to solve every single problem they can, ultimately leaving teams feeling overwhelmed and short on budget.
Acceptable risk isn’t, “I lost the data because I wasn’t blocking it. I get it. And it wasn’t a huge amount of data because at least I have some controls in place to prevent somebody from taking a million records, because nobody needs to read a million records. Nobody’s going to read a million records. So, why did I let it happen in the first place?”
Acceptable risk is “I know it happened, I accept that it happened, but it’s a reasonable number of events, it’s a reasonable number of records, because the controls I have in place aren’t so specific, aren’t so granular that they solve the whole problem of risk, but they take me to a world of acceptable risk.”
It’s better to begin today, and begin at the size and relevance that you can, even if that only takes you from high to medium risk, or reasonable to acceptable risk.
Try Imperva for Free
Protect your business for 30 days on Imperva.














